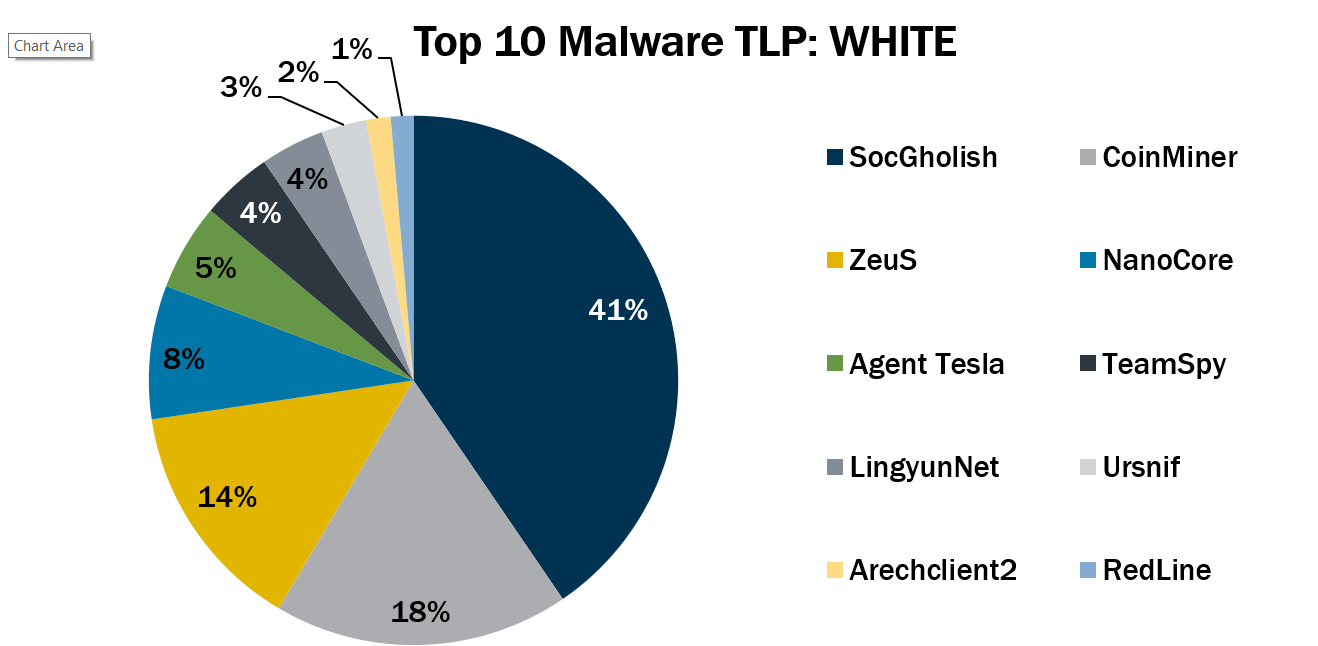
Top 10 Malware September 2022
In September 2022, the Top 10 Malware line-up stayed relatively consistent compared to the previous month. Most malware changed their rankings in the list, and new malware took the last three spots.
This month, Arechclient2, RedLine, and Ursnif returned to the Top 10 malware.
- Arechclient2 is a NET RAT with numerous capabilities, such as profiling victim systems, stealing information, and launching a hidden secondary desktop to control browser sessions.
- RedLine is an infostealer that is available for purchase on cybercriminal forums. The malware typically targets information such as credentials, cookies, banking information, and cryptocurrency wallet information. Furthermore, RedLine has remote functionality that enables it to download malicious tools or drop additional malware.
- Ursnif is a banking trojan that is spread through malspam. Ursnif can obfuscate itself against anti-malware software, and it collects victim information from login pages and web forms.
The Top 10 Malware variants comprise 71% of the total malware activity in September 2022, increasing 24% from August 2022.

Malware Infection Vectors
The Multi-State Information Sharing Analysis Center (MS-ISAC) tracks potential primary infection vectors for our Top 10 Malware each month based on open-source reporting, as depicted in the graph below. We currently track four initial infection vectors: Dropped, Malvertisement, Malspam, and Network. The MS-ISAC has not had any malware in the Top 10 use the initial infection vector Network in the past year. Some malware employ different vectors in different contexts and are thus tracked as Multiple.
