Showing results 1 - 20 of 37 for "gdpr"
BLOG POST - https://www.cisecurity.org/insights/blog/gdpr-are-you-ready
GDPR – Are you ready?
New regulations like GDPR (General Data Protection Regulation) can always be a bit intimidating – but they don’t have to be! If your organization hand...
BLOG POST - https://www.cisecurity.org/insights/blog/your-gdpr-questions-answered
Your GDPR Questions Answered
The General Data Protection Regulation (GDPR) aims primarily to give control back to EU citizens and residents over their personal data while standard...
BLOG POST - https://www.cisecurity.org/insights/blog/gdpr-a-new-regulation
GDPR – A New Regulation
By Sean Atkinson, Chief Information Security Officer In previous blogs, we deemed 2018 the “year of data privacy.” With privacy in mind, let’s examine...
MEDIA MENTION - https://www.cisecurity.org/about-us/media/media-mention/cso-online-highlights-cis-controls-...
CSO Online Highlights CIS Controls as Resource to Achieve GDPR Compliance
California uses a checklist of security controls created by CIS to ensure that they are following the state's data security compliance laws....
PAGE - https://www.cisecurity.org/privacy-notice/cis-privacy-notice-version-history
CIS Privacy Notice Version History
Privacy Notice Revision History...
BLOG POST - https://www.cisecurity.org/insights/blog/cis-ram-and-use-with-regulatory-frameworks
CIS RAM and Use with Regulatory Frameworks
By Chris Cronin, Partner, HALOCK Security Labs CIS RAM is an information security risk assessment method that helps organizations conduct cyber risk a...
BLOG POST - https://www.cisecurity.org/insights/blog/protecting-privacy-using-the-cis-controls-privacy-...
Protecting Privacy Using the CIS Controls Privacy Guide
The CIS Controls Privacy Guide provides best practices and guidance for implementing the CIS Critical Security Controls (CIS Controls) while consideri...
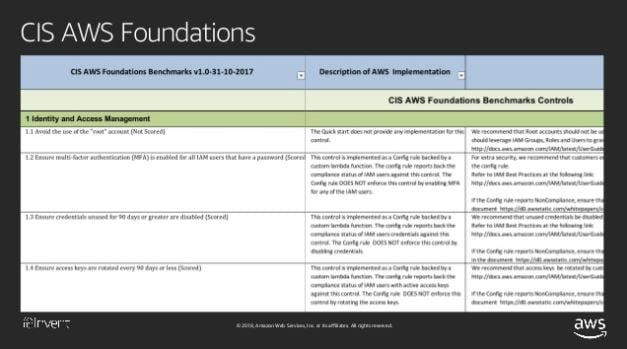
BLOG POST - https://www.cisecurity.org/insights/blog/wrap-up-cis-benchmarks-prevalent-at-aws-reinvent-2...
Wrap up: CIS Benchmarks Prevalent at AWS re:Invent 2018
AWS re:Invent took Las Vegas by storm again this November, bringing together cybersecurity industry leaders to discuss and develop the leading edge of...
WEBINAR - https://www.cisecurity.org/insights/webinar/foundational-cybersecurity-first-step-toward-co...
Foundational Cybersecurity as the First Step Toward Compliance
October 23, 2018 | 2:00 PM EDT Organizations often use multiple regulatory frameworks to guide their cybersecurity strategy. No matter which framework...
BLOG POST - https://www.cisecurity.org/insights/blog/keep-your-employees-interested-in-cybersecurity-aw...
Keep Your Employees Interested in Cybersecurity Awareness Training with these Tips
By Sean Atkinson, Chief Information Security Officer As organizations work to make internal company processes and personnel more secure it’s worth ask...
WHITE PAPER - https://www.cisecurity.org/insights/white-papers/a-cyber-defense-guide-for-the-financial-se...
A Cyber Defense Guide for the Financial Sector
The financial industry faces dangerous cyber-attacks every day. From data breaches to monetary theft to protecting tax information, banks, credit unio...
PRESS RELEASE - https://www.cisecurity.org/about-us/media/press-release/etsi-cis-controls-technical-reports
ETSI Publishes the CIS Controls™ as Technical Reports
The ETSI technical committee CYBER has updated its five-part international compendium of Technical Reports based on the CIS Controls....
BLOG POST - https://www.cisecurity.org/insights/blog/prepare-for-your-next-cybersecurity-compliance-aud...
Prepare for Your Next Cybersecurity Compliance Audit with CIS Resources
Reading a list of cybersecurity compliance frameworks is like looking at alphabet soup: NIST CSF, PCI DSS, HIPAA, FISMA, GDPR…the list goes on. It’s e...
BLOG POST - https://www.cisecurity.org/insights/blog/ciso-blog-response-planning-and-the-year-of-data-p...
Response Planning and the Year of Data Privacy
By Sean Atkinson, Chief Information Security Officer, CIS Spectre, Meltdown, and response planning As I start my third week here at CIS, we find multi...
BLOG POST - https://www.cisecurity.org/insights/blog/how-to-create-a-data-protection-plan
How to Create a Data Protection Plan
By Sean Atkinson, Chief Information Security Officer, CIS With 2018 being the “Year of Data Privacy,” organizations in every sector should focus on cr...
PAGE - https://www.cisecurity.org/standard-gdpr-clauses
Standard GDPR Clauses
STANDARD CLAUSES APPLICABLE TO CIS AGREEMENTS GOVERNED BY GDPR The data exporter, which constitutes (a) a Member as defined in a CIS SecureSuite Membe...
PAGE - https://www.cisecurity.org/privacy-notice/specific-cookies-used-by-cis
Specific cookies used by CIS
Category Name Domain Description Marketing __ab12# cisecurity.org pending Marketing __ncuid cisecurity.org Unclassified Marketing _alid_ vh.akamaihd.n...
BLOG POST - https://www.cisecurity.org/insights/blog/how-prioritized-security-controls-break-through-th...
How Prioritized Security Controls Break Through the Fog of More
By Sean Atkinson, Chief Information Security Officer & Stephanie Gass, Information Security Audit and Governance The 80s and 90s may have been the wil...