A Short Guide for Spotting Phishing Attempts
You receive an email from your finance department. You still need to complete your yearly benefits review. You need to immediately fill out the form to avoid losing your benefits. You click the link in the email, which directs you to a page asking for your personal information, including your Social Security Number and a copy of your driver’s license.
Criminals convince people to act by assuming a position of authority to exploit trust and create a sense of urgency. As in the example above, cybercriminals frequently leverage social engineering attacks using manipulation and deception to trick victims into taking a particular action, such as clicking a link, opening an attachment, or providing confidential information.
Phishing is a form of social engineering that uses emails and malicious websites or attachments to gain information. Phishing emails can contain links prompting the user to provide information, such as login credentials or account information. Attackers can then take the information provided to gain access to those accounts. Phishing continues to be one of the most common methods cyber threat actors (CTAs) use. Trend Micro observed a 29% increase in phishing incidents between 2021 and 2022. Similarly, ZScaler ThreatLabz noted a 47% increase in phishing attacks in 2022 compared to 2021. Knowing the common signs of phishing can help you spot suspicious emails and prevent a possible compromise.
How Attackers Use Phishing
Cybercriminals continuously improve their phishing campaigns, leveraging new technologies and exploits to achieve their goals. Attackers will also steal legitimate correspondence from compromised email accounts and incorporate that into their campaigns to improve their chances of success.
CTAs can use advancements in technologies, including generative Artificial Intelligence (AI) platforms like ChatGPT and Google Bard, to improve the quality of phishing emails. They can use these systems to generate believable content, eliminating some of the previous tell-tale signs, such as poor grammar and spelling.
Below are some examples of real-world phishing emails that have been reported:
Example 1: Malicious Link with Thread Hijacking
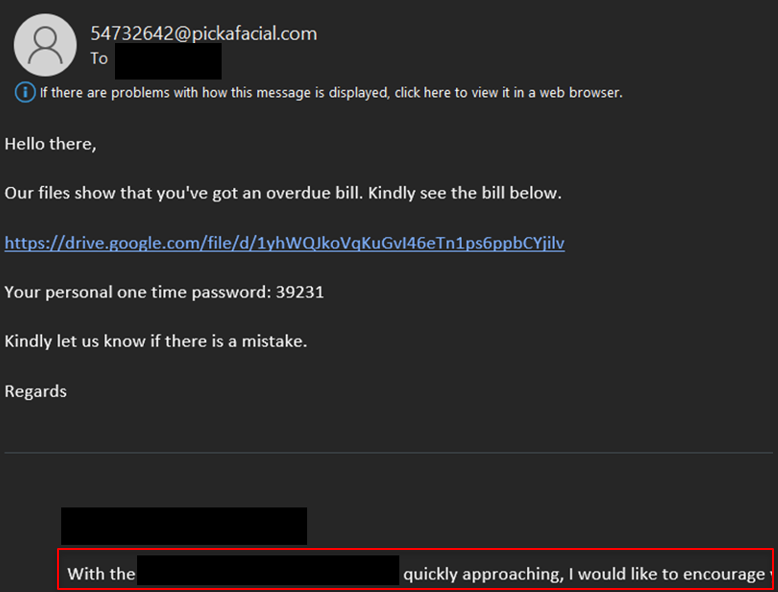
In this example, the phishing email invokes a sense of urgency by referencing an overdue bill. The email also includes a link and a “one-time password” to appear legitimate.
The bottom of the email in the red box is an example of thread hijacking, where the attacker takes legitimate correspondence from a separate email account they previously compromised and adds it to the bottom of the email to look legitimate.
