All Insights
Explore security resources, trends and updates, media, podcast episodes, and more
Filter
1340 Results Found
Solutions
Industry
971 - 980 of 1340 results
Published on 07.07.2020
In these unprecedented times, CISOs face many hurdles in securing virtual office environments. Indeed, in some organizations, virtual environment...
CIS Controls
Published on 07.06.2020
CIS Check Point Firewall Benchmark v1.1.0 Prescriptive guidance for Check Point Firewall, provides prescriptive guidance for establishing a secur...
CIS BenchmarksTechnology
Published on 06.30.2020
Analyzing security configuration assessment results is paramount to remediation planning efforts. The latest update to CIS-CAT Pro Assessor inclu...
CIS BenchmarksCIS SecureSuite
Published on 06.30.2020
Washington State Auditor’s Office uses the CIS Controls to perform security audits and improve the security posture of state agencies & local gov...
CIS Controls
Published on 06.29.2020
The Summer 2020 issue of Cybersecurity Quarterly highlights the CIS Controls mapping in the 2020 Verizon DBIR, new mappings to the CIS Controls, ...
CIS Controls
Published on 06.22.2020
At CIS, we believe in cultivating a trusted and collaborative environment for information sharing. Through our Community, we develop industry-lea...
CIS ControlsTechnology
Published on 06.16.2020
What it is: Cloud computing is the storing, accessing and delivering of data, programs, and other computing services on the internet rather than ...
Published on 06.12.2020
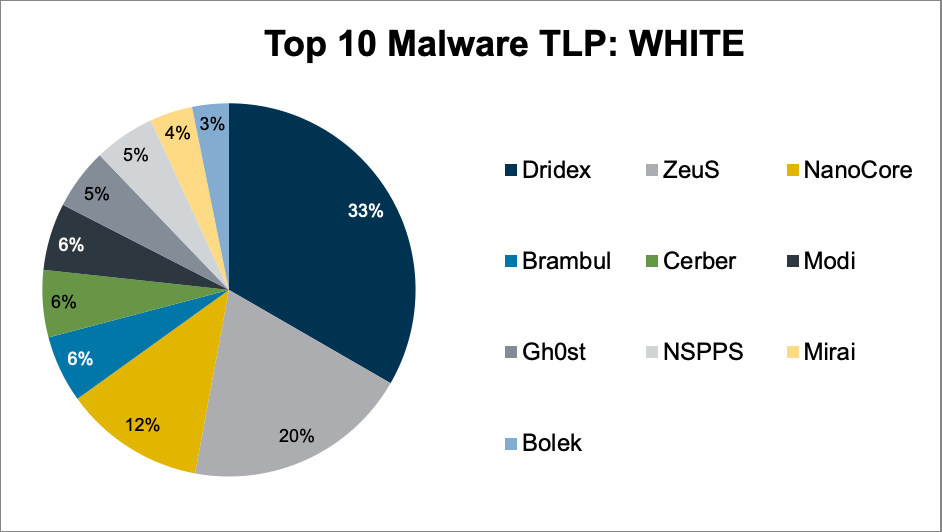
Top 10 Malware composition was fairly consistent with April 2020 with the exception of Modi, Mirai, and NSPPS. Overall, the Top 10 Malware varian...
MS-ISAC
Published on 06.09.2020
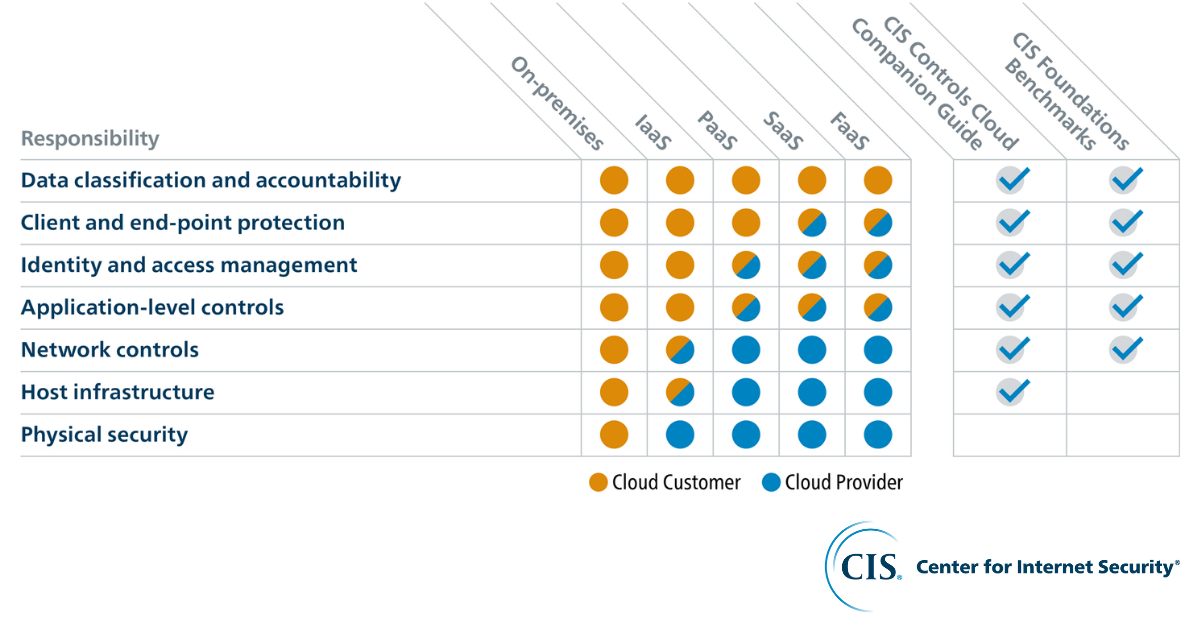
According to Gartner, “Through 2022, at least 95% of cloud security failures will be the customer’s fault.” With high chances of user error, limi...
CIS Hardened Images
Published on 06.09.2020
The COVID-19 pandemic changed business practices worldwide. The traditional workplace transformed; for many, the “new norm” is now a home office ...
CIS Hardened Images
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More