Showing results 1 - 20 of 2257 for "BestCoinShare💡231BestCoinShare.Com💡231Referral Codes Invitation Codes Invite Codes Promo Codes To Sign Up For Bonuses"
SPOTLIGHT - https://www.cisecurity.org/insights/spotlight/election-security-spotlight-dangers-of-qr-cod...
Election Security Spotlight – Dangers of QR Codes
In this Election Security Spotlight, the Elections Infrastructure Information Sharing and Analysis Center (EI-ISAC) discusses the dangers of QR codes....
PAGE - https://www.cisecurity.org/cis-securesuite/promo-terms
CIS SecureSuite® Promo Terms
CIS may offer limited-time promotional opportunities to save up to 20% on a new CIS SecureSuite Membership. This promotion is only available for new M...
PAGE - https://www.cisecurity.org/rss-syndication
RSS Syndication
Plain Text The MS-ISAC® provides information about our Advisories and Daily Cyber Tip in plain text format: www.cisecurity.org/text-feed-help/ RSS and...
MEDIA MENTION - https://www.cisecurity.org/about-us/media/media-mention/cis-offers-free-dns-security-tool-f...
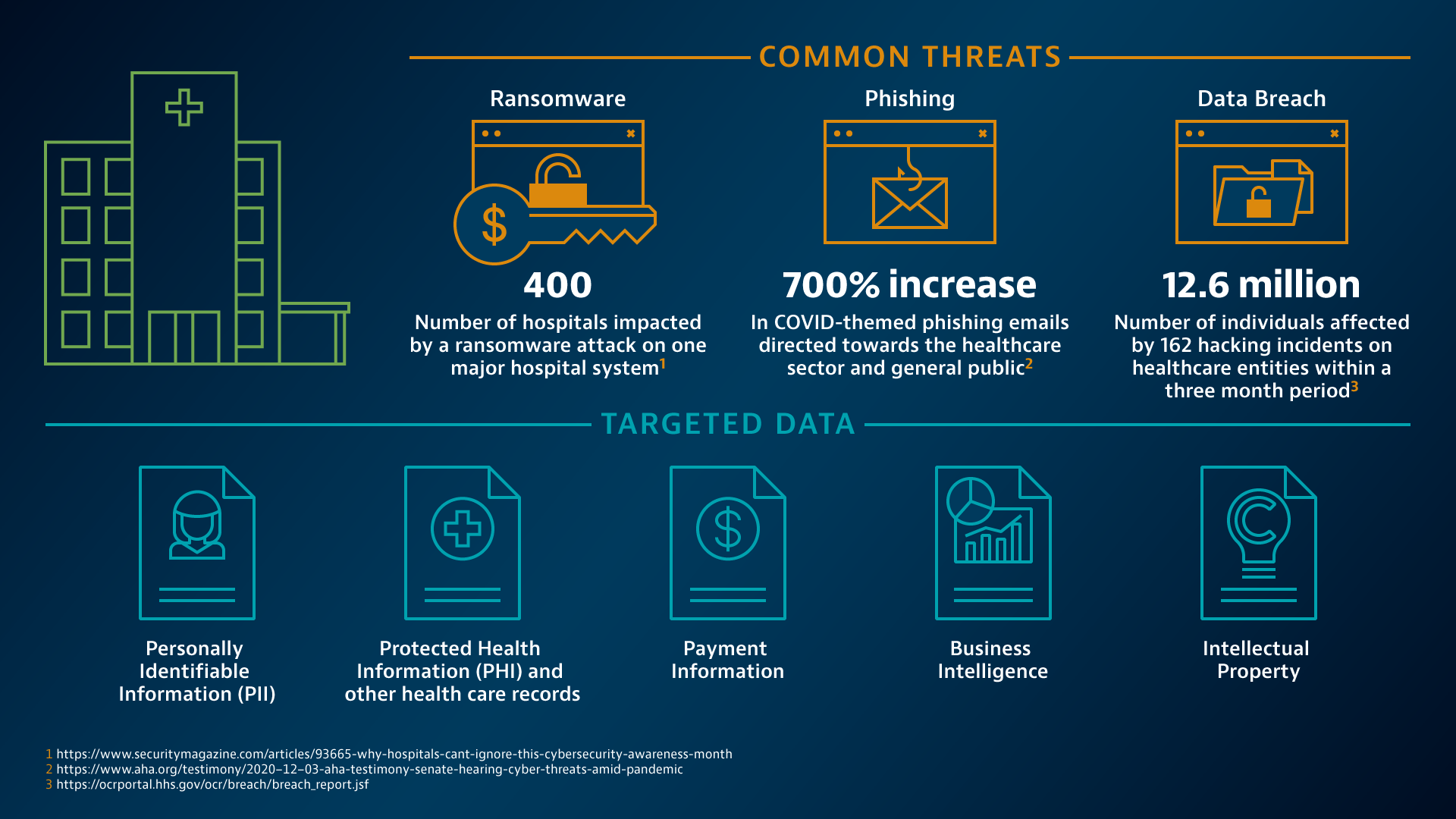
CIS Offers Free DNS Security Tool for US Hospitals
Hospitals would be well minded to sign-up for the MDBR service given the increase in threat activity launched against the sector during 2020....
