Top 10 Malware December 2022
Note: The Top 10 Malware blog is moving from monthly to quarterly in 2023. This shift aims to improve the granularity and quality of the report. All indicators are still available in near real-time via the ISAC’s Indicator Sharing Program.
By: The Cyber Threat Intelligence (CTI) team at the Multi-State Information Sharing and Analysis Center
Published January 20, 2023
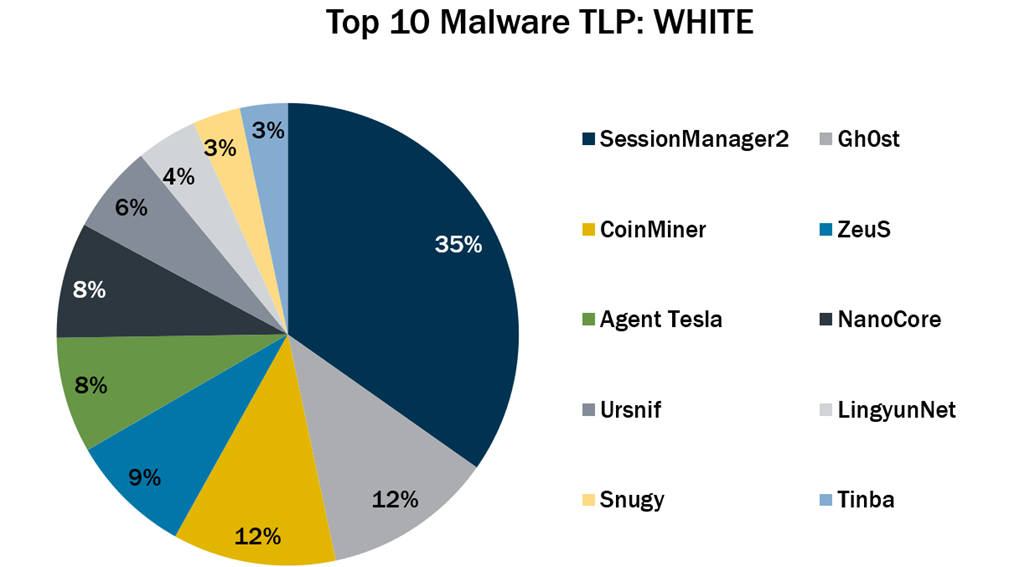
 In December 2022, the Top 10 Malware list remained consistent with November’s list except for the addition of three malware. This month, NanoCore, Snugy, and Tinba returned to the Top 10 Malware list. Additionally, SessionManager2 became the new top malware for the month.
In December 2022, the Top 10 Malware list remained consistent with November’s list except for the addition of three malware. This month, NanoCore, Snugy, and Tinba returned to the Top 10 Malware list. Additionally, SessionManager2 became the new top malware for the month.- NanoCore is a remote access trojan (RAT) spread via malspam with an attachment, such as a malicious Excel XLS spreadsheet. NanoCore accepts commands to download and execute files, visit websites, and add registry keys for persistence.
- Snugy is a PowerShell-based backdoor that obtains the system’s hostname and runs other commands. The backdoor communicates through a DNS tunneling channel on the compromised server.
- Tinba (aka Tiny Banker) is a banking trojan that's known for its small file size. Tinba uses web injection to collect victim information from login pages and web forms. It is primarily disseminated via exploit kits.
- SessionManager2 is a malicious Internet Information Services (IIS) module or backdoor that enables cyber threat actors (CTAs) to maintain persistent, update-resistant, and relatively stealthy access to a victim’s infrastructure.
The Top 10 Malware variants comprised 54% of the total malware activity in December 2022, staying consistent with the previous month.

Malware Infection Vectors
The MS-ISAC tracks potential primary infection vectors for our Top 10 Malware each month based on open-source reporting, as depicted in the graph below. We currently track four initial infection vectors: Dropped, Malvertisement, Malspam, and Network. The MS-ISAC did not observe any malware in the Top 10 use the initial infection vector Network in the past year. Some malware use different vectors in different contexts and are tracked as Multiple.
