Protecting Against Potential Russian Cyber Attacks
Whether you provide services to citizens as a U.S. state, local, tribal, or territorial (SLTT) government entity, or you’re marketing products and services, an effective cyber defense is critical to strengthening your organization’s resilience in the wake of a cyber attack.
As the potential for Russian cyber attacks increases, CIS has developed practical guidance for both SLTTs and private sector organizations.
Guidance for U.S. State, Local, Tribal, and Territorial (SLTT) Entities
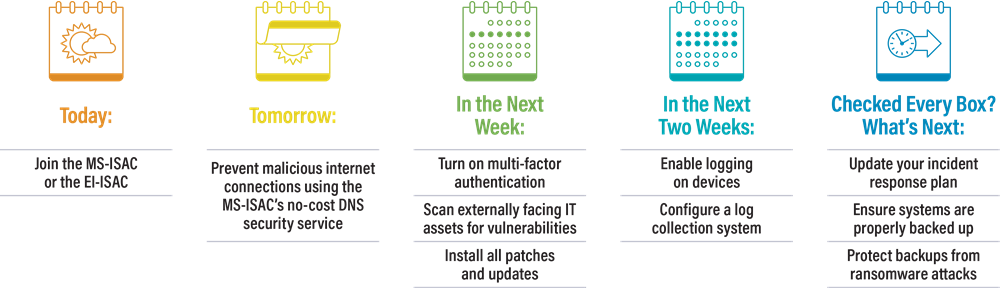
What You Should Do Today
Join the MS-ISAC
Level of Effort: 5 minutes to sign up online
Why: The MS-ISAC is the nation’s focal point for cyber threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) governments. In cooperation with the Cybersecurity and Infrastructure Security Agency (CISA), the MS-ISAC offers a 24x7x365 security operations center, incident response services, cyber threat intelligence, advisories and notifications, and several products and services, many of which are provided at no cost to SLTTs.
How: Sign up to join the MS-ISAC
Cost: No cost for SLTTs (State, Local, Tribal, and Territorial Entities)
What You Should Do Tomorrow
Stop malicious internet activity with a service provided by the MS-ISAC
Level of Effort: 15 minutes to redirect Domain Name System (DNS) resolution. No other configuration or maintenance is required.
Why: Each DNS request from an organization will be passed through our Malicious Domain Blocking & Reporting (MDBR) service, which will automatically block requests for malicious domains. This prevents hosts from connecting to known or suspected malware, phishing, ransomware, or command and control systems, protecting your environment.
How: The process to get started is automated, sign up for MDBR
Cost: No cost for SLTTs that are MS-ISAC members
What You Should Do in The Next Week
Turn on multi-factor authentication (MFA) for any system that offers it
Level of Effort: For Software as a Service (SaaS) (e.g., Google Workspace, Microsoft 365, and others) it may be as fast as 10 minutes to implement. Others may be more involved. Some user training may be required.
Why: Attackers continue to steal credentials (username and password) from users through phishing attacks and other social engineering tactics. Brute force attacks (using a computer to rapidly try multiple username and password combinations until a match is found) is also a common tactic. MFA protects an organization by up to 96% against these attacks.
How: Do a quick inventory of all systems in use and determine what offers MFA. Whether it is sending users a text message (SMS), or more preferably the use of an app (such as a push to a mobile device or an app like Google Authenticator or Microsoft Authenticator), enable it for all users.
Cost: In most cases, there is no cost to enable MFA
Obtain a recent vulnerability scan of externally facing IT assets and install all possible patches and updates
Level of Effort: Minimal, but this depends on the size and complexity of the environment. Within a few hours, a scan could be done and results analyzed and prioritized for remediation efforts. Exercise caution when scanning operational technology (OT) environments as aggressive scanning may cause systems to become unavailable. Ensure everything that can be updated and patched within your environment has been.
Why: Adversaries will be using historical vulnerability information available on the internet as well as launching their own scans to find exploitable vulnerabilities. Your organization should focus on finding and fixing these before the adversary does.
How: SLTTs can request a no-cost vulnerability scan via the CISA Cyber Hygiene (CyHy) program by emailing CISA at [email protected]. Due to the number of requests received by CISA, there may be a delay. SLTTs can also contact the Center for Internet Security (CIS) for vulnerability scanning.
Cost: No cost for use of CISA CyHy. CIS will offer vulnerability scanning of SLTTs' externally facing IT assets at no cost while in this heightened state of alert. Contact CIS at [email protected]
What You Should Do in the Next Two Weeks
Enable logging on any device that is capable and configure a log collection system
Level of Effort: Minimal – most infrastructure devices and systems have a native logging capability. IT administrators may be able to enable this across all devices using centralized management tools such as Group Policy Objects (GPOs) or others. A system must be set up to collect and store these logs, which could be as simple as a desktop computer with an external hard drive to start.
Why: Logs are what incident response and forensic teams will need in order to recreate an attackers’ footsteps in your network. Logs will help put the puzzle together of who the adversary was, how they got in, how long they were in, and what they did while inside. Logs also help identify previously undetected events or suspicious activity that did not trigger a signature-based defense system.
How: Set up a system (can be a desktop or server running Windows or Linux, although we recommend Linux) and use an open-source tool such as rsyslog to listen for and store logs sent to it. Configure devices to send logs to your syslog server (generally over UDP port 514, but some can be customized). Confirm logs are being received and stored on the system or external hard drive.
Cost: Minimal. You may be able to repurpose a computer for this and external storage if necessary. Use an operating system such as Ubuntu (no cost) and rsyslog (no cost) to get started.
What’s Next?
If you’ve already completed the suggestions above, here are two other important recommendations.
Develop or update an incident response (IR) plan
Level of Effort: Minimal – create a document that describes your organization’s plan for responding to and recovering from a cyber attack.
Why: Responding to a cyber attack is stressful, even for well-resourced and experienced teams. Developing procedures and establishing contacts with law enforcement, the MS-ISAC, CISA, your cyber insurance provider, and others should not wait until an emergency. Having a plan to identify roles, responsibilities, and key decision points is critical to your success.
How: CIS has a checklist available to get you started: Cyber Incident Checklist. CISA also has a template written for federal civilian agencies, but it provides a good overview for SLTTs on sections you will want to consider adding to your plan: Cybersecurity Incident & Vulnerability Response Playbooks
Cost: None
Ensure systems are properly backed up and backups are protected from ransomware attacks
Level of Effort: Moderate to significant depending on size and complexity of the environment, amount of data requiring backups, and business recovery objectives.
Why: Beyond the obvious need to have backups to restore in the event of a system crash or data corruption, having backups that can withstand a ransomware attack is critical and requires some additional considerations.
How: For more information on backup best practices, see the security spotlight on backups here: Election Security Spotlight – Backups and the co-authored ransomware guide by the MS-ISAC and CISA here: Ransomware Guide.
Cost: Minimal to significant
Resources from the Cybersecurity & Infrastructure Security Agency
For resources from our colleagues at CISA, please also see their Shields Up webpage.
Cyber Incident Support
Our expertly trained Cyber Incident Response Team (CIRT) is here to help. If your SLTT organization experiences a cybersecurity incident we encourage you to report an incident.
For further questions or concerns the MS-ISAC Security Operations Center (SOC) is available 24x7x365 to assist via phone or email.
Phone: 866-787-4722
Email: [email protected]

Learn more about joining the MS-ISAC here.