Surge of QakBot Activity Using Malspam, Malicious XLSB Files
The Multi-State Information Sharing and Analysis Center (MS-ISAC) is observing an uptick in U.S. State, Local, Tribal, and Territorial (SLTT) QakBot activity aligned with open-source reporting. This includes the research project abuse.ch, which found that 74% of the malware payloads received in April 2022 were for QakBot.
What Is QakBot?
QakBot is a banking trojan that the cybersecurity community has tracked since 2007. Over time, it evolved into the modular malware that's currently being deployed. It has numerous capabilities and can perform enumeration (through net, whoami, nslookup, netstat, ipconfig, etc.), move laterally on a network through Server Message Block protocol (SMB), use keylogging capabilities to steal user credentials, monitor network traffic, and drop additional malware. More specifically, it monitors traffic to online banking websites and leverages a Man-in-the-Middle (MitM) technique to intercept authentication tokens on a user’s active banking session.
But that's not all. QakBot can also load additional modules, including credential and cookie harvesters, a Virtual Network Computing (VNC) module, Cobalt Strike, and an email collection module. It can also lead to other malware infections, such as ransomware. Once QakBot operators are finished with an infected host or network, the malware leverages Cobalt Strike modules to sell or grant access to other cyber threat actor (CTA) groups. For example, there is recent reporting that QakBot is tied to current ransomware campaigns, including Black Basta.
Cyber Threat Actors (CTAs) disseminating QakBot do so widely via malspam emails that often leverage thread hijacking. In the summer of 2022, the cybersecurity community observed QakBot exploiting CVE-2022-30190 (also known as Follina), a remote code execution vulnerability in Microsoft Windows Support Diagnostic Tool (MSDT).
Inside One QakBot Infection
The initial infection vector for all QakBot activity reported to the MS-ISAC was malspam; the attachments were either malicious XLSB file attachments or a password-protected ZIP file containing a malicious IMG, MSI, or XLSB file. Once executed, the malware reached out to malicious domains to download DLLs and create a new directory in the C: drive. The DLLs executed via regsvr32.exe. In some of the cases, the malware injected these DLLs into explorer.exe or onedrivesetup.exe. To establish persistence, QakBot created scheduled tasks via schtasks.exe.
In one incident worked by the MS-ISAC's Cyber Incident Response Team (CIRT), the QakBot payload was delivered to the victim via an email with an attached ZIP file.
Once the ZIP file was opened, an IMG file was presented to the victim. An IMG file is similar to an ISO file; both function as a “container” to store additional files. Within modern versions of Windows, an ISO or IMG file can be natively mounted by double-clicking the aforementioned file. Due to this ease of access, CTAs commonly switch to using these types of deliverables in their campaigns.
Figure 1. Delivered IMG file.
After natively mounting the IMG file by double clicking on it, the victim was presented with three files. Note that file icon of the file ‘54165666_666958’ is masqueraded as a folder. In actuality however, this was a shortcut (i.e., a LNK file).
- DLL
- Microsoft Word Document
- Windows shortcut or link (LNK) file

Figure 2. Contents of IMG file.
Reviewing the LNK file found that its purpose was to execute rundll32.exe and execute the DLL found within the same directory named "019338921.dll."
By reviewing the properties of the LNK file, we can identify its command arguments.
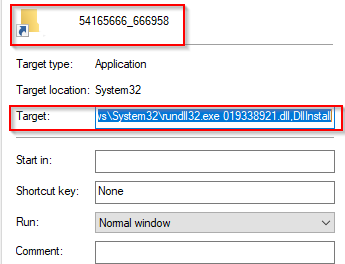
Figure 4. Command line parameters of LNK file.
Figure 5. Command line parameters of LNK file expanded.
Once clicked, the LNK file would have run the above parameters with the DllInstall function, which can be used to install or execute a specified DLL.
Review of the Microsoft Word document "doc693.docx" found that this file matched that of an Open Office XML (OOXML) document. This type of file is implemented as a ZIP archive containing various files that make up a single document.
It's possible to unzip an OOXML file to display its contents. As shown below, we can see that the file header of "doc693.docx" matched that of an OOXML format and was categorized as a ZIP file.

Figure 8. File header matching OOXML and zip.
Reviewing the contents of this file shows numerous files that make up the structure of the document.
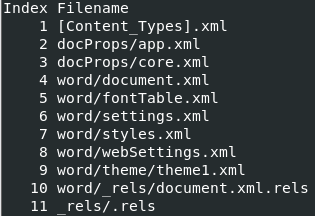
Figure 9. Contents of delivered Microsoft Document file.
