FAIR: A Framework for Revolutionizing Your Risk Analysis

In risk management, understanding the landscape of risks, their potential impact, and the likelihood of their occurrence is the first line of defense. Many frameworks exist to aid this analysis, but the Factor Analysis of Information Risk (FAIR) has emerged as a leading methodology for quantifying and managing information risk. By shifting the paradigm from subjective to quantitative analysis, FAIR has the potential to revolutionize your risk analysis approach.
In this blog post, I’ll provide an overview of how FAIR works, discuss some of the ways in which FAIR’s methodology revolutionizes risk analysis, and describe how a CIS SecureSuite Membership fits into the FAIR model.
Understanding FAIR
FAIR is a standard quantitative framework for understanding, analyzing, and quantifying information risk in financial terms. Unlike traditional risk assessments which focus on qualitative measures (e.g., high, medium, low), FAIR provides metrics about dollars and cents. In doing so, FAIR gives you a common language by which you and other stakeholders can understand what a risk means to your organization.
At a high level, FAIR’s model helps you to understand the probability and magnitude of loss tied to a potential risk event. As I discussed in a previous blog post, the FAIR model assigns a financial value to the risk based upon two factors: the loss event frequency, or the time frame during which a cyber threat actor (CTA) could affect an identified asset; and the loss magnitude, or the losses that could stem from the loss event. Both loss event frequency and loss magnitude also break down into subcategories that enable a detailed, nuanced understanding of risk. For instance, the former comprises threat event frequency, or the number of attempts a CTA could try to target an asset, and vulnerability, or the percentage of threat events that turn into loss events. Meanwhile, the latter encapsulates primary losses (such as productivity declines, the cost of replacements, and response times) and secondary losses (such as missed competitive advantages, reputational damages, and fines/judgments).
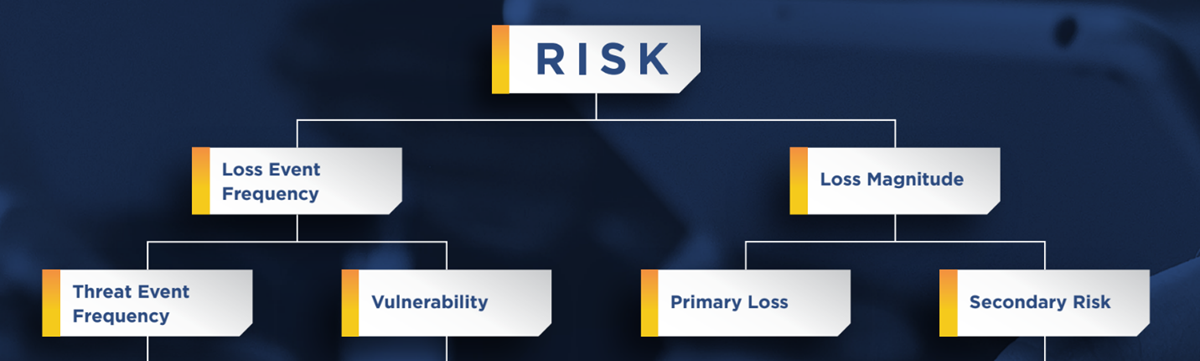
Source: The FAIR Institute
Threat event frequency, vulnerability, and secondary losses also have their own subcategories. You can learn more with this full view of FAIR’s risk analysis methodology.

Why FAIR Is Revolutionary for Risk Analysis
1. Emphasis on Quantitative Data
FAIR's primary strength lies in its ability to quantify risk. Expressing risk in financial terms enables you to make more objective and rational decisions. This quantitative data can be integrated into broader financial analysis, enhancing overall strategic planning and decision-making.
2. Prioritizing Risks Efficiently
By quantifying risks, FAIR enables you to compare and prioritize them based on potential financial impact. This allows for a more efficient allocation of resources, targeting the troubles with the most significant potential for harm.
3. Enhanced Communication
Expressing risk in financial terms enhances communication with stakeholders. It provides a common language that bridges the gap between technical risk experts and business executives. This can improve decision-making and buy-in for risk mitigation strategies.