Our Community Defense Model (CDM) v2.0 can help you defend against 77% of ATT&CK (sub-)techniques associated with malware – regardless of the infection vector they use. Learn more in the video below.
In December 2022, Dropped was the top initial infection vector due to SessionManager2 and Gh0st activity. Activity levels for Dropped and Malspam increased, while the activity level for Multiple decreased. It is likely that Dropped will remain the primary infection vector in the coming months if SessionManager2 activity continues. Once SessionManager2 activity decreases, Multiple will become the top initial infection vector as the trend of having more than one initial infection vector continues. Malware authors continue to add additional initial infection methods to increase the span of their campaign and the likelihood of success. The most popular ways of using Multiple initial infection vector is the combination of Malspam and Dropped. Malspam consistently represents a portion of the Top 10 Malware, as it is one of the oldest and most reliable initial infection vectors used by CTAs.

Dropped – Malware delivered by other malware already on the system, an exploit kit, infected third-party software, or manually by a CTAs. Gh0st and SessionManager2 are the only two malware in the Top 10 that are dropped.
Multiple – Malware that currently favors at least two vectors, such as Malspam and Dropped. Currently, CoinMiner, LingyunNet, Snugy, and ZeuS are the Top 10 Malware utilizing multiple vectors.
Malspam – Unsolicited emails either direct users to malicious websites or trick users into downloading/opening malware. The Top 10 Malware using this technique include Agent Tesla, NanoCore, Tinba, and Ursnif.
Top 10 Malware and IOCs
Below are the Top 10 Malware ranked in order of prevalence. The respective indicators of compromise (IOCs) are provided to aid in detecting and preventing infections from these malware variants. The below IOCs can be used for threat hunting but may not be inherently malicious for blocking purposes.
1. SessionManager2
SessionManager2 is a malicious Internet Information Services (IIS) module or backdoor that enables CTAs to maintain persistent, update-resistant, and relatively stealthy access to a victim’s infrastructure.
MD5 Hashes
5FFC31841EB3B77F41F0ACE61BECD8FD
84B20E95D52F38BB4F6C998719660C35
4EE3FB2ABA3B82171E6409E253BDDDB5
2410D0D7C20597D9B65F237F9C4CE6C9
2. Gh0st
Gh0st is a RAT used to control infected endpoints. Gh0st is dropped by other malware to create a backdoor that allows an attacker to fully control the infected device.
MD5 Hashes
77bd9926a4b41c14259e20c1f90e22aa
3. CoinMiner
CoinMiner is a cryptocurrency miner family that typically uses Windows Management Instrumentation (WMI) to spread across a network. Additionally, it often uses the WMI Standard Event Consumer scripting to execute scripts for persistence. However, the malware’s capabilities may vary since there are multiple variants. CoinMiner spreads through malspam or is dropped by other malware.
MD5 Hashes
90db8de2457032f78c81c440e25bc753
IPs
199[.]247[.]27[.]41
4. ZeuS
ZeuS is a modular banking trojan that uses keystroke logging to compromise credentials when a victim visits certain banking websites. Since the release of the ZeuS source code in 2011, many other malware variants have adopted parts of its codebase, which means that incidents classified as ZeuS may actually be other malware using parts of the original ZeuS code.
MD5 Hashes
2db9ee63581f0297d8ca118850685602
416cfb5badf096eef29731ee3bcba7ce
ae6cdc2be9207880528e784fc54501ed
8ad4fb848a323b62036ea463fcf58993
5. Agent Tesla
Agent Tesla is a RAT that targets Windows operating systems. It is available for purchase on criminal forums as Malware-as-a-Service (MaaS). It has various capabilities depending on the version purchased, including capturing keystrokes and screenshots, harvesting saved credentials from web browsers, copying clipboard data, exfiltrating victim files, and loading other malware onto the host.
