All Insights
Explore security resources, trends and updates, media, podcast episodes, and more
Filter
1324 Results Found
Solutions
Industry
891 - 900 of 1324 results
Published on 12.10.2020
To improve compliance with PCI DSS v4.0, you can implement the CIS Controls and prioritize your implementation efforts using CIS CSAT[…]
CIS ControlsCIS SecureSuite
Published on 12.08.2020
Small and medium organizations can face a variety of IT challenges: insufficient funding, constantly evolving technologies, growing legal and reg...
CIS Controls
Published on 12.07.2020
Small and medium enterprises often face the need to outsource their information technology infrastructure and services. Managed Service Providers...
CIS ControlsTechnology
Published on 12.03.2020
CIS is excited to announce the release of the following CIS Benchmarks. These CIS Benchmark releases would not have been possible without the tim...
CIS BenchmarksCIS SecureSuite
Published on 12.01.2020
Securing your IT infrastructure can be a challenge, especially if you’re working in a regulated environment. To help organizations with this chal...
CIS BenchmarksCIS Hardened Images
Published on 11.30.2020
Each year, billions of internet-connected systems and devices are brought online. This does not include the number of newly-installed systems tha...
CIS Controls
Published on 11.30.2020
We are at a point in cybersecurity where offense must inform defense in order to help protect against the most prolific cyber threats to our envi...
CIS Controls
Published on 11.24.2020
Cloud service providers (CSPs) have changed the way organizations of all sizes architect and deploy their IT environments. CSPs now make it possi...
CIS BenchmarksCIS Hardened Images
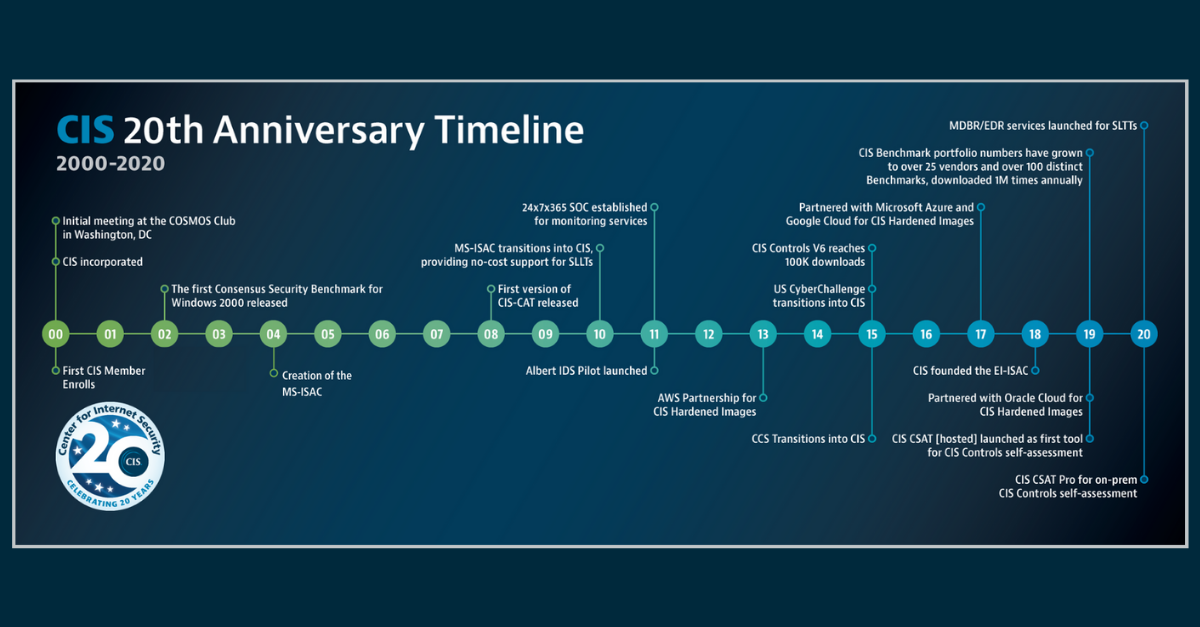
Published on 11.23.2020
This year, the Center for Internet Security (CIS) is celebrating 20 years of making the connected world a safer place for people, businesses, and...
CIS BenchmarksCIS ControlsCIS Hardened ImagesCIS ServicesCIS SecureSuite
Published on 11.20.2020
What it is An After Action Review (AAR) is a retrospective analysis performed after an event. AARs are used by election offices to study and impr...
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More