Other means of risk analysis don’t provide this level of communication. For instance, qualitative risk analysis doesn’t provide actionable or prioritized input that organizations need to effectively address risk within their environment. It gives a general impression that can guide decision-making around risk, but those decisions reflect the level of context that you have around a particular risk. To see this in action, you can review the “bald tire scenario.”
4. Facilitating Risk Transfer Decisions
With a clear understanding of the potential financial impact of risks, you are better equipped to make decisions about risk transfer. This is where you make a business agreement to pay/contact/direct another to take responsibility for mitigating a risk. As an example, you transfer your risk when you purchase any type of insurance. The key is to ground your risk transfer considerations on a solid foundation of what the risks mean to you. That way, you’ll ensure that your decisions are cost-effective and aligned with your organization's risk tolerance.
5. Supporting Continuous Improvement
FAIR encourages an ongoing risk analysis process, with regular updates as new data becomes available. This supports continuous improvement, enabling you to adapt your risk management strategies in response to evolving circumstances.
CIS SecureSuite: The Natural Complement to FAIR
By now, you know about the advantages of using FAIR’s model to understand your risks. However, you might not know how to start applying FAIR’s quantitative risk analysis to your own organization.
This is where a CIS SecureSuite Membership comes in. It provides benefits, tools, and resources that you can use to strengthen your cybersecurity posture by implementing CIS security best practices. Among them are the pro version of our CIS Configuration Assessment Tool (CIS-CAT Pro) and the pro version of our CIS Controls Self Assessment Tool (CIS CSAT Pro). Both can help you better understand and contextualize your risks in accordance to the FAIR model. Let’s explore a few examples below.
Insight into Quantitative Data
Using CIS CSAT Pro, you can track your implementation of the CIS Critical Security Controls (CIS Controls) at the level of individual CIS Safeguards. You can use such insight to determine your progress in implementing all of the Safeguards of a single Control and/or all of the Safeguards of an Implementation Group (IG). This gives you an understanding of where you are in the process of managing a certain risk.
It’s a similar story with CIS-CAT Pro, which enables you to conduct automated scans of your systems’ settings against the secure recommendations of the CIS Benchmarks. Each scan yields an HTML report, which includes a percentage that demonstrates your scanned system’s conformance to the corresponding CIS Benchmark’s guidance. This score quantifies to what extent your hardening efforts on your system fulfill a CIS Benchmark configuration profile, whether that be base-level (Level 1), defense-in-depth (Level 2), or those of the Defense Information Systems Agency Security Technical Implementation Guides (DISA STIGs).
Want to learn how CIS-CAT Pro can help you speed along to the implementation phase? Check out this video below.
Communication Around Prioritized Risks
The FAIR model emphasizes the importance of communicating with stakeholders about risk analysis and prioritizing risks accordingly. The same can be said about CIS CSAT Pro. It’s designed to help you prioritize your implementation of the Controls from the level of individual Safeguards. With this view of your efforts, you can plan to apply all the Safeguards of an IG that match your cybersecurity maturity. You can also look to implement all the Safeguards of a Control depending on your unique security requirements and risk mitigation priorities.
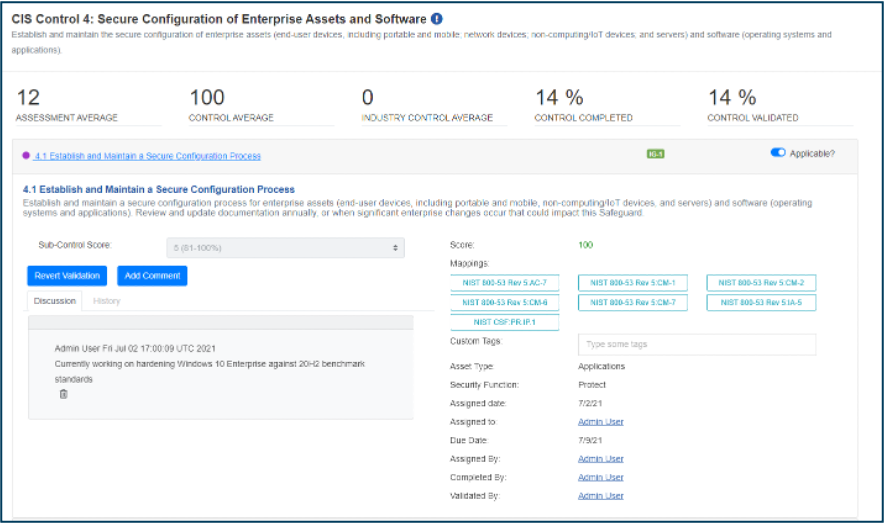
A screenshot of CIS CSAT Pro showing the completion percentage of CIS Control 4: Secure Configuration of Enterprise Assets and Software.