In September 2022, Multiple was the top initial infection vector as SocGholish activity decreased. Activity levels for Malspam and Multiple increased, while activity for Dropped and Malvertisement decreased. It is likely that Multiple will remain the primary infection vector in the coming months as other malware add initial infection methods to increase the span of their campaign unless the current SocGholish campaign increases. The Multiple category can include several vectors, and as such, it tends to increase and decrease at unpredictable rates, making trend analysis challenging. This category will likely continue to comprise a significant portion of the initial infection vectors as malware becomes more sophisticated and employs multiple methods to infect systems. Malspam consistently represents a portion of the Top 10 Malware, as it is one of the oldest, most reliable primary initial infection vectors used by cyber threat actors in both this category and the Multiple category.
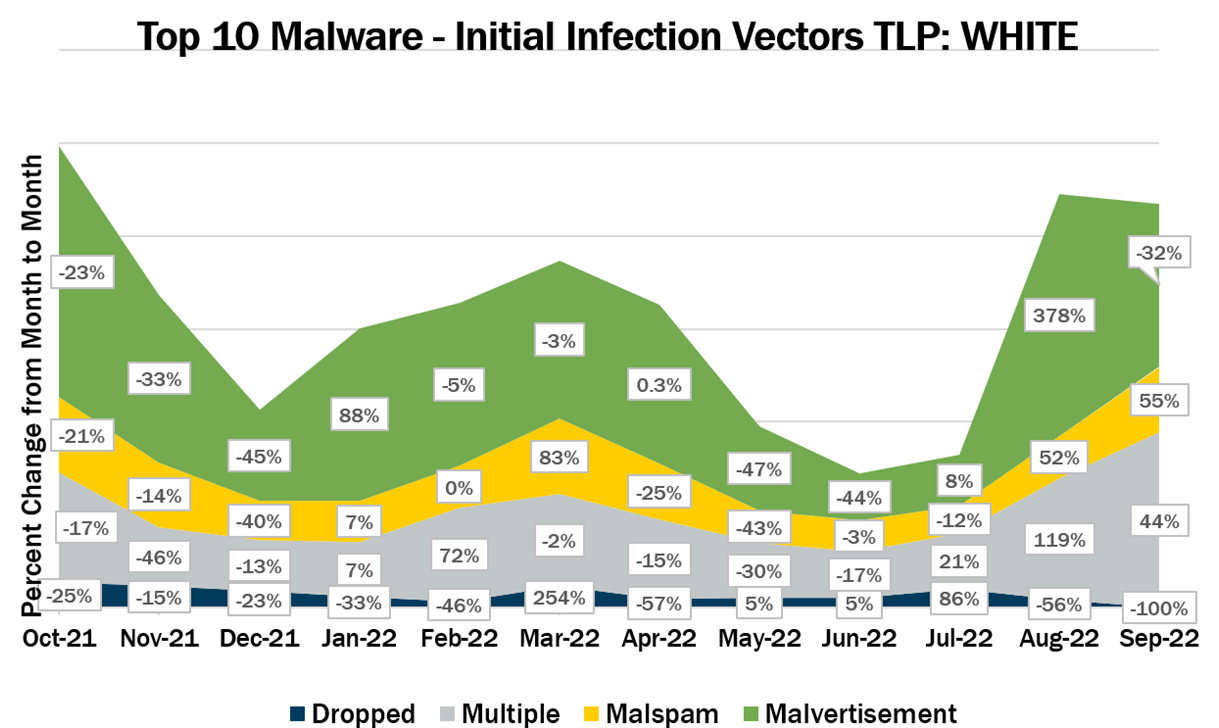
Multiple – Malware that currently favors at least two vectors. Currently, Arechclient2, CoinMiner, LingyunNet, RedLine, TeamSpy, and ZeuS are the malware utilizing multiple vectors.
Malspam – Unsolicited emails either direct users to malicious web sites or trick users into downloading or opening malware. Top 10 Malware using this technique include Agent Tesla, NanoCore, and Ursnif.
Malvertisement – Malware introduced through malicious advertisements. Currently, SocGholish is the only Top 10 Malware using this technique.
Top 10 Malware and IOCs
Below are the Top 10 Malware ranked in order of prevalence. The respective indicators of compromise (IOCs) are provided to aid in detecting and preventing infections from these Top 10 Malware variants.Note: The below IOCs are listed for the purpose of threat hunting though may not be inherently malicious. Additionally, the associated URIs are aligned with malware’s respective domain(s) or IP(s) and increase the likelihood of maliciousness when found together. The URIs alone are not inherently malicious.
