Defense-in-Depth: A Necessary Approach to Cloud Security
By Angelo Marcotullio, Chief Information Officer at CIS

Cloud security isn't getting any easier. A 2022 report stated that 45% of businesses had experienced either a data breach or failed audit in the cloud over the preceding 12 months. That's up 5% over the previous year. Approximately one-fifth of respondents to the study cited an increase in cloud-based cyber attacks including malware, ransomware, and phishing/whaling.
Given these challenges, you can’t rely on just any approach to secure your cloud-based systems and data. You need a strategic approach like defense-in-depth that will protect you against cyber threats from multiple angles. In this blog post, I will explain how defense-in-depth works, why it’s a necessary methodology for securing the cloud, and how you can achieve defense-in-depth through the Center for Internet Security (CIS).
3 Benefits of Implementing Defense-in-Depth in the Cloud
Defense-in-depth is the implementation of multiple layers of security controls around your data and security systems. It's like an onion. Each layer is a cybersecurity control that makes it more difficult for an attacker to get to your data at the core. This holds true for whether you store your data on premises or in the cloud.
Even so, the cloud is complex and dynamic compared to environments that are on premises. It doesn't take days or weeks to get something up and running. In the cloud, you can bring up systems as quickly as possible. This creates a degree of flexibility as well as complexity that can be difficult to manage from a security perspective.
By taking a defense-in-depth approach to your cloud security, you can do the following:
- Prevent any single point of failure: Successive defenses prevent cyber threat actors (CTAs) from using ransomware, phishing, etc. to breach your cloud-based assets.
- Create hurdles for cyber threat actors: Because it's so difficult for CTAs to infiltrate your defenses, they'll be more inclined to go target other organizations.
- Establish multiple opportunities for incident response: Say that someone tries to log in as one of your users at 03:00, for example. Your IT and security team can see this and raise the alarm so that you can address the incident before it escalates into a data breach.
How You Can Take a Defense-in-Depth Approach with CIS
You can adopt a defense-in-depth approach to cloud security using three resources at CIS.
CIS Critical Security Controls
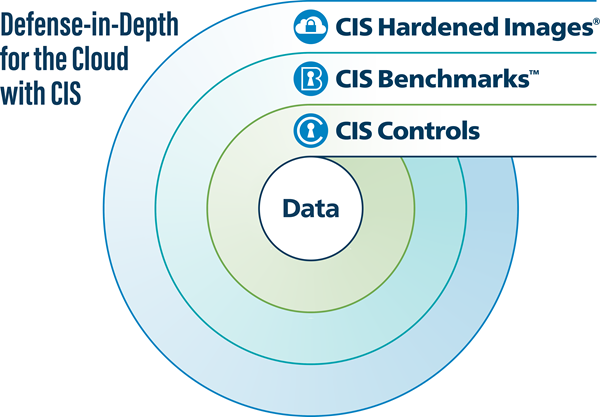
Your defense-in-depth journey begins with the CIS Critical Security Controls (CIS Controls). Focused on the corporate IT network, the CIS Controls are prioritized and prescriptive best practices that help you to defend against common cyber threats, as noted in our Community Defense Model v2.1. The Controls are freely available on the CIS website.
We've organized the Controls into Implementation Groups (IGs) to help you strengthen your cybersecurity maturity over time. You begin with Implementation Group 1 (IG1), which is our definition of essential cyber hygiene. From there, you move onto implementing the rest of the Controls using Implementation Group 2 (IG2) and Implementation Group 3 (IG3).
In terms of implementing the Controls in the cloud, you can use our CIS Controls v8 Cloud Companion Guide. It discusses how you can implement a specific Control depending on what type of service model (IaaS, PaaS, SaaS, or FaaS) you're using. It also helps you to identify who's responsible for that Control and follow additional cloud-specific guidance.
CIS Benchmarks
Once you have you've laid a foundation with the CIS Controls that matter most to your business, you can implement the CIS Benchmarks, or system-hardening guides for specific pieces of software. The Benchmarks map to the Controls and use secure configurations to help you protect your technologies at the level of the operating system. A global community of volunteers is responsible for developing the Benchmarks. This process ensures that the Benchmarks' hardening guidelines reflect the expertise of IT professionals around the world.
You can implement two types of Benchmarks with respect to the cloud. First, you can implement Foundations Benchmarks. They consist of core recommendations for each cloud service provider (CSP). Second, you can use the Cloud Services Benchmarks, which group relevant services of a CSP under logical categories, to augment your cloud security posture. The Cloud Services Benchmarks also help you to secure the cloud account and environment in which the CIS Hardened Images run.
CIS Hardened Images
Finally, there are the CIS Hardened Images. To create these resources, we took the Benchmarks' security recommendations and applied them to virtual images in AWS Marketplace, Microsoft Azure, Google Cloud Platform, and Oracle Cloud Marketplace. An example of a Hardened Image is an AWS EC2 server that already has the security recommendations of a Benchmark applied to it.
We update the Hardened Images regularly. In the process, you don't need to waste time building out and applying the security recommendations from a Benchmark in the cloud. Best of all, each Hardened Image costs only $0.02 per compute hour.
Begin Your Defense-in-Depth Approach to the Cloud
Cyber threat actors are committed to breaching your cloud-based systems and data. But nothing says they need succeed. By using CIS resources to achieve defense-in-depth in the cloud, you can make it as difficult as possible for the bad guys to infiltrate your cloud environments and create multiple opportunities to respond to threats while they’re in progress.
About the Author
Angelo Marcotullio
Chief Information Officer

Angelo Marcotullio is a technology specialist with more than 25 years of experience delivering technology solutions from concept to completion. As Chief Information Officer, Angelo is responsible for the delivery of innovative, reliable and secure applications that support and enhance CIS’ global mission. In addition to managing daily technology operations, Angelo provides strategic planning for a fast-growing company globally recognized as a leader in cybersecurity.
Prior to joining CIS in 2016, Angelo served as Principal Consultant at his own technology firm leading information technology projects in multiple industries including state and federal government, healthcare, finance and manufacturing. Angelo obtained Bachelor and Master degrees from Stony Brook University.
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.