Analysis of "document.xml.rels" found within "/word/_rels" revealed references to a hardcoded IP address. Once opened and its content enabled, the document reached out to the aforementioned IP address to access another file named "123.res." (At the time of analysis, this IP address and content were no longer available for review.)

Figure 10. Discovered hardcoded IP address.
Additional review of the aforementioned OOXML document found no suspicious macros, suggesting that the purpose of the document was to communicate with the hardcoded IP address to access "123.res."
Figure 11. No identified macros.
Based on the observed files, it is likely the CTAs implemented three malicious files to increase their chances of successfully compromising a victim’s machine. This included execution of the provided DLL, a disguised shortcut/LNK file, and a Microsoft Word document equipped to communicate with a suspicious IP address.
Depending on the initial access or execution technique used, such as opening the Microsoft Word file or executing the LNK file, the campaign typically downloads an additional payload to the system. In this example, a DLL named "gseae.dll" was downloaded and placed within C:\Users\%CurrentUser%\AppData\Roaming\Microsoft\. Here, a folder named "Hurosfyqv" was created. It contained the DLL as well as a registry RUN key for persistence.
Figure 12. Path and Run key value of observed DLL.
Shortly after the DLL dropped on the victim system, we observed the execution of various Living off the Land (LotL) reconnaissance-based commands and binaries. These included but were not limited to the following:
- Whoami.exe
- Net.exe
- Nslookup.exe
- Ipconfig.exe

Figure 13. Randomly named scheduled task.
Additionally, a Windows Defender exception was made for the suspicious DLL and directory by modifying the following registry key:
- HKLM\SOFTWARE\Microsoft\Windows\Defender\Exclusions\Path
Indicators of Compromise
The respective indicators of compromise (IOCs) are provided to aid in detecting and preventing infections from QakBot. Additionally, QakBot frequently shifts its C2 infrastructure, so all of the IP addresses listed below may not represent active infrastructure but can be used for threat hunting, respectively. Additionally, this list is not exhaustive of all IP addresses observed in open-source reporting. Security researchers, such as those operating Feodo Tracker, actively track QakBot and other malware C2 infrastructure.
C2 IPs
37[.]252[.]0[.]102
74[.]15[.]2[.]252
76[.]169[.]147[.]192
41[.]228[.]22[.]180
103[.]87[.]95[.]133
103[.]88[.]226[.]30
105[.]226[.]83[.]196
109[.]228[.]220[.]196
143[.]0[.]34[.]185
176[.]205[.]119[.]81
181[.]118[.]183[.]98
187[.]207[.]48[.]194
191[.]17[.]223[.]93
201[.]211[.]64[.]196
31[.]48[.]166[.]122
39[.]44[.]144[.]159
45[.]46[.]53[.]140
45[.]9[.]20[.]200
47[.]180[.]172[.]159
47[.]23[.]89[.]62
47[.]23[.]89[.]62:993
72[.]252[.]201[.]34
75[.]113[.]214[.]234
76[.]69[.]155[.]202
83[.]110[.]75[.]97
86[.]97[.]11[.]43
86[.]98[.]208[.]214
86[.]98[.]33[.]141
96[.]29[.]208[.]97
100[.]1[.]108[.]246
103[.]107[.]113[.]120
103[.]139[.]243[.]207
103[.]246[.]242[.]202
109[.]12[.]111[.]14
117[.]248[.]109[.]38
121[.]74[.]167[.]191
140[.]82[.]49[.]12
140[.]82[.]63[.]183
144[.]202[.]2[.]175
172[.]114[.]160[.]81
173[.]21[.]10[.]71
175[.]145[.]235[.]37
187[.]102[.]135[.]142
191[.]99[.]191[.]28
196[.]233[.]79[.]3
203[.]122[.]46[.]130
209[.]197[.]176[.]40
217[.]128[.]122[.]65
42[.]235[.]146[.]7
46[.]107[.]48[.]202
47[.]156[.]191[.]217
5[.]32[.]41[.]45
66[.]98[.]42[.]102
68[.]204[.]7[.]158
71[.]13[.]93[.]154
71[.]74[.]12[.]34
72[.]76[.]94[.]99
75[.]99[.]168[.]194
76[.]25[.]142[.]196
90[.]120[.]65[.]153
93[.]48[.]80[.]198
94[.]59[.]138[.]62
102[.]182[.]232[.]3
108[.]60[.]213[.]141
125[.]168[.]47[.]127
140[.]82[.]63[.]183
144[.]202[.]2[.]175
