How Secure by Design Helps Developers Build Secure Software
Security isn’t just a feature; it’s a foundation. As cyber threats grow more sophisticated and regulations tighten, developers are being asked to do more than just write clean code. They’re being asked to build software that’s secure by design throughout its lifetime.
To help developers meet this challenge, the Center for Internet Security® (CIS®) and the Software Assurance Forum for Excellence in Code (SAFECode) released Secure by Design: A Guide to Assessing Software Security Practices. This guide offers practical, risk-based strategies for integrating security into every phase of the software development lifecycle — tailored to real-world development environments.
Why Secure by Design Matters
The Secure by Design initiative, launched by the Cybersecurity and Infrastructure Security Agency (CISA) in 2023, urges technology vendors to prioritize customer security and reduce exploitable flaws at the source. But with fragmented guidance across frameworks like the National Institute of Standards and Technology (NIST) Secure Software Development Framework (SSDF), Building Security in Maturity Model (BSIMM), and SAFECode’s own practices, developers have lacked a unified path forward — until now.
This guide bridges that gap by aligning with NIST’s SSDF, mapping practices to the CIS Critical Security Controls® (CIS Controls®) and adapting recommendations to different organizational maturity levels using SAFECode’s Development Groups (DGs) model.
Six Secure by Design Considerations Every Developer Should Know
The guide breaks Secure by Design into six essential areas. Here’s what developers need to focus on:
1. Secure Software Design
Start with clear security objectives and a threat model. Whether you’re building for a niche application or a broad user base, your architecture must reflect the risks your software is expected to resist. Threat modeling isn’t optional; it’s your blueprint for resilience and needs to be maintained as the software and its use change.
2. Secure Development
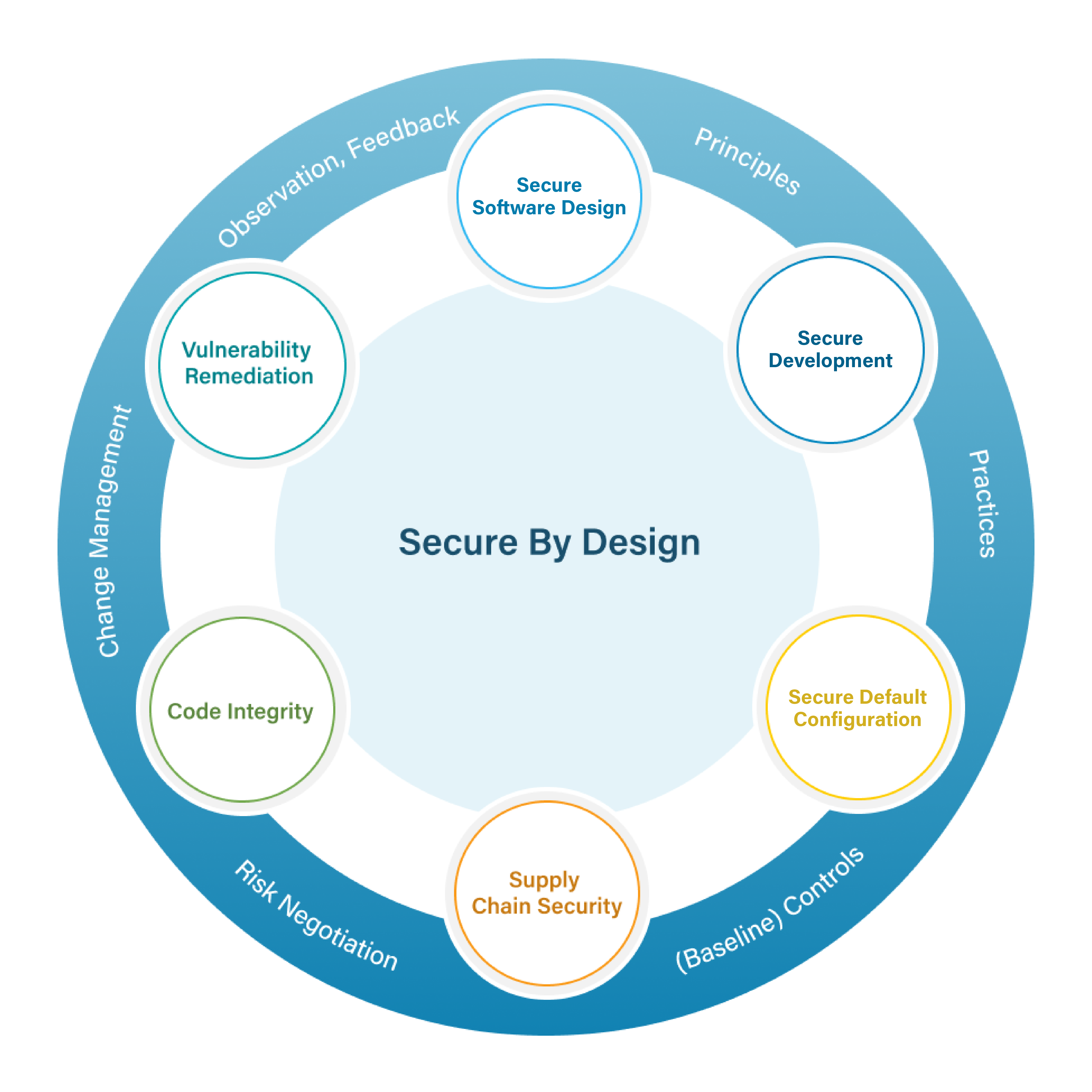
Coding, testing, deployment, and maintenance are where most vulnerabilities emerge. align your practices with the ssdf and tailor them to your tools, languages, and platforms. whether you’re working in containers, mobile apps, or embedded systems, the principles remain: validate inputs, manage secrets, and automate security checks.
3. Secure Default Configuration
Most users stick with default settings — so make them secure. Disable unnecessary features, restrict access, and minimize the attack surface. If 80% of users don’t need a feature, it should be off by default. This offers more than just good hygiene; it provides a frontline defense.
4. Supply Chain Security
Third-party code is everywhere, and it’s a risk. Vet, monitor, and manage the components you didn’t write and ensure that their security is maintained over time. Use contracts, audits, and internal reviews. If you rely on open-source or commercial tools, make sure they meet your security standards. And if they don’t, fill the gaps with scans, tests, and feedback loops.
5. Code Integrity
Security isn’t just about writing good code; it’s about ensuring the code you ship is the code you intended. Use version control, code signing, and change tracking to prevent tampering. Configure your development environment with least privilege and zero trust principles. And secure your tools as they’re part of your attack surface.
6. Vulnerability Remediation
No software is perfect. Accept vulnerability reports, investigate them, and fix the issues. Sponsor bug bounties, publish advisories using standards like the Common Security Advisory Framework (CSAF), and provide context on severity and exploitability. And critically important, use root cause analysis to improve your tools, training, and threat models. If you rely on external tools, give feedback to help them evolve.
Built for Developers, Not Just Auditors
Secure by Design: A Guide to Assessing Software Security Practices goes beyond just telling you what to do; it also helps you understand why it matters and how to tailor it to your organization’s maturity level. Using SAFECode’s DGs model, this guide helps you prioritize high-value activities whether you’re a lean startup or a large enterprise. And it provides guidance that helps you understand the implications of artificial intelligence and machine learning for the security of your software.
Security is a continuous process. But with the right framework, you can build software that’s secure by design, not just by accident. Level up your secure development practices and build with confidence.
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.