TrickBot: Not Your Average Hat Trick – A Malware with Multiple Hats
Part 1 in a series on Malware
Summary
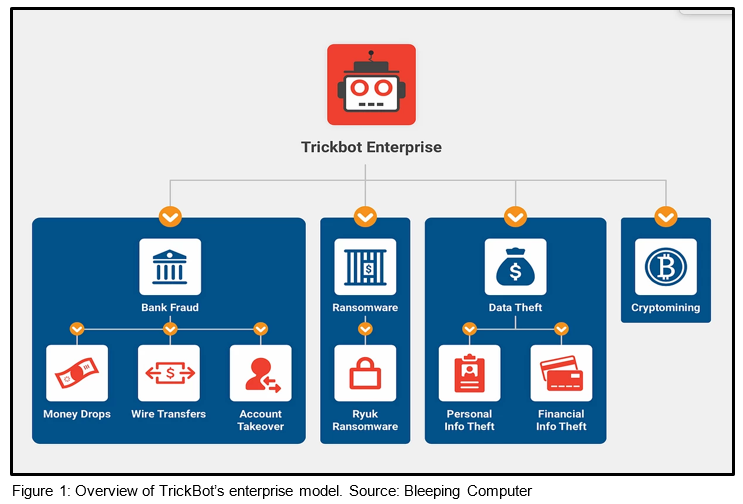
TrickBot originated as a banking credential theft Trojan, but is now considered a modular malware enterprise with sophisticated system reconnaissance, persistence capabilities, and an association with follow-on ransomware infections. The MS-ISAC continues to monitor TrickBot’s capabilities and the threats it poses to MS-ISAC members.
Not yet an MS-ISAC member? Here’s how to join our cyber defense community.
Background
TrickBot is a distant descendant of the ZeuS banking Trojan that emerged in 2005, but is most often traced back to Dyre or Dyreza, which went offline in 2015. TrickBot emerged in 2016, reusing aspects of Dyre’s code and retaining its banking credential harvesting capabilities and web inject infrastructure. TrickBot is now a malware empire with numerous plugin modules, cryptomining and persistence capabilities, and a growing association with follow-on ransomware infections. Beginning in June 2019, the MS-ISAC observed an increasingly close relationship between initial TrickBot infections and eventual Ryuk ransomware attacks. TrickBot also caught the attention of government and private entities in fall 2020, when it was reported that U.S. Cyber Command and private sector partners acted to blunt TrickBot’s reach and reduce chances its operators could interfere with 2020 U.S. election infrastructure. [1]
Technical Overview
TrickBot is often disseminated via malspam campaigns or dropped by other malware like the recently dismantled Emotet. Malspam lures delivering TrickBot leverage themes such as invoices, holiday greeting cards, traffic violations, and the COVID-19 pandemic. [2]
While security researchers have observed numerous infection vectors, the most common initial infection vector is malspam containing malicious macro-laden office documents.
Upon opening a malicious document, the end user is prompted to enable macros, which executes a base64 obfuscated VBScript to download the initial TrickBot binary from an external server. TrickBot will also use a number of publicly available resources, such as icanhazip[.]com[3] to determine the victim’s external IP address. Once executed, TrickBot writes itself to disk in the %AppData%Roaming% folder. TrickBot then unpacks itself with an obfuscated and encoded bot key unique to that infected machine.[4]
TrickBot also attempts to disable antivirus protection like Windows Defender and creates a scheduled task at system startup to ensure persistence.
After these initial actions on target, TrickBot is now able to receive commands and updated bot configurations, as well as load additional plugin modules as dynamic link library (DLL) files within the %Data% folder. TrickBot uses the unique bot key assigned to that machine to decrypt follow-on DLL plugins. In 2019, security researcher Vitali Kremez noted that TrickBot is capable of a User Account Control (UAC) bypass on both Windows 7 and Windows 10, allowing TrickBot to run or make changes to a system without a prompt requesting user authorization.[5]
Credential Theft
For traditional credential theft, TrickBot utilizes web injects to steal banking credentials and browser cookies. TrickBot uses two types of web injects:
- Redirection attacks (static injection) send victims to fraudulent banking site replicas when they navigate to certain banking websites. This fake website is hosted on the cyber threat actor’s (CTA’s) server and harvests the victim’s login information. It should be noted that researchers have not observed TrickBot utilizing redirection attacks since September of 2019.
