All Insights
Explore security resources, trends and updates, media, podcast episodes, and more
Filter
1324 Results Found
Solutions
Industry
971 - 980 of 1324 results
Published on 05.19.2020
Cybersecurity posters brought to you by the MS-ISAC
MS-ISAC
Published on 05.19.2020
What it is: Cyber threat indicator sharing is the practice of exchanging actionable threat intelligence between organizations. The information sh...
Published on 05.15.2020
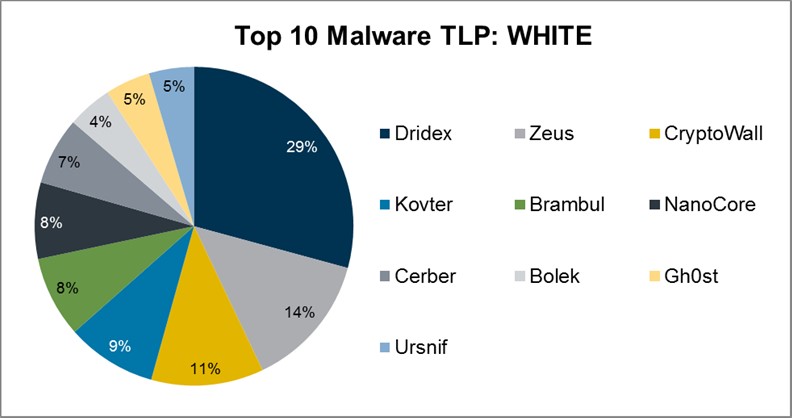
Top 10 Malware composition was fairly consistent with March 2020 with the exception of Bolek and Brambul. Overall, the Top 10 Malware variants co...
MS-ISAC
Published on 05.11.2020
CIS Oracle Database 12c Benchmark v3.0.0 This CIS Benchmark was released with the following improvements: Guidance was added to existing and new ...
CIS BenchmarksTechnology
Published on 05.06.2020
In addition to being costly and troublesome, the continued use of unsupported technologies can expose your organization to security risks. Patchi...
CIS BenchmarksTechnology
Published on 04.30.2020
The CIS Controls offer prioritized and prescriptive guidance on how to achieve an effective cybersecurity program. They are developed through a c...
CIS Controls
Published on 04.28.2020
With a plethora of cybersecurity threats on the horizon, it’s important that professionals have a common language for discussion and analysis. Op...
CIS Benchmarks
Published on 04.20.2020
According to the results of the CSO Pandemic Impact Survey, 61% of the security and IT leader respondents are concerned about an increase in cybe...
CIS BenchmarksCIS ControlsMS-ISAC
Published on 04.16.2020
According to the results of the CSO Pandemic Impact Survey, 61% of the security and IT leader respondents are concerned about an increase in cybe...
CIS ControlsMS-ISAC
Published on 04.16.2020
Top 10 Malware composition was fairly consistent with February 2020 with the exception of Pushdo and Tinba. Overall, the Top 10 Malware variants ...
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More