Breaking Down the BlackCat Ransomware Operation
The BlackCat ransomware group is making quite a name for itself. In a FLASH alert published in April 2022, the FBI revealed that the operation had infected more than 60 victims since first surfacing in mid-November 2021.
The Multi-State Information Sharing and Analysis Center (MS-ISAC) has seen this uptick in BlackCat activity on its end, too. Indeed, a member organization of the MS-ISAC recently underwent an incident response after a locked account revealed that an unknown cyber threat actor (CTA) was remotely controlling several of their PCs.
The incident began when the point of contact for the member organization received a report from an employee noting that his account was locked and that he couldn't access his email. After a password reset didn't fix the issue, the employee went into the office. There, the employee saw that an unknown actor was remotely controlling several of the PCs. He told the point of contact what was going on. At that point, the point of contact said that they would head into the office to investigate further.
On their way in, the point of contact received a call notifying them that another organization to which the member organization's network was connected had suffered a ransomware attack. The point of contact subsequently detected several encrypted files within their organization upon arrival. They also reviewed the Task Scheduler and discovered evidence that the ransomware had attempted to reinfect and spread. In the process, they learned that the ransomware had wiped their organization's backups.
The member's organization ultimately succeeded in restoring the domain controllers and a couple of servers. They weren't able to recover anything else. During the course of an internal investigation, the point of contact learned that the BlackCat group had likely been responsible for the attack.
Unpacking BlackCat’s Technical Details
In its FLASH alert, the FBI explained that BlackCat aka "AlphaV" ransomware gains initial access to a targeted system using compromised user credentials. It leverages that access to compromise user and admin accounts in the Active Directory. This enables the threat to configure malicious Group Policy Objects (GPOs) through the Windows Task Scheduler for the purpose of deploying its ransomware payload.
Upon initial deployment, BlackCat disables security features within the victim's network so that it can exfiltrate information prior to execution. It then uses several batch and PowerShell scripts to proceed with its infection. These include "est.bat," which copies the ransomware to other locations, and "drag-and-drop-target.bat," which launches the ransomware executable for the MySQL Server.
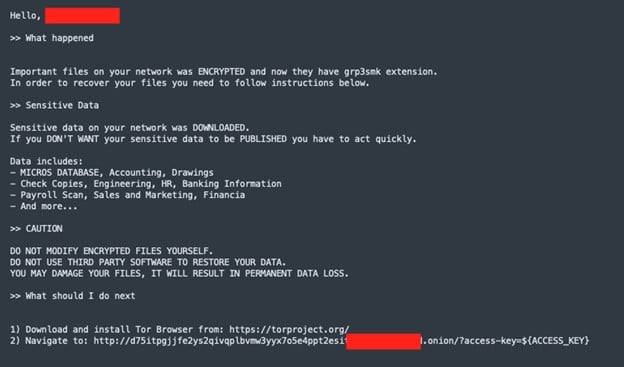
BlackCat ransom note (Source: AT&T Alien Labs Research)
How BlackCat Stands Out from Other Ransomware
BlackCat stands out among other ransomware operations for the following reasons: it's a possible rebranding of DarkSide, it's written in Rust, it pays affiliates a comparatively larger share than similar schemes, and it's responsible for launching one of the first public data leaks sites. Let's explore each of these factors below.
Possible Rebranding of DarkSide
The FBI noted in its FLASH alert that BlackCat's operators include many developers and money launderers who originated from the DarkSide Ransomware as a Service (RaaS) platform. As such, the BlackCat group already has experience with successfully targeting large enterprise networks. It's also familiar with the consequences of not being selective with their targets, insight which they can use to ensure their longevity.
DarkSide learned this lesson in the spring of 2021 when it disrupted Colonial Pipeline Company for six days, thereby attracting the attention of the FBI. Just a few days after the attack, an unknown actor seized the ransomware operation's servers and drained its cryptocurrency funds from its accounts. As a result of the hijacking, DarkSide personnel could not access their dark web data leaks site and couldn't pay their affiliates. Shortly after this setback, a member of the REvil RaaS operation posted a message on a cybercrime forum announcing DarkSide's retirement, reported KrebsonSecurity.