Domains
mail[.]euroinkchemical[.]ro
mail[.]nobilenergysolar[.]com
SHA256 Hashes
Initial Infection File
7f7323ef90321761d5d058a3da7f2fb622823993a221a8653a170fe8735f6a45
XLL Droppers
fbc94ba5952a58e9dfa6b74fc59c21d830ed4e021d47559040926b8b96a937d0
7a6f8590d4be989faccb34cd393e713fd80fa17e92d7613f33061d647d0e6d12
Final Agent Tesla Payload
12a978875dc90e03cbb76d024222abfdc8296ed675fca2e17ca6447ce7bf0080
5d555eddfc23183dd821432fd2a4a04a543c8c1907b636440eb6e7d21829576c
6. NanoCore
NanoCore is a RAT spread via malspam with an attachment, such as a malicious Excel XLS spreadsheet. NanoCore accepts commands to download and execute files, visit websites, and add registry keys for persistence.
Domains
nanoboss[.]duckdns[.]org
justinalwhitedd554[.]duckdns[.]org
shahzad73[.]casacam[.]net
shahzad73[.]ddns[.]net
power22[.]myftp[.]org
SHA256 Hashes
c8c69f36f89061f4ce86b108c0ff12ade49d665eace2d60ba179a2341bd54c40
dfdb008304c3c2a5ec1528fe113e26088b6118c27e27e5d456ff39d300076451
ff66be4a8df7bd09427a53d2983e693489fbe494edd0244053b29b9f048df136
7257729274b6ab5c1a605900fa40b2a76f386b3dbb3c0f4ab29e85b780eaef73
959484bfe98d39321a877e976a7cde13c9e2d0667a155dda17aeade58b68391c
988c1b9c99f74739edaf4e80ecaba04407e0ca7284f3dbd13c87a506bf0e97b7
7. Ursnif
Ursnif, also known as Gozi or Dreambot, is a banking trojan and downloader that spreads through malspam emails with Microsoft Office document attachments or ZIP files containing an HTA file. Ursnif collects victim information from cookies, login pages, and web forms. Additionally, Ursnif’s web injection attacks include TLS callbacks in order to obfuscate against anti-malware software. Furthermore, Ursnif’s newest variant has a built-in command shell which provides a reverse shell for connection to remote IP addresses. This allows a CTA to execute system commands via command line, enabling them to perform further reconnaissance as well as more effective lateral movement. Lastly, Ursnif has the ability to drop additional malware, such as ransomware.
Domains
Gameindikdowd[.]ru
Iujdhsndjfks[.]ru
Jhgfdlkjhaoiu[.]su
Lentaphoto[.]at
reggy505[.]ru
IPs
188[.]127[.]224[.]114
194[.]58[.]102[.]187
194[.]58[.]112[.]174
37[.]140[.]197[.]44
8. LingyunNet
LingyunNet is riskware that utilizes the victim’s system resources, which can slow down the computer or cause errors and potentially lead to further infections. Riskware is a program or application that potentially poses a risk due to its ability to exploit and cause damage to a system.
Domains
ampc[.]na[.]lb[.]holadns[.]com
ampc[.]na[.]lb[.]martianinc[.]co
Na[.]lb[.]willmam[.]com
zcky[.]na[.]lb[.]holadns[.]com
zcky[.]na[.]lb[.]martianinc[.]co
10[.]17ce[.]holadns[.]com
10[.]17ce[.]martianinc[.]co
9. Snugy
Snugy is a PowerShell-based backdoor that obtains the system’s hostname and runs other commands. This backdoor communicates through a DNS tunneling channel on the compromised server.
SHA256 Hashes
6c13084f213416089beec7d49f0ef40fea3d28207047385dda4599517b56e127
10. Tinba
Tinba (aka Tiny Banker) is a banking trojan that's known for its small file size. Tinba uses web injections to collect victim information from login pages and web forms and is primarily disseminated via exploit kits.
SHA256 Hashes
7a4def318c9873d3812da9c61824dd99a64fc4b4f61f870e081440c4364008bc
About the Author: The Cyber Threat Intelligence (CTI) team at the Multi-State Infrastructure Information Sharing and Analysis Centers (MS-ISAC) functions as the premier CTI source for all U.S. State, Local, Tribal, and Territorial (SLTT) entities. With a combined x years of experience in all types of industries, the CTI team pushes out Indicators of Compromise through its real-time threat indicator feeds. This information helps SLTTs automate defensive actions, correlate events, conduct analysis, and make better, faster, more impactful decisions. You can learn more about these feeds here.
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.