144[.]202[.]3[.]39
148[.]64[.]96[.]100
149[.]28[.]238[.]199
173[.]174[.]216[.]62
174[.]69[.]215[.]101
176[.]67[.]56[.]94
179[.]158[.]105[.]44
181[.]208[.]248[.]227
182[.]191[.]92[.]203
187[.]251[.]132[.]144
190[.]252[.]242[.]69
190[.]73[.]3[.]148
202[.]134[.]152[.]2
208[.]107[.]221[.]224
24[.]178[.]196[.]158
31[.]35[.]28[.]29
32[.]221[.]224[.]140
37[.]186[.]54[.]254
37[.]34[.]253[.]233
38[.]70[.]253[.]226
40[.]134[.]246[.]185
41[.]230[.]62[.]211
41[.]38[.]167[.]179
45[.]63[.]1[.]12
45[.]76[.]167[.]26
67[.]209[.]195[.]198
70[.]46[.]220[.]114
73[.]151[.]236[.]31
76[.]70[.]9[.]169
78[.]87[.]206[.]213
80[.]11[.]74[.]81
81[.]215[.]196[.]174
82[.]152[.]39[.]39
84[.]241[.]8[.]23:32103
85[.]246[.]82[.]244
91[.]177[.]173[.]10
92[.]132[.]172[.]197
72[.]12[.]115[.]90
101[.]99[.]95[.]146
185[.]82[.]127[.]231
185[.]172[.]129[.]84
185[.]235[.]247[.]119
187[.]250[.]114[.]15
Example Filepaths
C:\Users\%CurrentUser%\AppData\Roaming\Microsoft\
C:\ProgramData\Microsoft\
C:\Users\%CurrentUser%\AppData\Roaming\Microsoft\
C:\Users\%CurrentUser%\AppData\Local\SetupTest\
SHA256 Hashes
Note: The below LNK file hash is a hash of rundll32.exe and is not inherently malicious. As stated above, QakBot has been sending malspam with a ZIP file. The file is an IMG file type that, once mounted, showed three documents: a Word document, a hidden DLL, and a LNK file. The LNK file used rundll32.exe to run the hidden DLL. The hash for the LNK file is included because if a SLTT entity finds a LNK file that has this hash while threat hunting, it is an indicator that there may be a compromise.
.dat
f868253b34e11c233326d0f0a74d55ba0191be645569256a8ae5d861afb29420
.zip
2df3858be48c17a61684fa267a8885634053467c883fe04cd875fb5ebe21ae8c
.img
Accbe0818487ccaa487f24abe838c1e2f3c3bc263ee941f2ae7c0a682803be79
.docx
D20120cc046cef3c3f0292c6cbc406fcf2a714aa8e048c9188f1184e4bb16c93
.dll
78db8f8d22bf3f7440b1abe9f121c9fcf009f648b629f9e22c8d8afb1d585da7
LNK file
b1e6a7a3e2597e51836277a32b2bc61aa781c8f681d44dfddea618b32e2bf2a6
MD5 Hashes
b54dbb1431a8fa4edfce5a2373482133
c01c463e2e821fecaae7ca17bd75f5e2
e8f99ccb8d4678955c8d34734b956f9a
ff8044d1a42fdc1ecd980766d7a6ca6d
202d6895d1ddd74cedba7da709b471d8
43637a386dbdb83a68293fcf46a5ca1d
84d2856f8e597b31377d0b94d2dc3f34
Mutex
Global\{06253ADC-953E-436E-8695-87FADA31FDFB}
MITRE ATT&CK Patterns Observed
Initial Access
T1566.001 Phishing: Spearphishing Attachment
T1566.002 Phishing: Spearphishing Link
Execution
T1047 Windows Management Instrumentation
T1053.005 Scheduled Task/Job: Scheduled Task
T1059.001 Command and Scripting Interpreter: PowerShell
T1106 Native API
T1204.001 User Execution: Malicious Link
T1204.003 Virtualization/Sandbox Evasion: Time Based Evasion
Persistence
T1053.005 Scheduled Task/Job: Scheduled Task
T1547.001 Boot or Logon AutoStart Execution: Registry Run Keys/Startup Folder
Defense Evasion
T1027 Obfuscated Files or Information
T1027.001 Binary Padding
T1027.002 Software Packing
T1027.005 Indicator Removal from Tools
T1036 Masquerading
T1055 Process Injection
T1055.012 Process Hollowing
T1070.004 Indicator Removal on Host: File Deletion
T1112 Modify Registry
T1140 Deobfuscate/Decode Files or Information
T1218.007 System Binary Proxy Execution: Msiexec
T1218.010 System Binary Proxy Execution: Regsvr32
T1218.011 System Binary Proxy Execution: Rundll32
T1553.002 Subvert Trust Controls: Code Signing
T1562.001 Impair Defenses: Disable or Modify Tools
Credential Access
T1056.001 Input Capture: Keylogging
T1110 Brute Force
T1539 Steal Web Session Cookie
T1555.003 Credential from Password Stores: Credentials from Web Browsers
Discovery
T1010 Application Window Discovery
T1016 System Network Configuration Discovery
T1016.001 Internet Connection Discovery
T1018 Remote System Discovery
T1033 System Owner/User Discovery