- Server-side injections (dynamic injection)intercept the response from a bank’s server and redirects it to the CTA’s server. The web inject server injects additional code into the webpage before it is returned to the client. The CTA can then steal the victim’s banking credentials through the use of form-grabbers. Form grabbers benefit attackers by minimizing extraneous text that keyloggers normally generate and instead only show information entered into structured data fields.

Command and Control
TrickBot boasts resilient command and control (C2) infrastructure and a follow-on exploitation framework. It uses several types of infrastructure to support its array of functions and to withstand government and private sector takedown attempts. The CTAs operating TrickBot are constantly varying and replacing C2 infrastructure, making tracking and takedowns very difficult. TrickBot’s server types and functions include:
- Loader Server – Loads the initial TrickBot binaries onto an infected machine
- Core C2 – Communicates with and sends commands and updated configuration files to the infected bots
- Plugin Server – Loads additional modules onto TrickBot-infected machines, such as advanced system reconnaissance and lateral movement capabilities
- Webinject Server – These servers host configurations for static and dynamic web injects that harvest banking credentials via an infected browser on a host machine
- Dpost Server – Server where stolen credentials are routed
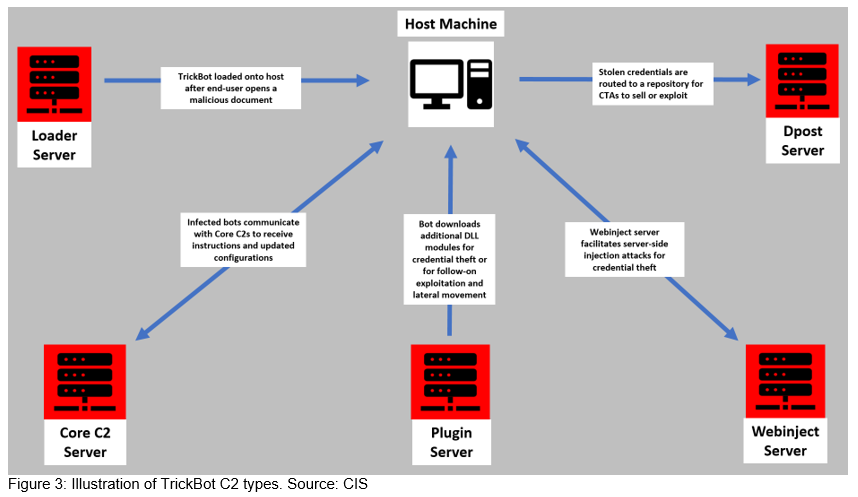
The actors behind TrickBot also make use of EmerDNS infrastructure as a backup control channel in the event of aggressive mitigation efforts by security organizations.[6] EmerDNS is associated with top level domains like [.]bazar, [.]lib, and [.]emc, and advertises it cannot be “altered, revoked, or suspended by any authority.”[7] TrickBot’s operators also frequently add and rotate infrastructure in order to evade law enforcement and security company takedown efforts.
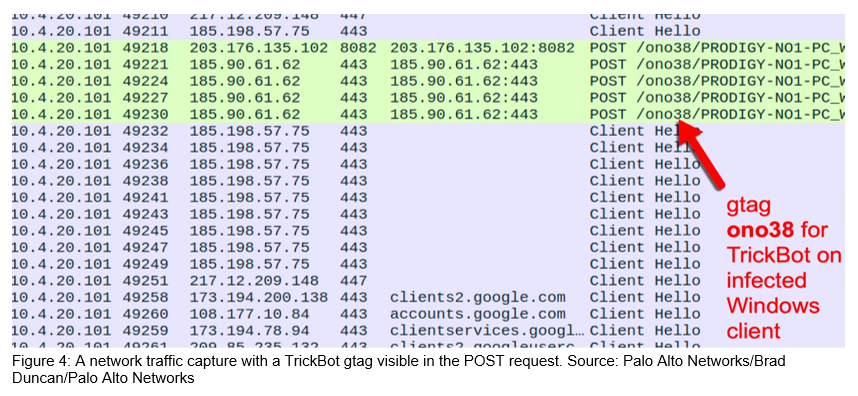
TrickBot’s operators use embedded group tags (“gtags”) to uniquely identify and track specific TrickBot campaigns. The specific gtag and a unique bot identifier are hard-coded in the Uniform Resource Identifiers (URIs) when TrickBot communicates with its C2 servers. These gtags[8] allow the operators to track TrickBot campaigns while working in tandem with other malware families or distribution methods. For example:
- Emotet: morXX
- Generic malspam: jimXX, libXX, totXX
- IcedID/Bokbot: sinXX, tinXX, winXX
- Loaders such as Amadey, Fastloader, Bazar: wmdXX, tarXX
- Ostap JavaScript loader – satXX, summXX, trgXX
Tricks on Tricks on Tricks
After the initial infection, TrickBot utilizes plugin modules to execute its many functions. These functions include credential theft, system profiling and reconnaissance, and network propagation.
