Renew Your Ransomware Defense with CISA's Updated Guidance
By: The Cyber Threat Intelligence (CTI) team at the Multi-State Information Sharing and Analysis Center

We assess with high confidence that financially motivated ransomware groups will likely continue to target U.S. State, Local, Tribal, and Territorial (SLTT) government entities using common initial access vectors along with familiar tactics, techniques, and procedures (TTPs) for persistence, privilege escalation, and lateral movement. Their goal is to target critical data so that they can pressure public sector entities into paying a ransom.
Our assessment reflects ransomware reporting to the Multi-State Information Sharing and Analysis Center (MS-ISAC) from victims and third parties, MS-ISAC incident response cases, and open-source reporting from the cybersecurity industry.
To combat this ongoing threat, we recommend that you reference the updated #StopRansomware Guide and the Blueprint for Ransomware Defense for preventative best practices and incident response guidance.
Ransomware Threat Landscape
Many ransomware groups are known for targeting U.S. SLTTs with network-wide encryption attacks. Following encryption in these incidents, the cyber threat actors (CTAs) demand a ransom payment in exchange for a decryption key. They typically demand the ransom in various forms of cryptocurrency but primarily bitcoin.
Sometimes, ransomware attacks include a data exfiltration component where CTAs steal data. The cybersecurity industry labels these types of attacks as "double extortion" because CTAs use two forms of leverage over the victim. In an attack with both encryption and data exfiltration, CTAs often hold the decryption key for ransom and threaten to publicly release exfiltrated data if the victim doesn't pay the ransom. In other instances, some ransomware groups focus solely on data extortion and leave the encryption element out of their attacks.
The Ransomware Risk to SLTTs
CTAs have succeeded in obtaining ransom payments from SLTT entities, sometimes over $1 million. According to reporting from Chainalysis, a blockchain analysis firm, overall ransom payments to ransomware groups increased year over year from 2022 to 2023. From the beginning of 2023 through the end of June, ransomware CTAs extorted $449 million from their victims.
All these ransomware payments further incentivize more threat activity. In terms of attack frequency, the MS-ISAC observed a 74% increase in year-over-year reported incidents from Q1-Q2 2022 to Q1-Q2 2023.
Additionally, some of the most active ransomware operations across all sectors, such as “Royal” and “LockBit 3.0,” are targeting SLTTs at a high rate. Ransomware groups use different tools or TTPs from incident to incident, but the initial access vectors largely remain the same as well as the MITRE ATT&CK techniques from initial access through exfiltration and impact. This highlights the importance of defense-in-depth, where you implement overlapping defensive measures that help you to not only prevent compromises but also quickly detect and mitigate threat activity following initial access.
