Cyber-Attack Defense: CIS Benchmarks + CDM + MITRE ATT&CK
By Jennifer Jarose, CIS Cybersecurity Engineer, CIS Benchmarks
Six trillion dollars…that’s the amount global cybercrime is expected to cost this year, according to Cyber Security Ventures. The Center for Internet Security (CIS) is committed to validating our standards against recognized cyber defense frameworks in the hopes to help reduce this amount in the future. Starting today, with the CIS Microsoft Windows 10 Benchmark, the CIS Benchmarks will map to the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) framework and CIS Community Defense Model (CDM) 2.0. These mappings will improve the use, understanding, and effectiveness of the CIS Benchmarks, in turn strengthening security posture and providing more support to prevent top cyber-attacks.
CIS Benchmarks and CIS Community Defense Model
CIS Benchmarks are consensus-developed, industry best practices for securely configuring operating systems, cloud services, applications, networks, and more. A global community of information technology (IT) security professionals that range from academia, government, industry, and individuals drive the development and maintenance of the CIS Benchmarks. CIS relies on the contributions of passionate industry experts to create and maintain the CIS Benchmarks. Interested in contributing? Sign up for CIS WorkBench and join a community.
Learn more about how you can defend against today’s most common cyber threats using CDM v2.0.
The CIS CDM v2.0 can be used to design, prioritize, implement, and improve an enterprise’s cybersecurity program. Enterprises naturally want to know, “how effective are the CIS Critical Security Controls (CIS Controls) against the top cyber-attacks?” The CDM can help answer that. This model leverages industry threat data to determine the top five cyber-attack types and creates comprehensive attack patterns (the set of attacker (sub-)techniques that are required to execute an attack). CDM v2 builds on the original version, by mapping the Safeguards from the CIS Controls v8 to the MITRE Enterprise ATT&CK® v8.2 framework. This methodology measures which Safeguards are most effective overall for defense across attack types.
Unifying the CIS Benchmarks, CDM, and MITRE ATT&CK Against Cyber-Attacks
To start these new mappings, CIS focused on two of the most downloaded CIS Benchmarks – Microsoft Windows 10 and Red Hat Enterprise Linux 7 – and drilled in to MITRE ATT&CK (sub-)techniques. This level of granularity provides CIS Benchmarks users a more detailed look into the effectiveness of the CIS Benchmarks against the top five attack types found in the CIS CDM. Combining technology-specific, security focused configuration settings from the CIS Benchmarks, with the prioritized, enterprise cyber defense guidance from the CIS CDM allows users a more holistic view of their cybersecurity program.
With the addition of mapping the MITRE ATT&CK framework to the CIS Benchmarks, this highlights the effectiveness of the CIS Microsoft Windows 10 v1.11.0 Benchmark, not only as security focused configuration recommendations, but quantifies its ability to reduce the risk and impact of a range of cyber-attacks. Additionally, CIS SecureSuite Members can visit CIS WorkBench to view the MITRE ATT&CK framework mappings, which can be found in the Excel version of the Benchmarks. CIS will continue refining and expanding this methodology which will further support unification across other frameworks as CIS updates and expands the mappings offered.
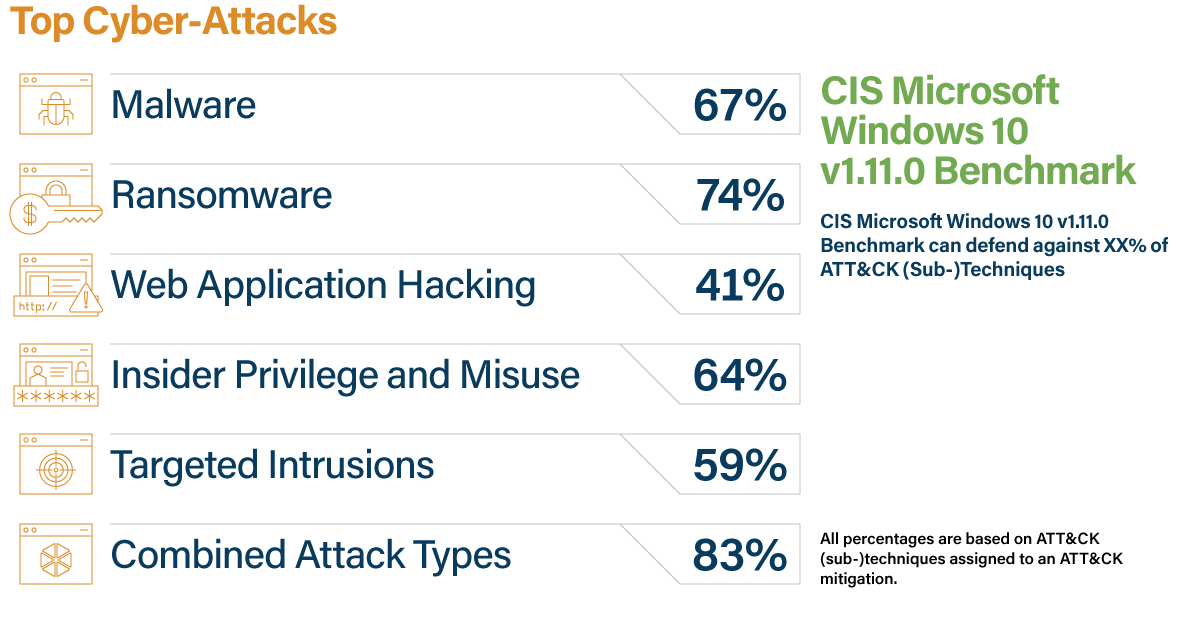
CIS Benchmarks’ Effectiveness Against Common Cyber-Attacks
The following findings demonstrate the security value of the CIS Microsoft Windows 10 v1.11.0 Benchmark against the top five cyber-attack types found in the CIS CDM:
- Malware: 67% of recommendations map to a parent or (sub-)technique
- Ransomware: 74% of recommendations map to a parent or (sub-)technique
- Web Application Hacking: 41% of recommendations map to a parent or (sub-)technique
- Insider and Privilege Misuse: 64% of recommendations map to a parent or (sub-)technique
- Targeted Intrusion: 59% of recommendations map to a parent or (sub-)technique
- Combined Attack Types: 83% of recommendations map to a parent or (sub-)technique when the above attack types are combined
The CIS Microsoft Windows 10 v1.11.0 Benchmark incorporates all parents of (sub-)techniques mapped to a given recommendation. In addition, the Microsoft Windows 10 v1.11.0 Benchmark is mapped to a subset of techniques within the Community Defense Model as a number of them do not apply to the Windows operating system.
When a Benchmark recommendation maps to a given parent or (sub-)technique it means that the given recommendation potentially mitigates, or disrupts, that step in a cyber-attack.
This effort is ongoing to further support unity of CIS resources with industry frameworks. CIS is currently working to expand MITRE ATT&CK mappings to our catalog of technology specific CIS Benchmarks, starting with the most commonly used. Next up is Red Hat Enterprise Linux 7. Stay tuned for an even more detailed report on the effectiveness of the Microsoft Windows 10 and Red Hat Enterprise Linux mappings to the Community Defense Model’s top five cyber-attack types.
![]()
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.