Core TrickBot Modules
- Coredll – Main TrickBot module that is packed and encrypted
- Socks5Dll – Enables authenticated C2 communication with a hardcoded list of C2 servers
- LoaderDll – Ensures other modules can be successfully loaded
Credential Stealers
- InjectDll – Monitors for banking website activity and uses web injects (e.g., pop-ups and extra fields) to steal financial information
- ImportDll – Harvests browser data such as cookies and browser configurations
- Pwgrab – Steals credentials, autofill data, history, and other browser information, as well as from VNC, RDP, PuTTY, OpenSSH, and OpenVPN
- Sinj – File containing information on the online banks targeted by TrickBot and uses redirection attacks (also known as web fake injections)
- Dinj – File containing information on the online banks targeted by TrickBot and uses server-side web injections
- Socks5Dll – Enables authenticated C2 communication with hardcoded list of C2 servers
- Dpost – Routes harvested browser credentials to a predetermined IP and port number
Information Harvesting
- DomainDll – Uses LDAP to harvest credentials and configuration data from domain controller by accessing shared SYSVOL files
- OutlookDll – Harvests saved Microsoft Outlook credentials by querying several registry keys
- SqulDll – Force-enables WDigest authentication and uses Mimikatz to scrape credentials from LSASS.exe.; the worming modules use these credentials to spread TrickBot laterally across networks
- Vncservdll – Installs a VNC client onto an infected host
- Psfin – Module seeks out Point-of-Sale(POS) endpoints such as kiosks and payment terminals
System/Network Reconnaissance
- System info – Harvests system information so that the attacker knows what is running on the affected system
- Mailsearcher – Compares all files on the disk against a list of file extensions
- NetworkDll – Collects more system information and maps out the network
- dll/Perma32Dll – Profiles the UEFI/BIOS firmware of a machine; potential to persist on a compromised system even after data recovery and reimaging recovery
Network Propagation
- WormDll and ShareDll– These are worming modules that abuse Server Message Block (SMB) and Lightweight Directory Access Protocol (LDAP) to move laterally across networks
- TabDll – Uses the EternalRomance exploit (CVE-2017-0147) to spread via SMBv1
- MasrvDll32/64 – Incorporates the open-source Masscan tool to map victim networks
Advanced Persistence/Anchor
TrickBot is also able to deploy an advanced persistence capability dubbed ‘Anchor’ by security researcher Vitali Kremez. This bespoke capability is used for high-value targets where persistence is especially valuable for a CTA. This subset and its modules are detailed below:
- Anchor dns – Encrypts C2 communication as well as hides in DNS traffic to maintain stealth and persist in a compromised network
- anchorInstaller – Enables actors to establish a foothold in a victim’s network with Anchor using both 32-bit and 64-bit versions
- anchorDeInstaller – Erases any evidence that has been on a victim’s network and perform cleanup functions
- AnchorBot – Core malware component when installed on a compromised system to load additional payloads
- Bin2hex – Converts binary files to hexadecimal format
- psExecutor – Module designed to execute PowerShell commands on a compromised system
- memoryScraper – Allows Anchor to scrape a machine’s memory for Point-of-Sale (POS) data
Implications
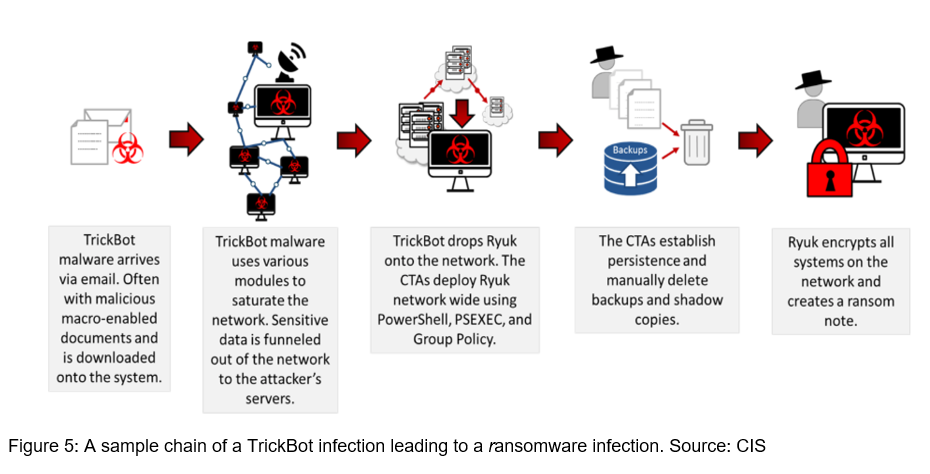