The graphic below shows a high-level overview for a typical ransomware attack. The various steps represent opportunities for network defenders to prevent, detect, contain, eradicate, or recover from an attack.
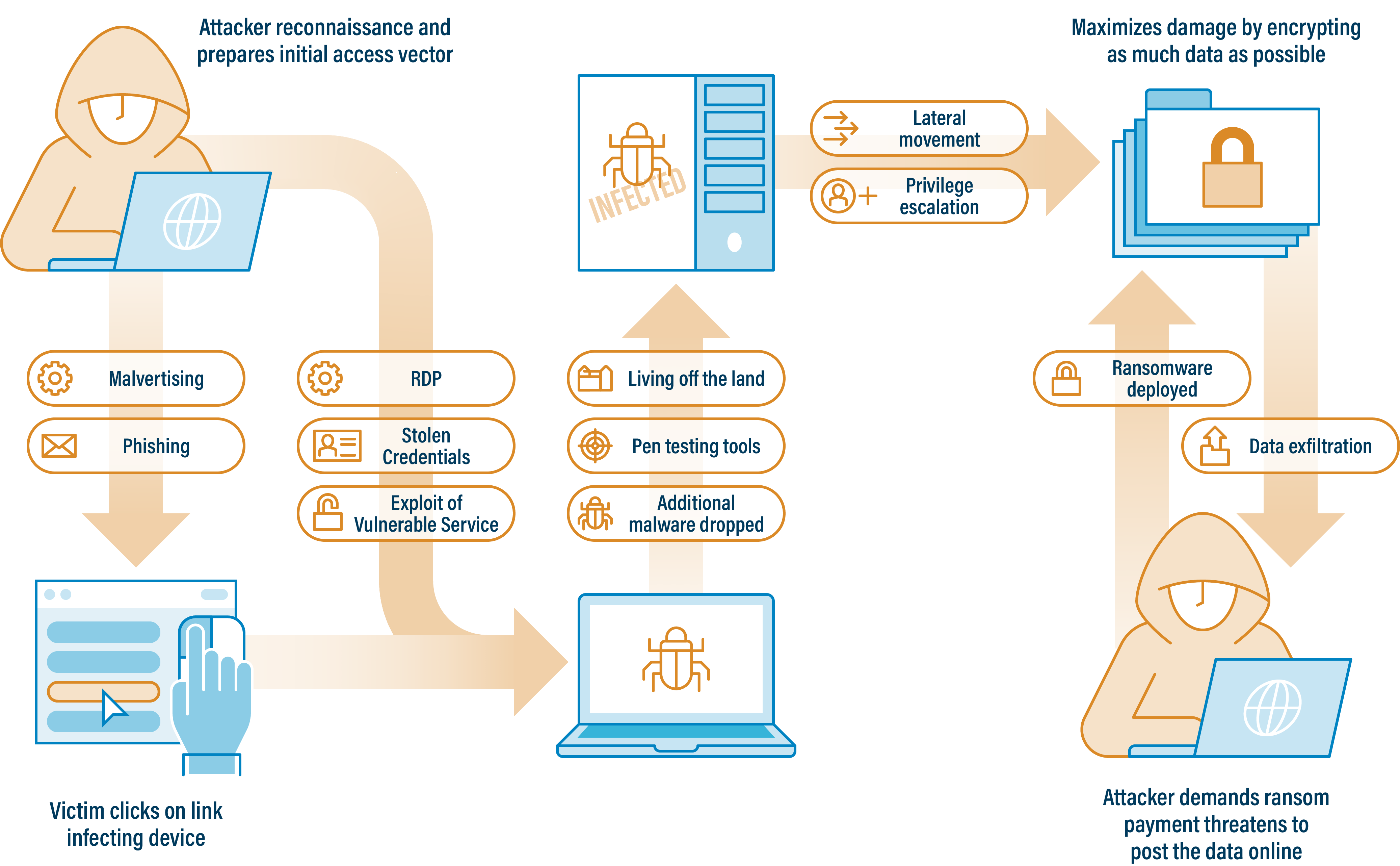
Figure 1 – High-Level Overview of a Typical Ransomware Attack.
#StopRansomware Guide
We worked with federal partners at CISA, the FBI, and the NSA to publish an updated version of the #StopRansomware Guide, which went live on May 23, 2023.
The Guide provides you with preparation, prevention, and mitigation best practices for ransomware and data extortion.
For best practices, the guide begins with the preparation stage and highlights the importance of maintaining offline, encrypted backups of critical data so that organizations can recover from malicious data encryption. Preparation also involves creating, maintaining, and regularly exercising a basic cyber incident response plan (IRP) and associated communications plans.
The best-practice guidance then covers defending against common initial access vectors, including:
- Internet-facing vulnerabilities and misconfigurations
- Compromised credentials
- Phishing
- Precursor malware infections
- Advanced forms of social engineering
- Compromises of third parties and managed service providers
Take internet-facing vulnerabilities and misconfigurations as an example. This type of initial access vector includes exposed and poorly secured remote services, such as Remote Desktop Protocol (RDP) and virtual private networks (VPNs). CTAs can achieve initial access using this vector in a number of ways, such as brute-forcing the accounts, using compromised credentials, or exploiting vulnerabilities in VPN software.
To help mitigate this activity, the #StopRansomware Guide recommends the following:
- Audit the network for systems using RDP, close unused RDP ports, enforce account lockouts after a specified number of attempts, apply multi-factor authentication (MFA), and log RDP login attempts.
- Update VPNs, network infrastructure devices, and devices being used to remote in to work environments with the latest software patches and security configurations. Implement MFA on all VPN connections to increase security. If MFA is not implemented, require teleworkers to use passwords of 15 or more characters.
The guide’s best practices section also includes other defense-in-depth measures like segmentation to cut down on lateral movement and to better protect critical network assets and data. This means employing logical or physical means with zero trust architecture to separate various business units or departmental IT resources within the organization as well as maintaining separation between IT and operational technology.
The #StopRansomware Guide then transitions from best practices to incident response guidance with the “Ransomware and Data Extortion Response Checklist.” This is a step-by-step checklist that begins with detecting and analyzing an incident. It then moves all the way to recovery and post-incident activity.
Defense-in-Depth with the Blueprint for Ransomware Defense
In addition to our efforts with the #StopRansomware Guide, the Center for Internet Security as a company has worked on other initiatives to help you defend against ransomware.