Example 2: Malicious File
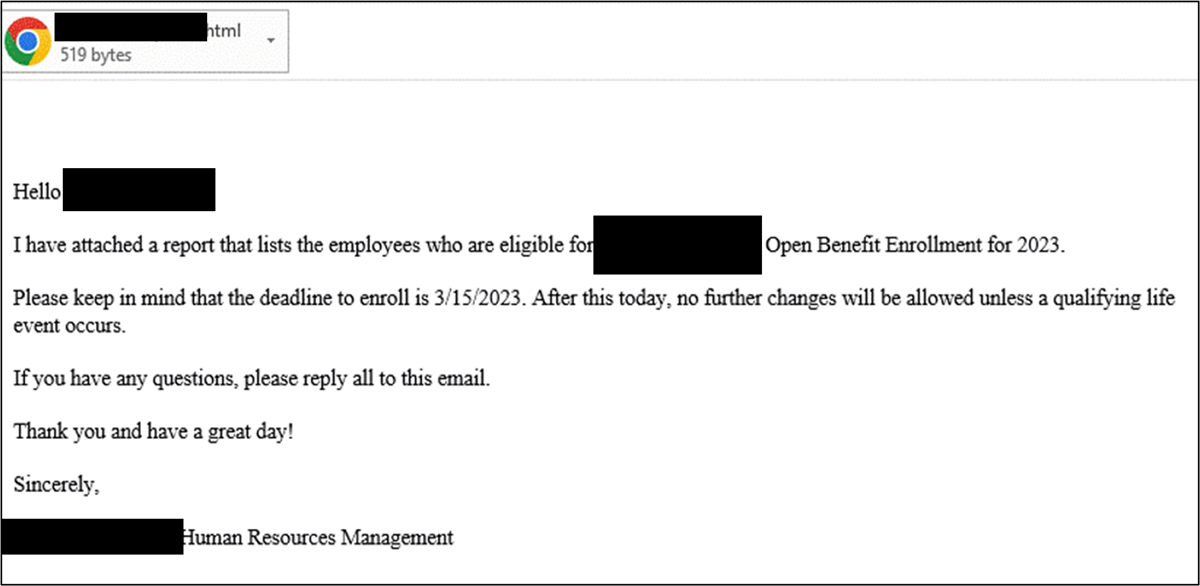
In this example, the attacker impersonates a trusted authority (human resources) and appeals to a sense of urgency surrounding Open Benefit Enrollment. The attachment is a malicious HTML file that attempts to exploit a known vulnerability.
Example 3: Malicious File with Thread Hijacking
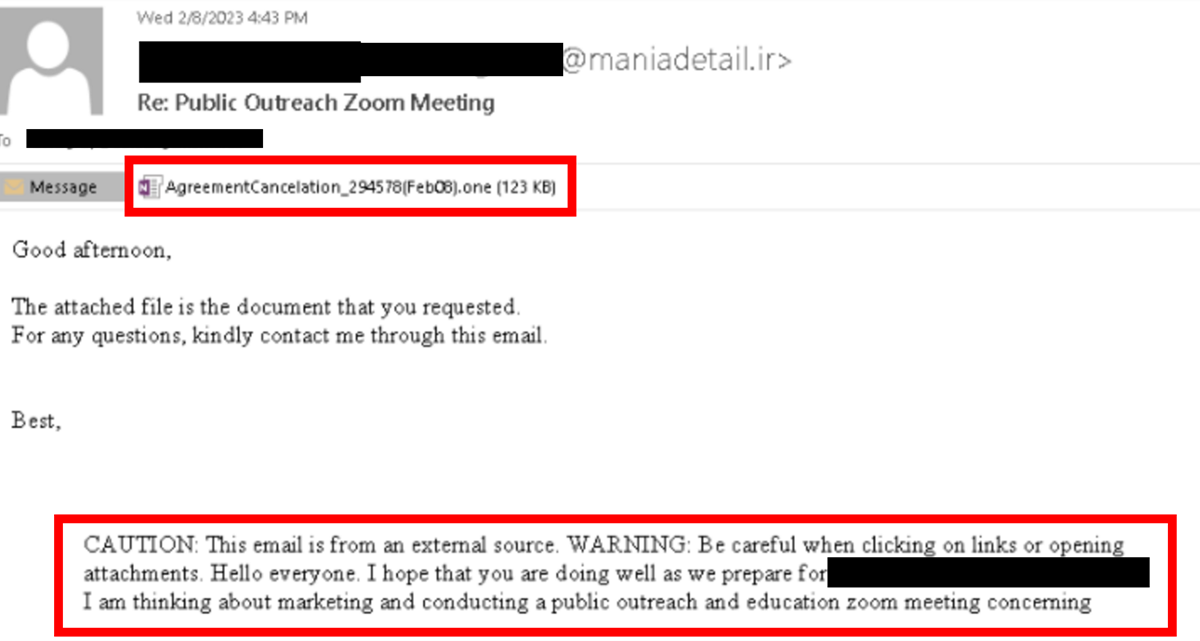
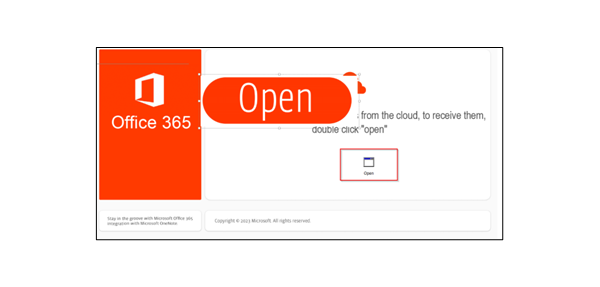
In this example, the attacker again takes legitimate correspondence and includes it at the bottom of the email to appear legitimate. The attachment to the email is a OneNote file. In the file, the attacker hides a malicious script behind the “open” button to trick the user into activating it.