A TrickBot infection has several implications for an affected organization. Though it is worth noting that TrickBot was potentially dropped by a precursor malware, the graver threat is the possibility of a follow-on ransomware attack. If CTAs deem the compromised environment a worthy (i.e., lucrative) target, CTAs are likely to deploy a strain of ransomware, such as Conti or Ryuk across the impacted entity.
Recommendations
Preventing TrickBot Infections:
- Provide social engineering and phishing training to employees.
- Consider creating a suspicious email policy and specify all suspicious emails should be reported to the security and/or IT departments.
- Mark external emails with a banner denoting it is from an external source. This will assist users in detecting spoofed emails.
- Implement filters at the email gateway for emails with known malspam indicators, such as known malicious subject lines, and block suspicious IP addresses at the firewall.
- To lower the chance of spoofed or modified emails, implement Domain Message Authentication Reporting and Conformance (DMARC) policy and verification, starting by implementing the Sender Policy Framework (SPF) and the Domain Keys Identified Mail (DKIM) standards. (CIS Subcontrol 7.8)
- Adhere to the principal of least privilege, ensuring that users have the minimum level of access required to accomplish their duties. Limit administrative credentials to designated administrators.
- If not already being done, consider implementing an Intrusion Detection System (IDS) to detect command and control (C2) activity and other potentially malicious network activity, such as the MS-ISAC’s Albert system.
- Ensure that systems are hardened with industry-accepted guidelines, such as those provided by CIS Benchmarks™.
- Disable the use of SMBv1 across the network and require at least SMBv2 to harden systems against Network Propagation modules used by TrickBot.
Responding to a TrickBot Infection:
- Determine the infection vector (patient zero) to determine the root cause of the incident.
- Disable internet access at the affected site to help minimize the extent of exfiltration of credentials associated with external third-party resources.
- Identify and isolate the infected machines from the network.
- Heighten monitoring of SMB communication or block it between workstations, and configure firewall rules to only allow access from known administrative servers.
- Assess the need to have ports 445 (SMB) open on systems and consider limiting connections to only specific trusted hosts.
- Create clean VLANs that do not have access to infected VLANs. After the systems have been reimaged or restored from a known good backup, place them on the clean VLAN.
- Do not login to infected systems with domain or shared local administrator accounts. This is the best remediation strategy since TrickBot has several ways of gaining access to those credentials.
- As TrickBot is known for scraping both domain and local credentials, it is recommended that a network-wide password reset take place. This is best done after the systems have been cleaned and moved to the new VLAN, so the passwords are not scraped again by the malware.
Read Other Articles In this Series:
- Mimikatz: The Finest in Post-Exploitation
- Ransomware: The Data Exfiltration and Double Extortion Trends
Take Our Survey
- We would like to hear from you, please take a moment to complete this survey on this blog on Trickbot. Thank you.
References
[1] https://www.cyberscoop.com/trickbot-takedown-cyber-command-microsoft/
[2] https://twitter.com/msftsecintel/status/1251181180281450498?lang=en
[3] Please note that icanhazip[.]com is a legitimate service
[7] https://emercoin.com/en/documentation/blockchain-services/emerdns/emerdns-introduction
[8] https://intel471.com/blog/understanding-the-relationship-between-emotet-ryuk-and-trickbot/
![]()