Blog Posts
Industry news, product updates, videos, infographics, and more from CIS
Filter
631 Results Found
Solutions
Industry
581 - 590 of 631 results
Published on 03.07.2018
CIS Hardened Images are securely configured virtual machines which are now available to spin up in the AWS GovCloud (US) region. AWS customers ca...
CIS Hardened ImagesCIS SecureSuite
Published on 03.06.2018
By Sean Atkinson, Chief Information Security Officer Our normal day-to-day business activities often don’t involve a specific focus on informatio...
CIS Controls
Published on 02.27.2018
By Sean Atkinson, Chief Information Security Officer Asking the question, “Where are my gaps and have I been tested?” The process of managing an ...
CIS Controls
Published on 02.20.2018
It is with great enthusiasm we announce the release of the highly anticipated CIS Microsoft Azure Foundations Benchmark v1.0.0. The development ...
CIS BenchmarksTechnology
Published on 02.13.2018
By Sean Atkinson, Chief Information Security Officer, CIS Using the CIS Controls to define and identify risk The implementation of the CIS Contro...
CIS Controls
Published on 02.07.2018
By Sean Atkinson, Chief Information Security Officer, CIS With 2018 being the “Year of Data Privacy,” organizations in every sector should focus ...
CIS Controls
Published on 02.05.2018
Time is running out for financial institutions in New York State to submit their first certification for 23 NYCRR Part 500. New regulation 23 NYC...
CIS SecureSuite
Published on 01.24.2018
By Sean Atkinson, Chief Information Security Officer, CIS Spectre, Meltdown, and response planning As I start my third week here at CIS, we find ...
Published on 01.12.2018
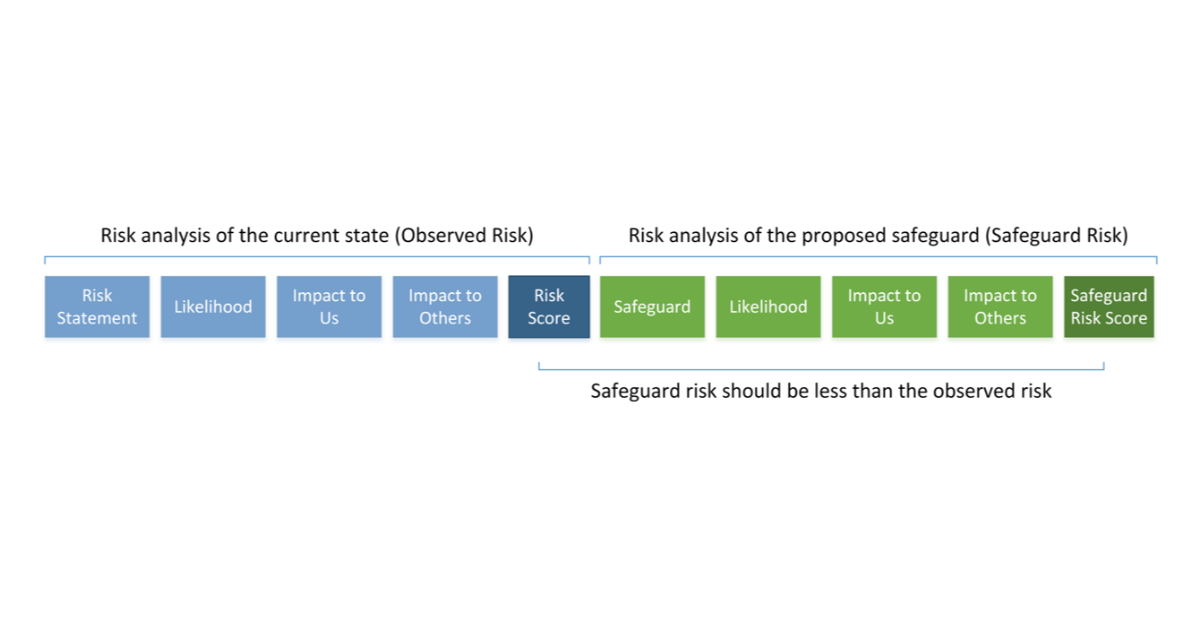
For organizations who are conducting their first cyber risk assessment, it can be challenging to know where to start. CIS RAM (Center for Interne...
Published on 01.02.2018
By Tony Sager, Senior Vice President, and Chief Evangelist Have you ever heard of Security Content Automation Protocols (SCAP)? SCAP is a method ...
CIS Benchmarks
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More