Blog Posts
Industry news, product updates, videos, infographics, and more from CIS
Filter
598 Results Found
Solutions
Industry
261 - 270 of 598 results
Published on 01.05.2022
The following CIS Benchmarks have been updated or released for January 2022. We've highlighted the major updates below. Each Benchmark includes a...
CIS BenchmarksCIS SecureSuite
Published on 01.04.2022
Apple users rejoice! CIS Hardened Images for macOS Big Sur (11) and Catalina (10.15) are now available in Amazon Web Services (AWS) Marketplace. ...
CIS BenchmarksCIS Hardened Images
Published on 01.03.2022
Part 2 of a 2-part series By: Kathleen M. Moriarty, CIS Chief Technology Officer and active participant in the Critical Infrastructure Partnershi...
CIS Hardened Images
Published on 12.15.2021
The Windows Management Instrumentation (WMI) protocol – infrastructure on a Windows-based operating system – is used for management data and oper...
CIS Controls
Published on 12.12.2021
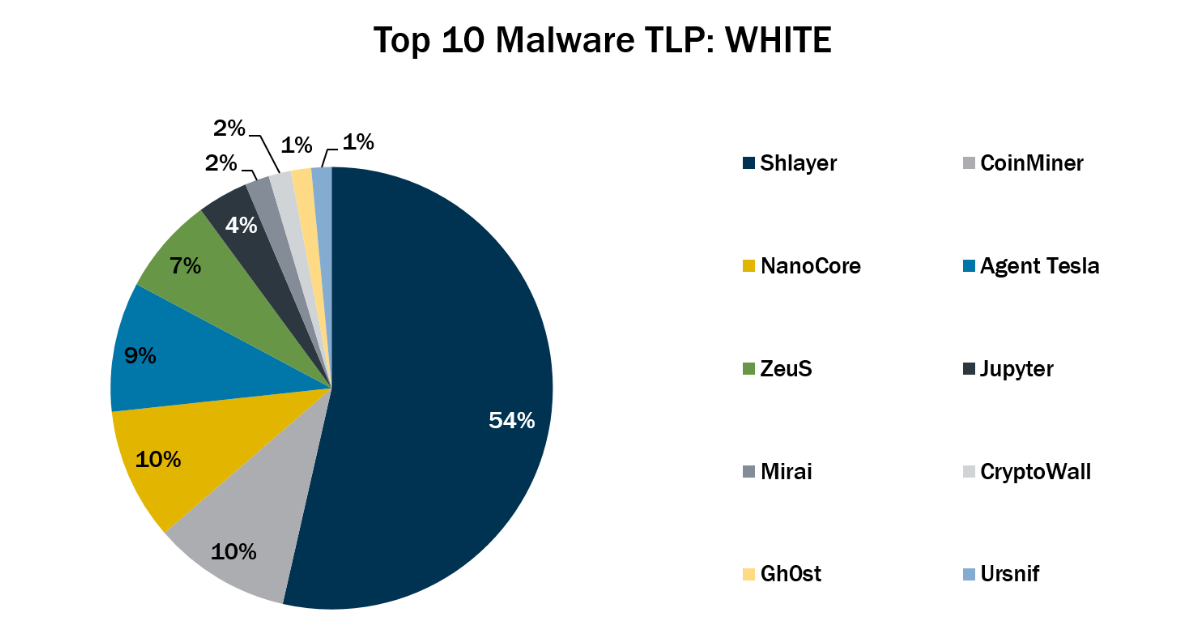
In November 2021, the Top 10 stayed consistent with the previous month with the exception of Gh0st, Mirai, and Ursnif, which returned to the Top ...
MS-ISAC
Published on 12.09.2021
The following CIS Benchmarks have been updated or released. We’ve highlighted the major updates below. Each Benchmark includes a full changelog ...
CIS BenchmarksCIS SecureSuite
Published on 12.07.2021
Part 1 of a 2-part series By: Kathleen M. Moriarty, CIS Chief Technology Officer and active participant in the Critical Infrastructure Partnershi...
Published on 12.02.2021
The selection of podcasts – on everything from gaming to movies to sports – has exploded in recent years. Whatever topic you’re interested in, ch...
Published on 12.02.2021
Many offices are operating with a hybrid of remote and in-person workspaces as the COVID-19 pandemic continues and evolves. Wherever your team is...
CIS CyberMarket
Published on 12.01.2021
This is the third article in this series by Kathleen Moriarty, CIS Chief Technology Officer. In this article, Moriarty interviews Justin Richer, ...
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More