Top 10 Malware Q2 2023
By: The Cyber Threat Intelligence (CTI) team at the Multi-State Information Sharing and Analysis Center
Published August 14, 2023

In Q2 2023, the malware on the Top 10 list remained consistent with the previous quarter, with most strains simply switching spots. CoinMiner took the number one spot in Q2, comprising 24% of Top 10 Malware incidents detected by the MS-ISAC during that time. NanoCore, ZeuS, and ViperSoftX activity increased, while Agent Tesla and Gh0st activity decreased. Additionally, although Laplas is in the same spot at eighth place, its activity increased by 2%.
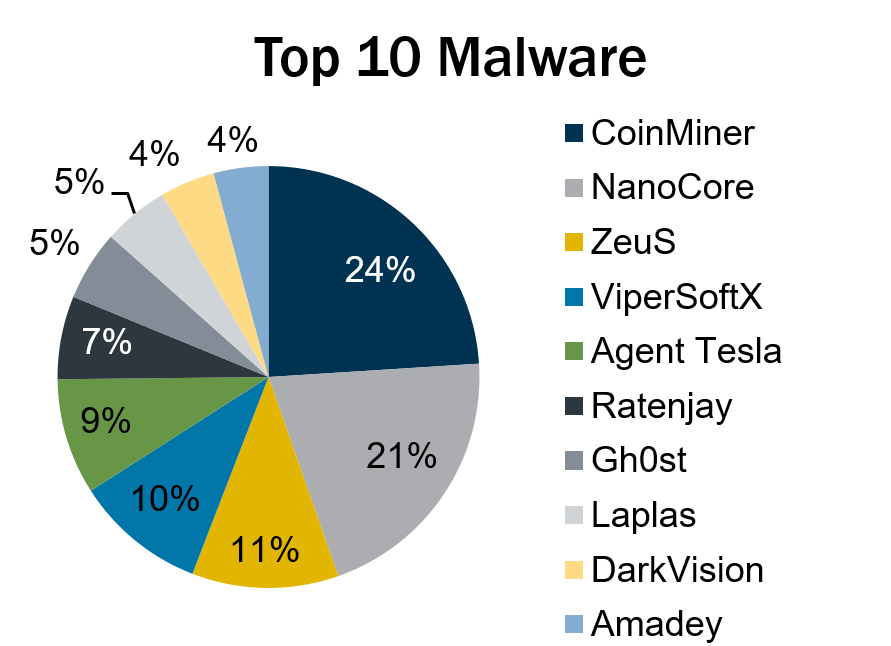
Lastly, the MS-ISAC observed Ratenjay, DarkVision, and Amadey make their first appearance on the quarterly Top 10 Malware list.
- Ratenjay is a Remote Access Trojan (RAT) dropped by other malware or downloaded as a file onto a victim’s system. It executes commands remotely and includes keylogging capabilities.
- DarkVision is a remote access toolkit sold on the dark web. It is written in C++ and targets native Windows clients. Once installed on a victim’s computer, DarkVision creates a backdoor for persistence and enables a cyber threat actor (CTA) to remotely control the system. This toolkit comes with modular plugins that are similar to add-ons. Some examples of DarkVision's add-on capabilities include keylogging, screen/microphone/webcam captures, password recovery, and reverse proxy. DarkVision is dropped by malware such as SmokeLoader.
- Amadey is a multi-functional botnet sold on criminal forums. The botnet primarily steals information from targets and downloads additional malware, such as FlawedAmmyy RAT and LockBit 3.0 ransomware.
In Q2, malware decreased by 40% compared to Q1 2023, and the Top 10 Malware decreased 65%. Furthermore, the Top 10 Malware variants comprised 39% of the total malware activity in Q2 2023, decreasing 28% compared to the previous quarter.

Malware Infection Vectors
The MS-ISAC tracks potential initial infection vectors for our Top 10 Malware each quarter based on open-source reporting, as depicted in the graph below. We currently track four initial infection vectors: Dropped, Malvertisement, Malspam, and Network. CTAs delivering malware malware also use different vectors in different contexts, and those instances are tracked as Multiple.
