CIS Critical Security Control 11: Data Recovery
Overview
Establish and maintain data recovery practices sufficient to restore in-scope enterprise assets to a pre-incident and trusted state.
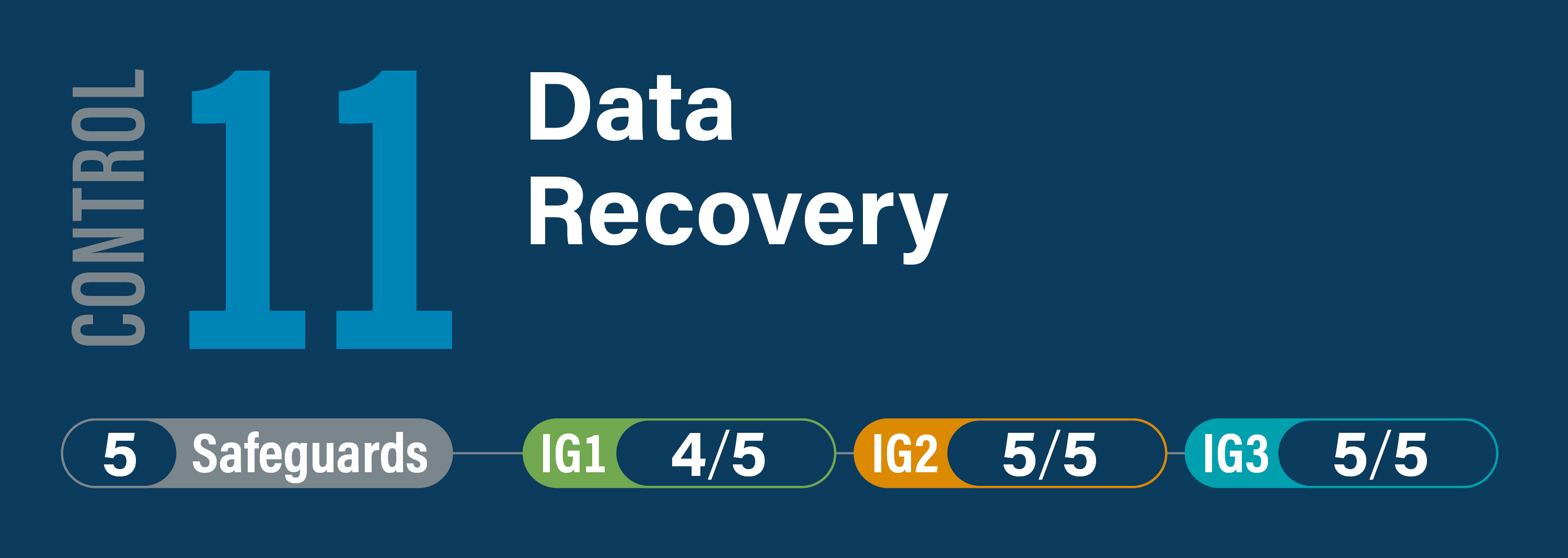
Establish and maintain data recovery practices sufficient to restore in-scope enterprise assets to a pre-incident and trusted state.