As part of this prioritization process, you can work with your team members and other stakeholders to assign tasks for each implementation effort. Such a collaborative process enables you to streamline your communication with stakeholders around mitigating cybersecurity risk. Similarly, it improves visibility around outstanding actions, thereby creating accountability for cyber defense across the organization.
A Toolbox for Continuous Improvement
Risk analysis means nothing if you can’t adapt and improve your understanding of your risks over time. CIS CSAT Pro and CIS-CAT Pro support this viewpoint. The former helps you to track your efforts so that you can move through the IGs of the Controls, growing your cybersecurity maturity along the way. Similarly, CIS-CAT Pro comes with a Dashboard component that displays your scanning results over a recent period of time. You can use these results to understand your systems’ conformance to the CIS Benchmarks, including how you’ve improved and where you still need to go.
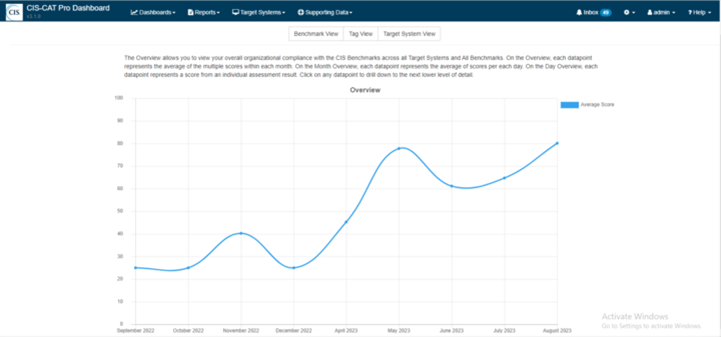
A screenshot of CIS-CAT Pro Dashboard showing conformance scores to a CIS Benchmark over one year.
Enhancing Your Risk Analysis Program with FAIR
The FAIR model offers a paradigm shift in risk analysis, shifting the focus from a subjective to a quantitative understanding of risk. While it may not replace other risk analysis forms, it provides another analysis capability for your organization to enhance your decision-making. It requires understanding the context of the business, gauging control depth, and adding a reality check to the number so that the calculations are not the one area assessed in risk management. By integrating FAIR into your risk management approach, you can achieve a more robust, objective, and practical understanding of your risk landscape.
Just remember that FAIR, like any model, is not a panacea. It is most effective when used as part of a broader risk management strategy, incorporating quantitative and qualitative analysis methods. Nevertheless, the value of FAIR in revolutionizing risk analysis is undeniable. It is well worth considering for you organization as you seek to enhance your approach to managing risk in today's uncertain world.
In the next blog post, I’ll shift my focus from risk to compliance. Specifically, I’ll address what you need to do the moment after you’ve successfully fulfilled your compliance requirements.
Check out our related blog posts:
Want to explore CIS SecureSuite in the meantime?
About the Author
Sean Atkinson
Chief Information Security Officer

Sean Atkinson is Chief Information Security Officer of CIS. He uses his broad cybersecurity expertise to direct strategy, operations, and policy to protect CIS’s enterprise of information assets. His job responsibilities include risk management, communications, applications, and infrastructure. Prior to CIS, he served as the Global Information Security Compliance Officer for GLOBALFOUNDRIES, serving Governance, Risk and Compliance (GRC) across the globe.
Prior to GLOBALFOUNDRIES, Atkinson led the security implementation for the New York State Statewide Financial System (SFS) implementation from 2007 to 2014, and his last role and responsibility was as the Internal Control, Risk and Information Security Manager.
Atkinson was born in Brooklyn, N.Y. and lived in England for 18 years, graduating from Sheffield Hallam University in 2000. After moving back to the United States, he has pursued multiple degrees and certifications in the IT arena.
In addition to his work with CIS, Atkinson is also an adjunct professor of Computer Science at the College of Saint Rose.
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.