The CIS Community Defense Model (CDM) v2.0 can help you defend against 77% of MITRE ATT&CK (sub-)techniques associated with malware – regardless of the infection vector they use. Learn more in the video below.
In Q2 2023, the top initial infection vector changed from Dropped to Multiple due to a decrease in SessionManager2 activity, which largely drove the spike in Q1 2023 Dropped numbers. Activity levels for all three categories (Dropped, Malspam, and Multiple) decreased. The most popular combination for the Multiple initial infection vector was Malspam and Dropped. This category will likely continue to comprise a significant portion of the initial infection vectors as malware becomes more sophisticated and employs multiple methods to infect systems.
Malspam consistently represents a portion of the Top 10 Malware, as it is one of the most reliable primary initial infection vectors.
Dropped – Malware delivered by other malware already on the system, an exploit kit, infected third-party software, or manually by a cyber threat actor. DarkVision, Gh0st, and Ratenjay are the only Top 10 Malware currently using this technique.
Malspam – Unsolicited emails, which either direct users to malicious websites or trick users into downloading or opening malware. Agent Tesla and NanoCore are currently using this technique.
Multiple – Malware that currently uses at least two vectors, such as Dropped or Malspam. Currently, Amadey, CoinMiner, Laplas, ZeuS, and ViperSoftX are malware utilizing multiple vectors.
Top 10 Malware and IOCs
Below are the Top 10 Malware ranked in order of prevalence. The respective indicators of compromise (IOCs) are provided to aid in detecting and preventing infections from these malware variants. The below IOCs can be used for threat hunting but may not be inherently malicious for blocking purposes.
1. CoinMiner
CoinMiner is a cryptocurrency miner family that typically uses Windows Management Instrumentation (WMI) to spread across a network. Additionally, it often uses the WMI Standard Event Consumer scripting to execute scripts for persistence. However, the malware’s capabilities may vary since there are multiple variants. CoinMiner spreads through Malspam or is dropped by other malware.
MD5 Hashes
90db8de2457032f78c81c440e25bc753
268f9b1d96c6359dd88cfba68d59eb25
d39880431013527b5595b70869450749
a4c70c143cf88e4f3065f44e3951a09a
4850001d63b0eea395e4f60a38d5c59d
5c1a5f4a597d915702a0f598f49088cc
1682bfcdc5c616d64b81da79af2b767f
0e00b83f809d108430aaaea1fe6bbc71
File
odbc32[.]exe
Sysqamqqvaqqd[.]exe
2. NanoCore
NanoCore is a RAT spread via Malspam with an attachment, such as a malicious Excel XLS spreadsheet. NanoCore accepts commands to download and execute files, visit websites, and add registry keys for persistence.
Domains
december2n[.]duckdns[.]org
december2nd[.]ddns[.]net
MD5 Hashes
5c0f39d2e1d01ef7346ec7d1667b2cca
ebb4b4afb2d1c564df3290a5217769a2
b45c85ea03fb63e30414d6ec52606cae
69f724e06ca173de33d022719bb1be26
3. ZeuS
ZeuS is a modular banking Trojan that uses keystroke logging to compromise credentials when a victim visits certain banking websites. Since the release of the ZeuS source code in 2011, many other malware variants have adopted parts of its codebase, which means that incidents classified as ZeuS may actually be other malware using parts of the original ZeuS code.
IP Addresses
54[.]38[.]80[.]220
4. ViperSoftX
ViperSoftX is a multi-stage cryptocurrency stealer spread within torrents and filesharing sites, typically as a malicious crack for popular software.
Domains
uwfmz[.]com
vewga[.]com
vqjumd[.]com
wopsyqi[.]com
xcakdisve[.]com
xsdmcy[.]com
xvfnhw[.]com
yjghwcxel[.]com
ysawrbi[.]com
zcdkjqwgn[.]com
zeiyusv[.]com
zjyhc[.]com
zqiwma[.]com
5. Agent Tesla
Agent Tesla is a RAT that targets Windows operating systems. It is available for purchase on criminal forums as malware-as-a-service. It has various capabilities depending on the version purchased, including capturing keystrokes and screenshots, harvesting saved credentials from web browsers, copying clipboard data, exfiltrating victim files, and loading other malware onto the host.
