Why Your Organization Needs a Cybersecurity Roadmap
By Sean Atkinson, Chief Information Security Officer at CIS
Data breaches happen when we treat cybersecurity as a destination. The costs of doing so continue to rise year after year. For example, IBM found that the average data breach cost $4.45 million in 2023. That's 2.3% higher than the previous year and 15.3% greater than the 2020 value.
IBM also learned that data breaches cost organizations even more in certain industries. Healthcare organizations paid the most at $10.93 million. By comparison, financial organizations paid $5.90 million on average after a data breach. Organizations in the pharmaceutical, energy, and industrial sectors weren't too far behind at $4.82 million, $4.78 million, and $4.73 million, respectively.

We can minimize the risk of a data breach by approaching cybersecurity as a journey. But that in itself is not enough. No cybersecurity journey is the same. Yours is unique to you depending on the data you need to secure and the regulations with which you need to comply. If you have clients, their cybersecurity journey is unique to them.
As such, you need to be strategic and plan out your journey carefully. You can do so by creating a cybersecurity roadmap. In this blog, I explain what a cybersecurity roadmap is and discuss some of the benefits of creating one.

Crafting a Vision for Your Cybersecurity Needs
A cybersecurity roadmap is an assessment of current capability and a gap analysis with a short- to long-term vision for integrating security practices. The need to address future implementation, evolving compliance requirements that pertain to your industry, control enablement, and a road to follow is critical for your organizational and prioritization purposes.
The roadmap should delineate the predecessor tasks along the journey so controls and implementation complement a strategy of security and risk management.
The roadmap gives a perspective to stakeholders about the approach being taken to secure your organization and mitigate risk. The roadmap itself should be generalized to an extent to not be overly prescriptive. In essence, it shouldn't affect your organization's ability to alter the roadmap to address new risks or newly identified threats.
The ability to address agility is important. Prioritized items should be your first stops on the roadmap, but these can and often change in light of newly identified threats and regulatory updates. For example, you might prioritize the long-term replacement of a configuration management and control system after identifying vulnerabilities within your current system. As another example, you might see the Customized Approach introduced in Payment Card Industry's Data Security Standard (PCI DSS) v4.0 as an opportunity to adapt your security controls with a greater emphasis on continuous monitoring.
The Steps for Creating a Cybersecurity Roadmap
As I said above, your cybersecurity roadmap will be unique to your organization. Even so, there’s a set of steps that you can use to create a roadmap that fits your unique cybersecurity needs.
They are as follows:
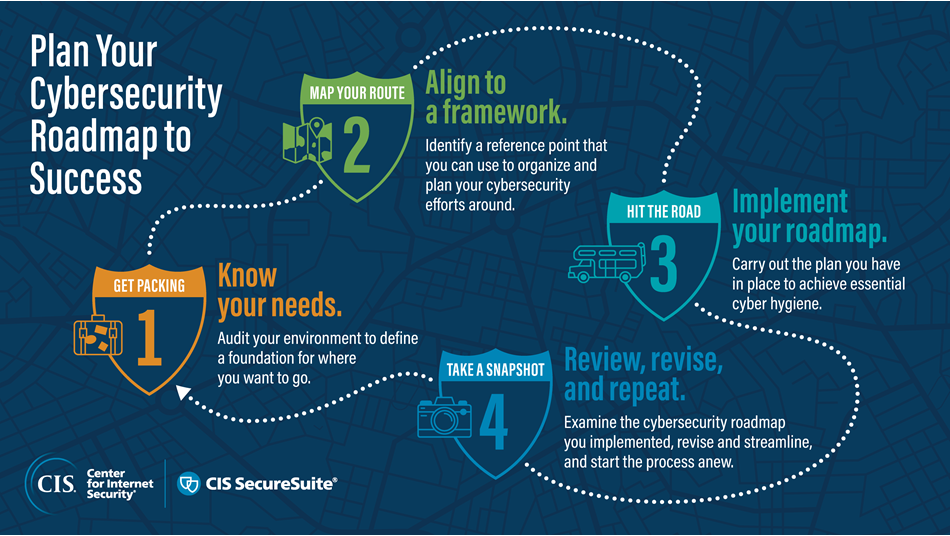
- Know your needs to get packing: Audit your environment to define a foundation for where you want to go.
- Align to a framework to plan your route: Identify a reference point that you can use to organize and plan your cybersecurity efforts around.
- Implement your roadmap to hit the road: Carry out the plan you have in place to achieve essential cyber hygiene.
- Review, revise, and repeat to take a snapshot: Examine the cybersecurity roadmap you implemented, revise and streamline, and start the process anew.
Here are some examples:
1. Know your needs to get packing
Financial Risk Assessment - Conduct a comprehensive risk assessment that prioritizes controls that address risks specific to your industry. For example, financial services industry checking for unauthorized access to customer accounts or manipulation of financial data, identifying and classifying sensitive financial data your organization stores and processes.
2. Align to a framework to plan your route
Financial Industry Frameworks - Consider using frameworks like CIS Controls and CIS Benchmarks, which are specifically designed to address security best practices and map to financial industry regulations like PCI DSS and GLBA. Using these frameworks can streamline compliance efforts while strengthening security.
Fortunately, you don’t need to do these steps on your own. At the Center for Internet Security (CIS), our CIS SecureSuite Membership can help your organization move through these steps. It comes with various benefits, tools, and resources for strengthening your cybersecurity posture, fulfilling your evolving compliance obligations, growing your cybersecurity maturity over time.
The video below goes over how you can harden your cybersecurity defenses via CIS SecureSuite.
CIS SecureSuite provides all you need for achieving your cybersecurity roadmap throughout its entire lifecycle. Tony Sager and I will explain how over a series of four blog posts. Stay tuned for more!
Look to Your Cybersecurity Future
The roadmap is an outline of a detailed journey that only time will tell if the future-looking mapping is accurate or should be changed based an external stimuli to the cybersecurity program.
Want to learn how to get started with a cybersecurity roadmap for your organization?
About the Author
Sean Atkinson
Chief Information Security Officer

Sean Atkinson is Chief Information Security Officer of CIS. He uses his broad cybersecurity expertise to direct strategy, operations, and policy to protect CIS’s enterprise of information assets. His job responsibilities include risk management, communications, applications, and infrastructure. Prior to CIS, he served as the Global Information Security Compliance Officer for GLOBALFOUNDRIES, serving Governance, Risk and Compliance (GRC) across the globe.
Prior to GLOBALFOUNDRIES, Atkinson led the security implementation for the New York State Statewide Financial System (SFS) implementation from 2007 to 2014, and his last role and responsibility was as the Internal Control, Risk and Information Security Manager.
Atkinson was born in Brooklyn, N.Y. and lived in England for 18 years, graduating from Sheffield Hallam University in 2000. After moving back to the United States, he has pursued multiple degrees and certifications in the IT arena.
In addition to his work with CIS, Atkinson is also an adjunct professor of Computer Science at the College of Saint Rose.
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.
.png?rev=4d7157de8bb34815a5cf6636e70a39ac&hash=254F86E12D68CA5A8F085886197FE7BF)