Example 4: Call Back Phishing
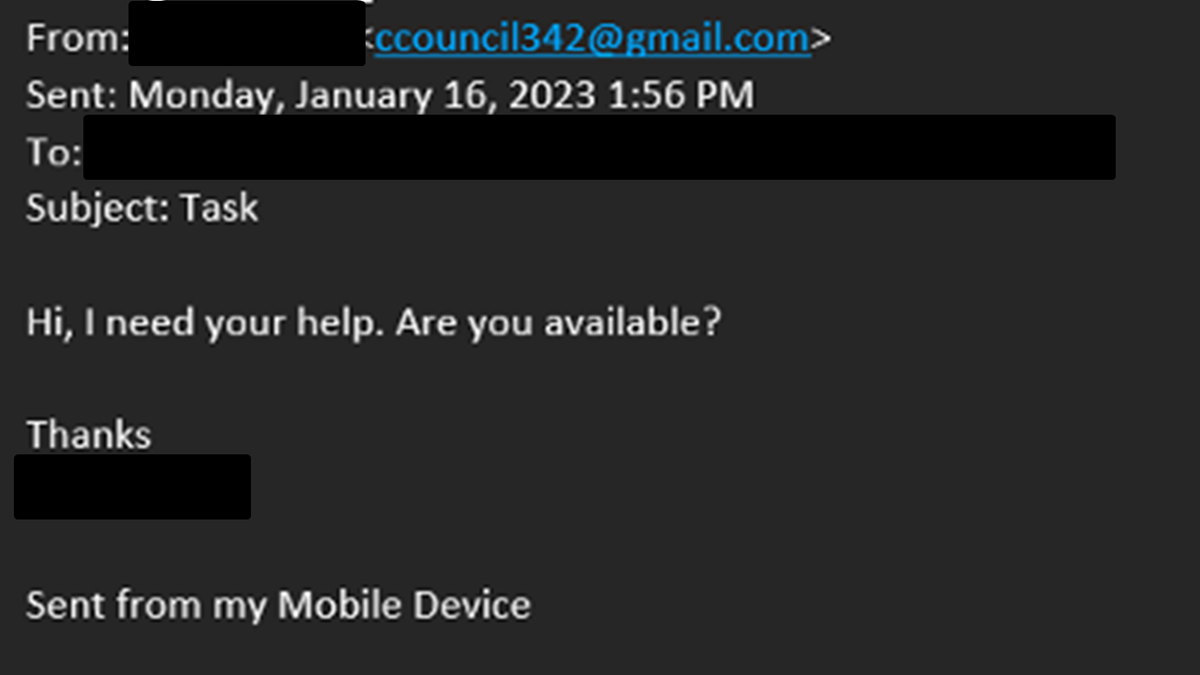
In this example, the attacker doesn’t provide a link or attachment in the email. The attacker poses as the recipient’s manager and asks the recipient to contact them. Previously observed versions of these emails involve the attacker asking for financial assistance or account information. Other iterations of these phishing emails include pretending to help the victims deal with an issue, typically through downloading tools or malware that can be used to compromise a system or steal information.
If You See Something…
Here’s what to do if you spot a suspicious email: notify your IT security team or Chief Information Security Officer (CISO). They may have policies in place for handling suspected phishing. Examples include forwarding the email to a secure inbox for analysis or deleting it from your inbox. Above all, do not click on any links or download attachments if you do not know the email sender. Remember, legitimate organizations will never ask for sensitive information via an unsolicited email.
Training Is Key
Teaching employees how to spot phishing emails is key to defending against attacks. Make sure they know what to do if they spot a suspicious email. These include the following best practices:
- Don’t open the email, click on any links, or download/open any attachments.
- Report the email to your IT security team.
- Follow organizational security policies.
To address this need, CIS is proud to partner with the SANS Institute to offer our members SANS Security Awareness Phishing Tools. SANS Phishing Tools provides a simple, cost-effective tool that allows you to reach everyone within your organization to test the security awareness of your employees through phishing exercises.
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.