MD5 Hashes
aa6e15b27f3b0ab1033505b952597ca2
72ca702d9c009f895b15bc4101b29978
a5404f71aa5247d85c82d7be23778979
9cd2d4d852f7440298765cb8b1572498
50d4ad9c7025d9f194ced783a8a9e3ea
a5bd7081d929485e9619fdd711dff8a9
2e2dfc4fe680d5b1460efa9afc53df4e
6. Ratenjay
Ratenjay is a Remote Access Trojan (RAT) dropped by other malware or downloaded as a file onto a victim’s system. It executes commands remotely and includes keylogging capabilities.
IP Addresses
167[.]235[.]141[.]81
94[.]158[.]247[.]101
7. Gh0st
Gh0st is a RAT used to control infected endpoints. Gh0st is dropped by other malware to create a backdoor that allows an attacker to fully control the infected device.
MD5 Hashes
77bd9926a4b41c14259e20c1f90e22aa
c50fa53d302bc36d0cb26e618e9f5fb7
a5825db412727d2c0356333700745e21
f4482b2d7e963e647ebcd74a6385b9e0
f1d2f3a206d3b46fd23ff8612bd01ca8
3d80407a47f1e8f32a987cf1bffc39c6
9e6c45b6b8b20bf3c5959dbba8f27117
URLs
hxxp://datacache[.]cloudservicesdevc[.]tk/picturess/2023/223[.]114[.]txt
hxxp://datacache[.]cloudservicesdevc[.]tk/picturess/2023/LiveUpdate[.]exe
hxxp://datacache[.]cloudservicesdevc[.]tk/picturess/2023/LiveUpdate360[.]dat
hxxp://datacache[.]cloudservicesdevc[.]tk/picturess/2023/Media[.]xml
hxxp://datacache[.]cloudservicesdevc[.]tk/picturess/2023/SqlVersion9[.]dll
hxxps://api[.]youkesdt[.]asia/admin/down/hash/79b7c6ed-c4d8-4b36-b1cd-f968e6570010
8. Laplas
Laplas is a clipper malware spread by other malware. Currently, Laplas is spread by SmokeLoader, which is delivered via phishing emails containing malicious documents.
Domains
Clipper[.]guru
Nerf-0150-unknown[.]guru
IP Addresses
163[.]123[.]142[.]220
185[.]174[.]137[.]94
185[.]223[.]93[.]251
212[.]113[.]106[.]172
45[.]159[.]189[.]105
79[.]137[.]195[.]205
9. DarkVision
DarkVision is a remote access toolkit sold on the dark web. It is written in C++ and targets native Windows clients. Once installed on a victim’s computer, it creates a backdoor for persistence and enables a CTA to remotely control the system. This toolkit comes with modular plugins that are similar to add-ons. Some examples of DarkVision's add-on capabilities include keylogging, screen/microphone/webcam captures, password recovery, and reverse proxy. DarkVision is dropped by malware such as SmokeLoader.
MD5 Hash
5bf6dda87c399945bfdae0c390523f6c
126e11df3a5c5aa56461d6a490b2f2aa
51cf4802354c64cf1097ae46b63f7fe7
10. Amadey
Amadey is a multi-functional botnet sold on criminal forums. The botnet primarily steals information from targets and downloads additional malware, such as FlawedAmmyy RAT and LockBit 3.0 ransomware.
Domains
ama[.]hostiko[.]link
nestlecareers[.]cf
nestlehosts[.]xyz
IP Addresses
78[.]46[.]242[.]112
79[.]137[.]203[.]19
About the Author: The Cyber Threat Intelligence (CTI) team at the Multi-State Infrastructure Information Sharing and Analysis Centers (MS-ISAC) functions as the premier CTI source for all U.S. State, Local, Tribal, and Territorial (SLTT) entities. With decades of combined experience in all types of industries, the CTI team pushes out curated SLTT-centric threat intelligence reporting as well as malicious indicators via near real-time threat feeds. This information helps SLTTs anticipate and proactively defend against emerging cyber threats and shifts in adversarial tactics, techniques, and procedures. Additional information: team tradecraft and indicator feeds.
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.