Mapping Your Way To Compliance With Cybersecurity Frameworks
Organizations today need to comply with multiple policy, regulatory, and legal security frameworks. Complying with all of these frameworks can be difficult and time consuming. Your cybersecurity program can work more efficiently when you know how to “map” them all together.
Efficiencies for Cybersecurity Compliance
Today’s IT and information security professionals can find themselves tasked with satisfying myriad regulatory frameworks. But the primary responsibility for cybersecurity professionals is to keep their organization’s assets and data safe from an attack. A truly efficient approach protects the organization while also meeting compliance requirements. This is where the CIS Controls and CIS Benchmarks can help.
While frameworks and standards usually explain “what” you need to do to achieve compliance, the organizational policies and workflows of the CIS Controls, plus the detailed configuration checks of CIS Benchmarks, go a few steps further. For example, they will tell you that by implementing the CIS Control 3.1, you are also complying with specific CMMC, MITRE ATT&CK, NIST, and PCI DSS requirements.
A Global Standard for Cybersecurity Protection
The CIS Controls and CIS Benchmarks are recognized as industry standards for cyber protection around the world:
- PCI recommends CIS standards for hardening
- The DoD Cloud Computing Security Requirements Guide references CIS Benchmarks as an acceptable alternative to the STIGs and SRGs, Section 5.5.1
- The CIS Controls are referenced by the National Governors Association and NIST
- FedRAMP lists CIS Benchmarks if U.S. government configuration guidelines aren’t available for a specific platform
- The CIS Controls and CIS Benchmarks complement the HIPAA security rule and contain many of the same provisions
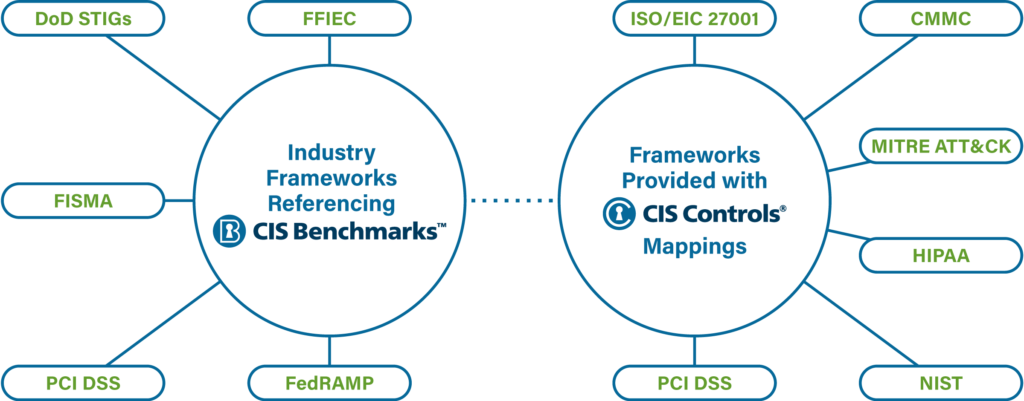
The CIS Controls are “mapped” to other frameworks, such as NIST and PCI DSS, while the CIS Benchmarks are “referenced” as being acceptable standards. Additionally, CIS Benchmarks recommendations are mapped to the CIS Controls.
Tools for Compliance Mapping and Tracking
Learn how the CIS Controls map to popular industry frameworks with the CIS Controls Navigator. Once you know which frameworks to measure against, the next step is to manage the prioritization and implementation of those frameworks.
The CIS Controls Self Assessment Tool (CIS CSAT) and the on-prem CSAT Pro with additional features, enables security teams to track and prioritize their implementation of the CIS Controls and sub-controls (now known as Safeguards). You can determine which CIS Controls are applicable to your organization, and if they’ve been assigned, implemented, automated, documented, and reported. It also helps you align with other security frameworks.
An “On-ramp” to Compliance: CIS SecureSuite Membership
The CIS Controls and CIS Benchmarks provide an “on-ramp” toward compliance with these other security frameworks. That’s because they’re a good starting point for securing your organization while moving you toward compliance.
Many resources and tools, like CIS CSAT Pro, for implementing the cybersecurity recommendations of CIS Controls, are only available through a CIS SecureSuite Membership. It is a cost-effective way to achieve compliance and ensure the protection of data assets.
Learn more about all the benefits of being a member in our next demo.
![]()