Jesse Adam, a Cyber Threat Intelligence Analyst at the MS-ISAC, revealed that there might be another reason for the name change. Organizations oftentimes track different infrastructure, adversary-identifying information, intrusions, and tactics, techniques, and procedures (TTPs) from one another. As a result, they can arrive at different perspectives/assessments where they do not feel comfortable attributing based on other organizations' findings.
"Cybercrime researchers are naming their profiles based on their set of data, which may lead to the creation of a new name if the threat actor is using new tactics or different malware," Adam pointed out. "Sometimes, a threat actor's name changes also based on information that geolocates to their location and/or based on the organization that names them. This is to say that multiple factors, not just one, might have informed DarkSide's transition to BlackCat."
Written in Rust
The April 2022 FLASH alert revealed that BlackCat is written in Rust. In the FBI's words, Rust is "considered to be a more secure programming language that offers improved performance and reliable concurrent processing." It provides attackers with several advantages over using another programming language.
"Rust enables BlackCat to target a wider range of systems including both Windows and Linux," Adam said. "It also makes BlackCat into a very complex ransomware with efficient algorithms to aid in the encryption process of breached systems. Remember that Rust is built for fast performance, powerful web application development, and memory management resolution. If that weren't enough, Rust aids in making the ransomware harder to analyze in sandbox environments. That's because many security solutions are still catching up in their ability to analyze threats written in Rust and other more modern languages."
There's a potential disadvantage to the BlackCat gang writing their payload in Rust. As of this writing, there aren't too many malware or ransomware strains written in Rust. The Hacker News did report on one such threat dubbed "Ficker Stealer" in August 2021. Depending on which security systems they have, defenders might be able to use artificial intelligence to spot Rust code and issue an alert of a potential BlackCat infection. But that's not necessarily what most organizations are on the lookout for these days.
The Share that BlackCat’s Operators Pay Affiliates
As a RaaS operation, BlackCat's business model revolves around letting other attackers use their ransomware, conduct their own campaigns, and keep a percentage of what they earn. Most RaaS operations allow affiliates to keep 70% of their profits. With BlackCat, however, affiliates can expect to keep 80-90%.
"BlackCat's split is a huge advantage in terms of advertising," Adam explained. "Many groups that use RaaS as their business model need to advertise their service to be successful. Some turn to a marketing and PR team to get the word out on cybercrime forums and other back channels of the web. But this affiliate share does much of that for them. Word of mouth among the affiliates themselves can carry BlackCat forward."
That doesn't bode well for organizations, according to Adam.
"BlackCat's affiliates aren't sitting on their huge payouts. They're taking them and renting out more of BlackCat's services. They might also be paying other cybercriminals to use their services. In other words, this scheme allows attackers to do more bad things at a bigger scale."
Launched One of the First Public Data Leaks Sites
Acknowledging its popularity among affiliates, it's perhaps unsurprising that BlackCat has done something that no other RaaS operation has done: it has created a data leaks website on the public internet. Other groups set up these types of sites on the dark web. The purpose of these sites is to prove that victims have suffered a data breach so that they'll be more inclined to pay the attackers.
Because these sites are available on the dark web, however, their visibility is largely limited to victims, other cybercriminals, and security researchers. BlackCat's public site changes the game by making its site available to everyone – including current and potential customers, shareholders, and reporters. As KrebsonSecurity wrote in June 2022, this tactic can therefore pressure victims even further to fulfill the attackers' demands.
How Organizations Can Defend Against BlackCat
Organizations aren't powerless when it comes to defending against BlackCat. SLTT-affiliated organizations can join the MS-ISAC and use their membership to deploy Malicious Domain Blocking & Reporting (MDBR), Endpoint Security Services (ESS), and Albert Network Monitoring and Management, among other no-cost protective services. Meanwhile, organizations of every sector can take precautions like regularly creating and testing up-to-date offline backups, using multi-factor authentication (MFA), conducting user awareness training on an ongoing basis, and securing remote desktop protocol (RDP) to make a big impact. For further defense, organizations should download the CIS Critical Security Controls (CIS Controls) for prescriptive and prioritized cyber defense guidance. Per the Community Defense Model (CDM), organizations can use Implementation Group 1 (IG1) of the CIS Controls to achieve essential cyber hygiene against ransomware and other common attacks.
Want clear and actionable steps for defending against ransomware? Check out the video below.
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.