BLOG POST - https://www.cisecurity.org/insights/blog/mimikatz-the-finest-in-post-exploitation
Mimikatz: The Finest in Post-Exploitation
Part 2 in a series on Malware Overview The MS-ISAC continuously observes attacks using the post-exploitation credential stealing tool Mimikatz. Many c...
BLOG POST - https://www.cisecurity.org/insights/blog/authentication-and-authorization-using-single-sign...
Authentication and Authorization Using Single Sign-On
By: Kathleen M. Moriarty, CIS Chief Technology Officer In order to prevent credential theft from phishing attacks, there is a push for multi-factor au...
MEDIA MENTION - https://www.cisecurity.org/about-us/media/media-mention/the-csi-effect-comes-to-cybersecuri...
The CSI Effect Comes to Cybersecurity
Deploying the top five CIS Critical Security Controls can reduce up to 90 percent of known pervasive and dangerous cyber-attacks....
PAGE - https://www.cisecurity.org/hospitals
No-Cost Malicious Domain Blocking and Reporting for U.S. Hospitals
With the increasing industry shift to electronic health records and other digital technologies, cybersecurity has become a strategic priority for the ...
BLOG POST - https://www.cisecurity.org/insights/blog/ctas-using-adversary-in-the-middle-aitm-phishing-a...
CTAs Using Adversary in the Middle (AiTM) Phishing Attacks
Cyber threat actors show no sign of curbing their Adversary in the Middle (AiTM) phishing attacks against SLTTs. Here's how to defend your organizatio...
ADVISORY - https://www.cisecurity.org/advisory/multiple-vulnerabilities-in-adobe-products-could-allow-...
2023-133: Multiple Vulnerabilities in Adobe Products Could Allow for Arbitrary Code Execution
Multiple vulnerabilities have been discovered in Adobe products, the most severe of which could allow for arbitrary code execution. A...
BLOG POST - https://www.cisecurity.org/insights/blog/insider-threats-in-the-healthcare-sector
Insider Threats: In the Healthcare Sector
Organizations are often too preoccupied with defending the integrity of their company and network from external threats to address the very real and d...
ADVISORY - https://www.cisecurity.org/advisory/multiple-vulnerabilities-in-citrix-products-could-allow...
2023-080: Multiple Vulnerabilities in Citrix Products Could Allow for Remote Code Execution
Multiple vulnerabilities have been discovered in Citrix products, the most severe of which could allow for remote code execution. Citrix ADC perfor...
MEDIA MENTION - https://www.cisecurity.org/about-us/media/media-mention/vulnerabilities-in-thunderbird-emai...
Vulnerabilities in Thunderbird Email Client Allow Code Execution
Security updates for the Thunderbird email client address vulnerabilities that could be exploited to execute arbitrary code on impacted systems....
BLOG POST - https://www.cisecurity.org/insights/blog/data-deserialization
Data Deserialization
Computer data is generally organized in data structures such as arrays, records, graphs, classes, or other configurations for efficiency. When data st...
BLOG POST - https://www.cisecurity.org/insights/blog/how-to-secure-your-online-identity-with-security-k...
How to Secure Your Online Identity with Security Keys
An intern with our CTO office embarked on a short project to protect her accounts with security keys. Here's what her experience was like....
NEWSLETTER - https://www.cisecurity.org/insights/newsletter/vishing-and-smishing-what-you-need-to-know
Vishing and Smishing What You Need to Know
Vishing and smishing are common social engineering attacks used by cybercriminals. Learn more about what they are and how to thwart them....
BLOG POST - https://www.cisecurity.org/insights/blog/remote-assessment-comes-to-cis-cat-pro-v4
Remote Assessment comes to CIS-CAT Pro Assessor v4
CIS recently announced its latest update to the CIS-CAT® Pro configuration assessment tool. CIS-CAT Pro Assessor v4 provides new features and function...
ADVISORY - https://www.cisecurity.org/advisory/updated-ms-isac-cybersecurity-advisory---multiple-vulne...
2023-100: UPDATED – MS-ISAC CYBERSECURITY ADVISORY - Multiple Vulnerabilities in Apple Products Could Allow for Arbitrary Code Execution PATCH: NOW - TLP: CLEAR
Additional systems were found to be affected by vulnerabilities, the most severe of which could allow for arbitrary code execution....
ADVISORY - https://www.cisecurity.org/advisory/a-vulnerability-in-the-backup-migration-plugin-for-word...
2023-141: A Vulnerability in the Backup Migration Plugin for WordPress Could Allow for Remote Code Execution
A vulnerability has been discovered in the Backup Migration Plugin for WordPress, which could allow for remote code execution. The Backup Migration...