T1049 System Network Connections Discovery
T1057 Process Discovery
T1069.001 Permission Groups Discovery: Local Groups
T1082 System Information Discovery
T1083 File and Directory Discovery
T1120 Peripheral Device Discovery
T1124 System Time Discovery
T1135 Network Share Discovery
T1482 Domain Trust Discovery
T1497.001 Virtualization/Sandbox Evasion: System Checks
T1497.003 Virtualization/Sandbox Evasion: Time Based Evasion
T1518 Software Discovery
T1518.001 Security Software Discovery
Lateral Movement
T1091 Replication Through Removable Media
T1210 Exploitation of Remote Services
Collection
T1005 Data from Local System
T1056.001 Keylogging
Command and Control
T1071.001 Application Layer Protocol: Web Protocols
T1090.002 Proxy: External Proxy
T1095 Non-Application Layer Protocol
T1105 Ingress Tool Transfer
T1132.001 Data Encoding: Standard Encoding
T1568.002 Dynamic Resolution: Domain Generation Algorithms
T1572 Protocol Tunneling
T1573.001 Encrypted Channel: Symmetric Cryptography
Exfiltration
T1041 Exfiltration Over C2 Channel
How to Defend Against QakBot
To improve their network defenses against malware like QakBot, organizations can use application allowlists, which are recommended in CIS Critical Security Control 2. These will enable you to actively manage (inventory, track, and correct) all software on the network so that only authorized software is allowed to install and/or execute. You can also implement/enforce the Principle of Least Privilege, PowerShell Signed Scripts, and adequate logging (particularly for PowerShell) if not already implemented.
In terms of defending against a malspam attack, you must implement procedures that support safe email use. These actions include the following:
- Creating a suspicious email policy and specifying that all suspicious emails should be reported to the security and/or IT departments.
- Marking external emails with a banner denoting it is from an external source.
- Implementing filters at the email gateway for emails with known malspam indicators.
- Blocking suspicious IP addresses at the firewall.
- Enacting Domain Message Authentication Reporting and Conformance (DMARC) policy and verification by implementing the Sender Policy Framework (SPF) and the Domain Keys Identified Mail (DKIM) standards.
- Providing employee training to protect against social engineering and malspam.
Finally, if you're a U.S. State, Local, Tribal, or Territorial (SLTT) government organization, we recommend you become a member of the MS-ISAC. As a member, you gain access to various benefits and no-cost services that can help you protect against a QakBot infection. These include offerings that share indicators among MS-ISAC members, proactively block your network traffic from connecting to harmful web domains, monitor and stop unauthorized activities on the endpoint, and deliver both traditional and advanced network security alerts for the identification and reporting of malicious events.
References
- https://www.bleepingcomputer.com/news/security/qbot-now-pushes-black-basta-ransomware-in-bot-powered-attacks/
- https://twitter.com/abuse_ch/status/1521025776472178688
- https://news.sophos.com/en-us/2022/03/10/qakbot-injects-itself-into-the-middle-of-your-conversations/
- https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e
- https://attack.mitre.org/software/S0650/
- https://isc.sans.edu/forums/diary/Qakbot+infection+with+Cobalt+Strike+and+VNC+activity/28448/
- https://www.microsoft.com/security/blog/2021/12/09/a-closer-look-at-qakbots-latest-building-blocks-and-how-to-knock-them-down
- https://research.nccgroup.com/2022/06/06/shining-the-light-on-black-basta/
- https://www.trendmicro.com/en_us/research/22/e/examining-the-black-basta-ransomwares-infection-routine.html
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.