1. SocGholish
SocGholish is a downloader written in JavaScript that is distributed through malicious or compromised websites. It uses fake updates, such as Flash Updates or browser updates. SocGholish has been known to use Cobalt Strike and steal information. Additionally, it has been known to lead to further malware infections, such as Azorult, Dridex, NetSupport RAT, and sometimes ransomware.Domains
irsbusinessaudit[.]net
irsgetwell[.]net
common.dotviolationsremoval[.]com
d2j09jsarr75l2.cloudfront[.]net
mafia.carverdesigngroup[.]com
cruize.updogtechnologies[.]com
record.usautosaleslv[.]com
hunter.libertylawaz[.]com
requests.pleaseactivate[.]me
zoom.themyr2bpodcast[.]com
accounts.mynewtopboyfriend[.]store
restructuring.breatheinnew[.]life
activation.thepowerofhiswhisper[.]com
sonic.myr2b[.]me
baget.godmessaged[.]me
predator.foxscalesjewelry[.]com
amplifier.myjesusloves[.]me
episode.foxscales[.]com
active.aasm[.]pro
tickets.kairosadvantage[.]com
templates.victoryoverdieting[.]com
casting.faeryfox[.]com
wallpapers.uniquechoice-co1[.]com
basket.stylingtomorrow[.]com
vacation.thebrightgift1[.]com
wallpapers.uniquechoice-co[.]com
vacation.thebrightgift[.]com
cigars.pawscolours[.]com
premium.i5417[.]com
rituals.fashionediter[.]com
expense.brick-house[.]net
loans.mistakenumberone[.]com
soendorg[.]top
prompt[.]zonashoppers[.]academy
hair[.]2topost[.]com
clean[.]godmessagedme[.]com
secretary[.]rentamimi[.]com
custom[.]usmuchmedia[.]com
2. CoinMiner
CoinMiner is a cryptocurrency miner family that typically uses Windows Management Instrumentation (WMI) and EternalBlue to spread across a network. Additionally, it typically uses the WMI Standard Event Consumer scripting to execute scripts for persistence. However, due to multiple variants of this malware, capabilities may vary. CoinMiner spreads through malspam or is dropped by other malware.MD5 Hashes
90db8de2457032f78c81c440e25bc753
d985ca16ee4e04ce765e966f1c68348f
f2184f47be242eda117037600760c3d7
4fd9592b8bf4db6569607243997cb365
3. ZeuS
ZeuS is a modular banking trojan that uses keystroke logging to compromise victim credentials when the user visits a banking website. Since the release of the ZeuS source code in 2011, many other malware variants have adopted parts of its codebase, which means that events classified as ZeuS may actually be other malware using parts of the ZeuS code.MD5 Hashes
2db9ee63581f0297d8ca118850685602
306cbc3c0d2b83e57a68dec63a37f22f
416cfb5badf096eef29731ee3bcba7ce
5e5e46145409fb4a5c8a004217eef836
ae6cdc2be9207880528e784fc54501ed
d93ca01a4515732a6a54df0a391c93e3
4. NanoCore
NanoCore is a RAT spread via malspam as a malicious Excel XLS spreadsheet. As a RAT, NanoCore can accept commands to download and execute files, visit websites, and add registry keys for persistence.Domains
nanoboss[.]duckdns[.]org
justinalwhitedd554[.]duckdns[.]org
shahzad73[.]casacam[.]net
shahzad73[.]ddns[.]net
SHA256 Hashes
c8c69f36f89061f4ce86b108c0ff12ade49d665eace2d60ba179a2341bd54c40
dfdb008304c3c2a5ec1528fe113e26088b6118c27e27e5d456ff39d300076451
ff66be4a8df7bd09427a53d2983e693489fbe494edd0244053b29b9f048df136
0195b0fbff91bece4665d8189bec104e44cdec85b6c26f60023a92dece8ca713
098fe3c8d0407e7438827fb38831dac4af8bd42690f8bd43d4f92fd2b7f33525
2605a1cb2b510612119fdb0e62b543d035ad4f3c873d0f5a7aa3291968c50bc8
28ef1f6f0d8350a3fda0f604089288233d169946fca868c074fc16541b140055
4b61697d61a8835a503f2ea6c202b338bde721644dc3ec3e41131d910c657545
7257729274b6ab5c1a605900fa40b2a76f386b3dbb3c0f4ab29e85b780eaef73
959484bfe98d39321a877e976a7cde13c9e2d0667a155dda17aeade58b68391c
988c1b9c99f74739edaf4e80ecaba04407e0ca7284f3dbd13c87a506bf0e97b7
5. Agent Tesla
Agent Tesla is a RAT that can exfiltrate credentials, log keystrokes, and capture screenshots from an infected computer.SHA256 Hashes
Initial Infection File
7f7323ef90321761d5d058a3da7f2fb622823993a221a8653a170fe8735f6a45
First Stage dll module
c0ee1071e444f415f8b62856a0896f3b22e563f1bb4f03d14142583efe49a565
XLL Droppers
fbc94ba5952a58e9dfa6b74fc59c21d830ed4e021d47559040926b8b96a937d0
7a6f8590d4be989faccb34cd393e713fd80fa17e92d7613f33061d647d0e6d12
Final Agent Tesla Payload
ab5444f001b8f9e06ebf12bc8fdc200ee5f4185ee52666d69f7d996317ea38f3
f3ebbcbcaa7a173a3b7d90f035885d759f94803fef8f98484a33f5ecc431beb6
12a978875dc90e03cbb76d024222abfdc8296ed675fca2e17ca6447ce7bf0080
3a4fc42fdb5a73034c00e4d709dad5641ca8ec64c0684fa5ce5138551dd3f47a
5d555eddfc23183dd821432fd2a4a04a543c8c1907b636440eb6e7d21829576c
9d713d2254e529286ed3ac471e134169d2c7279b0eaf82eb9923cd46954d5d27
6. TeamSpy
TeamSpy is spyware that has been known to use a popular remote access tool, TeamViewer, and malware to steal information from victims.IPs
185[.]141[.]63[.]172
193[.]242[.]211[.]141
Domains
These are domains created by a generation algorithm (DGA).