One such effort took place in 2022. As a member of the Ransomware Task Force, CIS worked with other organizations to produce the Blueprint for Ransomware Defense. The report explains how a subset of CIS Safeguards are effective in defending against common ransomware techniques.
The guidance of the Blueprint for Ransomware Defense extends what we already know from the Community Defense Model (CDM) v2.0. It shows how effective each CIS Controls Implementation Group (IG) is against the most commonly used MITRE ATT&CK techniques.
Figure 1 below illustrates that upon completing IG1, also known as “essential cyber hygiene,” you can defend against 78% of ransomware ATT&CK Techniques. If you're able to implement all CIS Controls Safeguards, the Community Defense Model Version 2.0 shows that you can defend against 92% of ransomware ATT&CK Techniques.
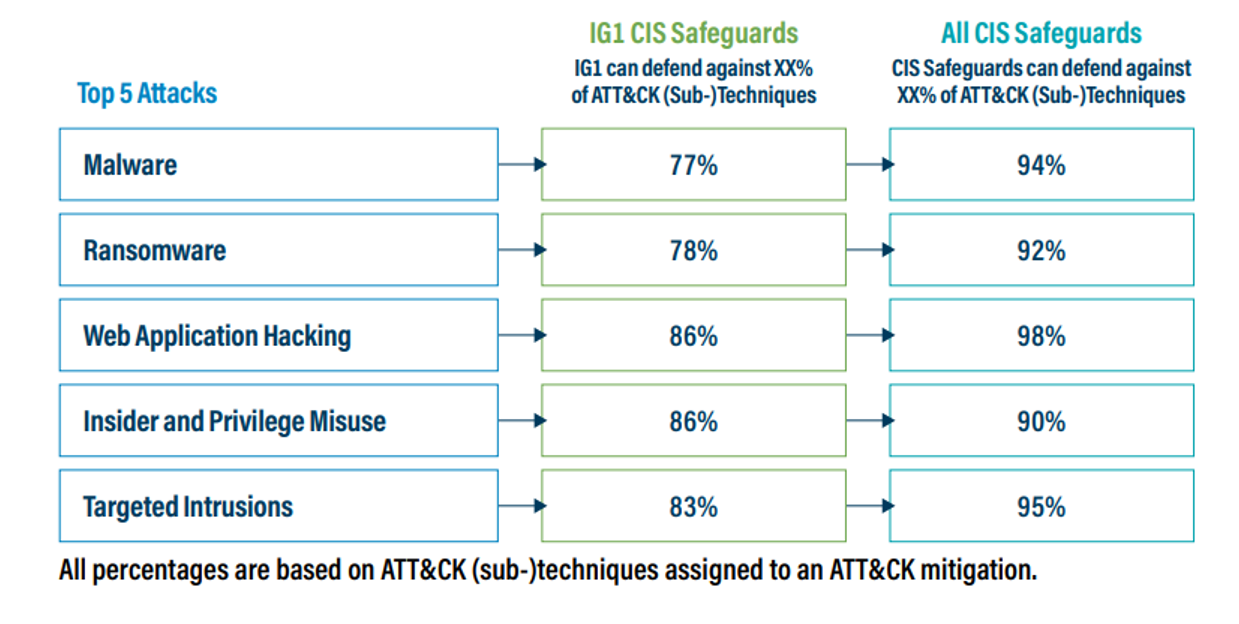
Figure 2 – Community Defense Model Version 2.0 attack pattern analysis
Preparation is Key
Properly preparing for a ransomware incident means that you must operate under the assumption that it’s not a matter of if you will be attacked but when. Under this assumption, you can begin assessing current plans and defenses before closing relevant gaps. We recommend that you reference both the updated #StopRansomware Guide and the Blueprint for Ransomware Defense to help better prepare for this pervasive cybersecurity threat.
About the Author: The Cyber Threat Intelligence (CTI) team at the Multi-State and Elections Infrastructure Information Sharing and Analysis Centers (MS-ISAC and EI-ISAC), functions as the premier CTI source for all U.S. State, Local, Tribal, and Territorial (SLTT) entities and election offices. With decades of combined experience in all types of industries, the CTI team pushes out curated SLTT-centric threat intelligence reporting as well as malicious indicators via near real-time threat feeds. This information helps SLTTs anticipate and proactively defend against emerging cyber threats and shifts in adversarial tactics, techniques, and procedures. Additional information: team tradecraft and indicator feeds.