SLTT Organizations and the Defense-in-Depth Strategy
Defense-in-depth applies layers of controls and mitigations to systems and networks, providing redundancy and reducing the likelihood of a successful cyberattack or a single point of failure. Many U.S. State, Local, Tribal and Territorial (SLTT) organization networks are already protected by cybersecurity technologies. But while technology plays an important role in protecting SLTTs, it is only one layer of the defense-in-depth strategy. Simply stated, technology alone isn’t enough.
3 Benefits to SLTTs that Adopt a Defense-in-Depth Strategy
A defense-in-depth strategy protects the confidentiality, integrity, and availability of the network and the data within. It is beneficial to adopt this strategy because it:
- Ensures network security is redundant, preventing any single point of failure.
- Significantly increases the time and complexity required to successfully compromise a network.
- Provides many hurdles a cyber threat actor must overcome. Most cyberattacks are opportunistic, meaning cyber threat actors take the path of least resistance. Unless your organization is the specific target, they will move on to less mature organizations that haven’t implemented a defense-in-depth strategy.
While no individual mitigation can stop all cyber threats, the systems in a defense-in-depth strategy provide protection against a wide variety of threats while incorporating redundancy in the event one mechanism fails. When successful, this approach significantly bolsters network security against many attack vectors.
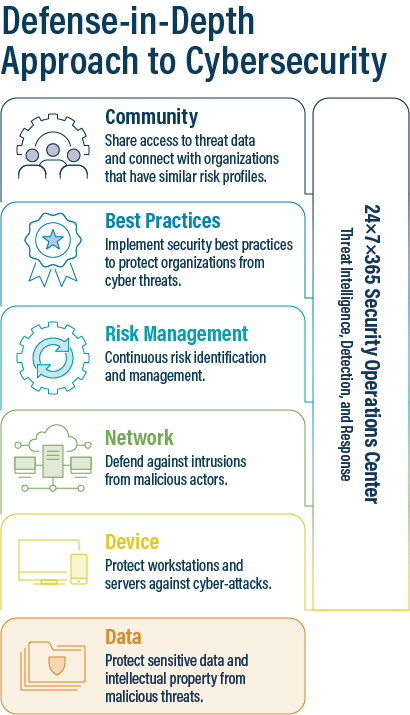
The Challenge SLTTs Face with Defense-in-Depth Implementation
A defense-in-depth strategy requires a wide range of security best practices, tools, and policies that strengthen an organization’s security posture. Some of these tools include firewalls, an intrusion detection system (IDS) or intrusion prevention system (IPS), endpoint detection and response (EDR) software, and more.
While government organizations recognize the importance of incorporating crucial mechanisms to enhance their cybersecurity, time and resources are always a challenge. Obtaining services from outside sources may be necessary in order to build a strong cybersecurity program.
For example, U.S. SLTTs can join the Multi-State Information Sharing and Analysis Center (MS-ISAC) at no cost. The MS-ISAC is designated by DHS as the cybersecurity ISAC for state, local, tribal, and territorial (SLTT) governments. It provides services and information sharing that significantly enhances SLTT governments’ ability to prevent, protect against, respond to and recover from cyberattacks and compromises.
Managed Detection and Response Offers Protection and Response
CIS Managed Detection and Response™ (CIS MDR™) delivers advanced device-level protection to help U.S. SLTT member organizations of the MS-ISAC secure their endpoints against evolving threats. With hosting options available in the GovCloud and Commercial Cloud, this flexible and cost-effective solution actively defends U.S. SLTTs against both known and unknown malicious activity — including encrypted malicious traffic and zero-day attacks.
More than just blocking threats, CIS MDR takes an active role in isolating, quarantining, and remediating malware in real time, thus stopping attacks before they spread. It also helps with tracking the root cause of compromises, giving U.S. SLTT organizations the insights they need to prevent future incidents.
Want to learn more about CIS MDR? Check out our video below.
Managed Security Services (MSS) to Support Defense-in-Depth
CIS, in partnership with Accenture, provides Managed Security Services (MSS) to help U.S. SLTT organizations improve their cybersecurity. These services monitor SLTT devices for signs of malicious or anomalous activity, eliminate false positives, and escalate only actionable items as an alert. This alleviates alert and log fatigue by filtering out all of the false positives and only “alert” on what is impactful. The elimination of false positives saves an organization time and effort in reviewing potential threats. As a result, organizations spend more time focused on their core mission and less time worrying about cybersecurity.

Benefits of MSS from CIS include:
- Access to the 24x7x365 Security Operations Center (SOC) for questions and support
- A customized Log Collection Platform (LCP) built with CIS and Accenture
- Reports and analysis done by expert analysts using cyber threat intelligence specifically focused on SLTTs, providing details of all incidents for the previous month, and statistics on data such as events, incidents, and a review of the total volume of monitored traffic
- Access to the Accenture portal, which provides visibility into security events
MSS provides a valuable expansion of insight, saves time and resources for government organizations, and alleviates information fatigue, all while supporting a defense-in-depth strategy.
![]()
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.