Aypbwhw[.]ru
Bboazuw[.]com
Bbvdjuw[.]com
Bjwoquv[.]com
Brozbsw[.]com
Ckrokei[.]net
Diczhcx[.]info
Dlylbux[.]info
Dtnpzec[.]info
eggrewv[.]ua
egtobdw[.]ua
emrdtbx[.]ua
endtcww[.]ua
eubjdjx[.]ua
eugnhuw[.]ua
gjdhcdw[.]com
gragcdw[.]com
hkaauvb[.]net
jmqmcdq[.]info
khuddqu24603344[.]ua
khvrder23620304[.]ua
kvbinbw23685840[.]ua
kxvfeow23554768[.]ua
qivoeeu[.]ru
rrlqlzv[.]com
uhgybdw[.]ua
uuxiqlu[.]ua
wzoodor[.]com
xknyajr[.]net
xsdbflb[.]net
ydfhzrx[.]info
ydxemre[.]info
ylfoopp[.]info
ytlqxzq[.]info
zbmgsbi[.]ua
zetuhne[.]ua
zfdboiu[.]ua
zftdlxd[.]ua
zhoppju[.]ua
zouiols[.]ua
zoumzgb[.]ua
zozlwla[.]ua
zueclka[.]ua
zwadpme[.]ua
zxfbihb[.]ua
7. LingyunNet
LingyunNet is riskware that utilizes the victim's system resources.Domains
ampc[.]na[.]lb[.]holadns[.]com
ampc[.]na[.]lb[.]martianinc[.]co
zcky[.]na[.]lb[.]holadns[.]com
zcky[.]na[.]lb[.]martianinc[.]co
8. Ursnif
Ursnif, also known as Gozi or Dreambot, is a banking trojan that is spread through malspam with a Microsoft Office document attached or a ZIP file containing an HTA file. Ursnif collects victim information from cookies, login pages, web forms. Additionally, Ursnif’s web injection attacks include TLS callbacks in order to obfuscate against anti-malware software.Domains
expl[.]intorcafli[.]art
hop[.]feen007[.]at
iujdhsndjfks[.]com
kol[.]dsasghqwt[.]com
turialopatnds[.]live
wdeiqeqwns[.]com
weiqeqwens[.]com
weiqeqwns[.]com
weiqewqwns[.]com
IPs
185[.]240[.]103[.]83
45[.]8[.]158[.]104
9. Arechclient2
Arechclient2, aka SectopRAT, is a NET RAT with numerous capabilities including multiple stealth functions. Arechclient2 can profile victim systems, steal information such as browser and crypto-wallet data, and launch a hidden secondary desktop to control browser sessions. Additionally, it has several anti-VM and anti-emulator capabilities.10. RedLine
RedLine is an infostealer that is available for purchase on cybercriminal forums. Due to its ability to be purchased, there are multiple malware campaigns, infection vectors, targets, and abilities (based on version being used). The malware typically targets information that can be easily monetized such as credentials, cookies, banking information, and cryptocurrency wallet information. Additionally, the malware gathers information about the infected system such as web browser, FTP clients, instant messengers, VPN services, and gaming clients. Furthermore, RedLine has remote functionality that enables it to download further malicious tools or drop additional malware.IPs
185[.]215[.]113[.]121
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.