Know Your Needs: Get Packing for Your Cybersecurity Roadmap
By Tony Sager, Senior Vice President and Chief Evangelist

In a previous blog post, CIS’s CISO Sean Atkinson explained why every organization needs a cybersecurity roadmap.
A roadmap for a journey is a fair metaphor for a cybersecurity improvement program if we allow for some nuance. In cybersecurity, the situation is a “dynamic” journey. Road conditions change constantly (like we might today notice in Waze). Also, many points on the journey that were at one time fixed are continually changing. For instance:
- You might begin working with a new supplier and need to determine their cybersecurity risk posture.
- The regulatory environment might change, leaving you with the task of fulfilling a new compliance obligation or working with your clients to help them meet a new industry requirement.
- Your organization might deepen its understanding of the threats facing it, leading you to re-prioritize where you want to direct your security investments.
All of these changes can factor into your next stop along your journey. But every roadmap needs a starting point. In cybersecurity, the best place to start is for you to know your needs. I'll discuss what this step involves, what challenges you might face as you get packing for the journey ahead, how you can overcome them, and how the Center for Internet Security® (CIS®) can help you.
Take a Broad View from Where You Are
You can’t create a cybersecurity roadmap and act on it unless you figure out where you are first. In technical terms, we often refer to an “assessment” as a good place to start. But many assessments can get too granular too quickly.
A truly useful starting point is much broader and should start with your business and mission. As part of this step, you can ask yourself the following questions:
- What is the purpose of your business?
- Which sources of information and/or services are critical to fulfilling the identified purpose of your business? Pay particular attention to sensitive data like medical records, student information, and financial details.
- What are your dependencies? What risks do they pose?
A lot of this requires teasing out implicit or unspoken assumptions. You might also find the need to refine vague bumper stickers such as “Quality is job one” or “We are customer-driven” into specifics. By doing so, you can gain valuable context that you can use to navigate the steps that follow.

Tie the Business to Your Tech
Once you’ve gone through and evaluated your business, your mission, and your dependencies/risks, you must take that solid understanding and match it to an inventory of what technology you have.
This is sometimes easier said than done. Most organizations find tech inventory to be challenging because they don’t have the fundamental machinery in place to see and manage assets. It's more than a tech problem, as you must also have business processes in place to plan for, acquire, provision, and manage technology. Nor is it an exclusive security problem. It is about good asset management, which is similar to what you would expect for physical assets.
These types of questions may come to mind:
- How many instances of a particular technology do I have?
- What condition are they in?
- Where are they located?
- How are they protected?
- Who is responsible for them?
- Who can access them?
- What types of information, including sensitive data, do they store?
Keep in mind that developing an inventory isn’t a task without its flaws. Perfection of inventory is not the goal, nor is it possible. We don’t even have perfect inventory of physical space. What’s more, many inventory programs or security measures that require having a solid inventory, such as app allowlisting and management of admin privileges, have failed — not due to a lack of technology but due to a lack of "management will."
We’re not striving for perfection. What we’re looking to do is get close enough to make reasonable business risk decisions at this moment in time. Those business risk decisions will ultimately change. But it’s like having a cybersecurity roadmap in general. You need a place to start.
The Right Machinery for the Right "Management Will"
If you have the necessary motivation or "management will" to develop a solid inventory, you can find fundamental machinery that will help you. Take the CIS Critical Security Controls® (CIS Controls®) as an example. The CIS Controls provide a tested, vetted, transparent approach. They avoid security “magic” in favor of putting in place the foundations of good visibility and management. They do this right from the beginning with CIS Control 1: Inventory Control of Enterprise Assets and CIS Control 2: Inventory and Control of Software Assets. These security measures help you actively manage your enterprise and software assets to know what you need to monitor and protect. As such, you can use both Controls to identify unauthorized and unmanaged assets and thereby minimize your risk of shadow IT. What's more, both Controls 1 and 2 map to numerous security frameworks, helping you achieve compliance with regulations that matter to you in your industry.
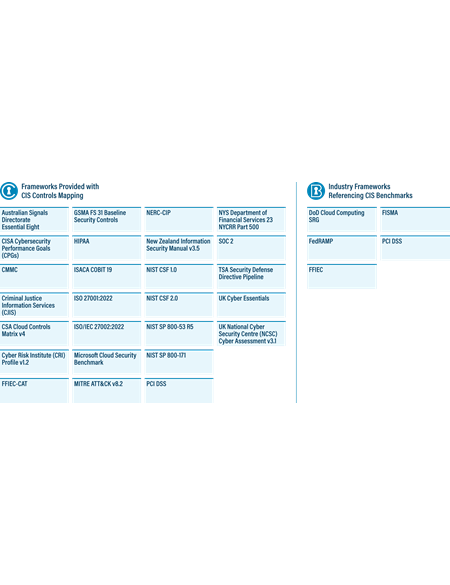
A list of frameworks and regulations to which the Controls map
You can implement CIS Controls 1 and 2 on your own. Alternatively, you can get even more support by becoming a CIS SecureSuite® Member. CIS SecureSuite gives you access to additional tools and resources that you can use to prioritize your implementation of CIS Controls 1 and 2 down to the level of individual Safeguards. In this way, you can begin tracking your actions so that you can draw out the rest of your cybersecurity roadmap, adjust it accordingly, and advance efforts to meet your complementary compliance requirements in the process.
The video below provides more information on how you can use CIS SecureSuite to fulfill your compliance obligations.
The Next Step for Your Cybersecurity Roadmap
Using CIS Controls 1 and 2, you can build an inventory and start to think about whether the technology you’re using is supporting your business mission and how they might be contributing to your risks. Such insight is crucial to packing for a cybersecurity roadmap that fits your unique business, regulatory, and industry needs and situation.
In the next blog post, Sean will discuss how to align your cybersecurity roadmap to a framework, thus ensuring your success. For now, get started identifying your organization’s needs.
About the Author
Tony Sager
Senior Vice President and Chief Evangelist

Tony Sager is a Senior VP & Chief Evangelist for the Center for Internet Security. He is involved in a wide variety of strategic, partnership, and outreach activities. He led the work which later became known as the CIS Critical Security Controls – an independent, volunteer-developed, cyber defense best practices program which is used throughout the industry. Tony has led numerous other activities to develop, share, scale, and sustain effective defensive cyber practices for worldwide adoption.
In addition to his duties for CIS, he is a volunteer in numerous cyber community service activities. He serves as an inaugural member of the DHS/CISA Cyber Safety Review Board, an advisor to the Minnesota Cyber Summit, and a member of advisory boards for several local schools and colleges. He is also a former member of the National Academy of Sciences Cyber Resilience Forum and serves on numerous national-level study groups and advisory panels.
Tony retired from the National Security Agency in 2012 after 34 years as a mathematician, computer scientist, and executive manager. As one of the Agency’s first Software Vulnerability Analysts, he helped create and lead two premier NSA cyber defense organizations (the System and Network Attack Center and the Vulnerability Analysis and Operations Group). In 2001, Sager led the release of NSA security guidance to the public and expanded NSA’s role in the development of open standards for security. Sager’s awards and commendations at NSA include the Presidential Rank Award at the Meritorious Level (twice) and the NSA Exceptional Civilian Service Award. The groups he led at NSA were recognized for mission excellence inside government and across industry with awards from numerous sources, including the SANS Institute, SC Magazine, and Government Executive Magazine.
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.
