New on AWS Marketplace: Ubuntu Linux 18.04 and Amazon Linux 2 CIS Hardened Images
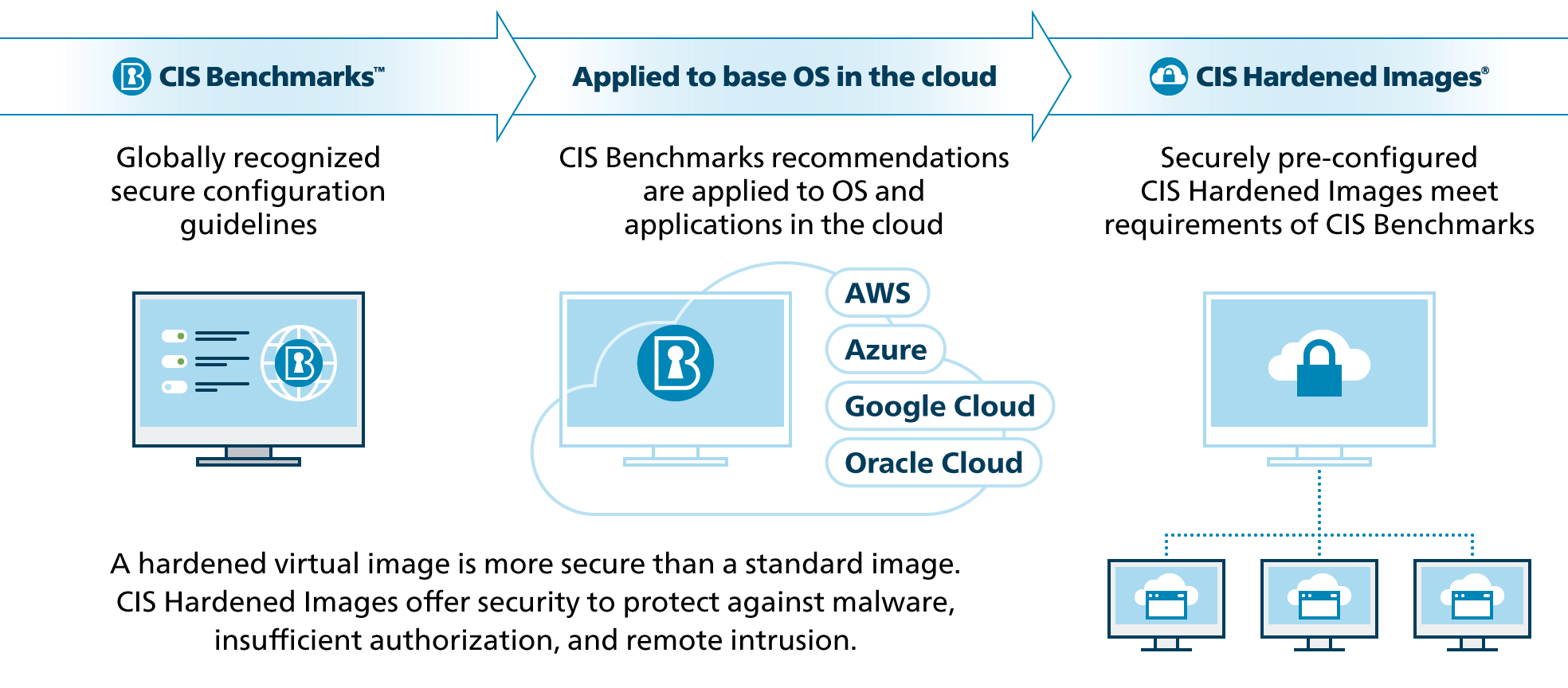
CIS just released two new CIS Hardened Images™ for operating systems on AWS Marketplace: Ubuntu Linux 18.04 and Amazon Linux 2. These images are preconfigured to meet security recommendations from the related CIS Benchmarks™. Secure configurations help safeguard organizations from common cyber threats. CIS Benchmarks are consensus-developed configuration guidelines downloaded over a million times per year. CIS applies these recommendations to AMI’s in the cloud so you can start secure and stay secure.
Securing Ubuntu Linux 18.04
In order to develop the new CIS Benchmark for Ubuntu Linux 18.04, we worked with the global community to identify, test, and develop configuration best practices. Via our collaboration platform, CIS Workbench, the community was able to discuss security topics specific to Ubuntu Linux 18.04. CIS implements those practices in creating the images for cloud environments on AWS.
Examples of recommendations found in the CIS Benchmark that was used to configure this CIS Hardened Image include:
- Ensure GPG keys are configured – It is important to ensure that updates are obtained from a valid source to protect against spoofing that could lead to the inadvertent installation of malware on the system.
- Ensure permissions on bootloader config are configured – Setting the permissions to read and write for root only prevents non-root users from seeing the boot parameters or changing them. Non-root users who read the boot parameters may be able to identify weaknesses in security upon boot and be able to exploit them.
- Ensure AIDE is installed – By monitoring the file system state compromised files can be detected to prevent or limit the exposure of accidental or malicious misconfigurations or modified binaries.
Launch the CIS Hardened Image for Ubuntu Linux 18.04 on AWS
Securing Amazon Linux 2
- Ensure only strong ciphers are used – Weak ciphers that are used for authentication to the cryptographic module cannot be relied upon to provide confidentiality or integrity, and system data may be compromised.
- Ensure access to the su command is restricted – Restricting the use of su, and using sudo in its place, provides system administrators better control of the escalation of user privileges to execute privileged commands. The sudo utility also provides a better logging and audit mechanism, as it can log each command executed via sudo, whereas su can only record that a user executed the su program.
- Ensure bogus ICMP responses are ignored – Some routers (and some attackers) will send responses that violate RFC-1122 and attempt to fill up a log file system with many useless error messages.
These recommendations were applied to a virtual machine image of Amazon Linux 2, resulting in the pre-configured CIS Hardened Image for Amazon Linux 2 available in AWS Marketplace.
Launch the CIS Hardened Image for Amazon Linux 2 on AWS
Hardening Systems in the Cloud
Working in cloud environments offers immense flexibility, portability, and computing power. Security in the cloud is just as important as it is for on-premises environments. CIS Hardened Images offer one way to quickly implement cyber defense in the cloud. Because they are pre-configured according to a secure standard – the CIS Benchmarks – the security is baked in from the start. Launch one on AWS, Microsoft Azure, or Google Cloud Platform.