2021 NCSR: SLTTs Struggle with Supply Chain, Risk Management
Cyber attacks targeting U.S. State, Local, Tribal, and Territorial (SLTT) government organizations increased significantly in 2022. In a mid-year update to the 2022 SonicWall Cyber Threat Report, for instance, researchers found that ransomware affecting government organizations rose 1,885%, eclipsing the combined growth in attacks against healthcare (755%), education (152%), and retail (21%). It was a similar story with cryptojacking and malware. Cryptojacking attempts grew 709% among the public sector in 2021. (By comparison, global cryptojacking attacks increased 19% for all sectors year over year.) Meanwhile, the volume of malware attacks in government entities escalated 94%. This was despite global malware rates falling by four percent during the same period.
These findings highlight the need for SLTTs to better understand their cybersecurity postures so that they can make meaningful improvements going into 2023. To get started, they can reference the findings of the 2021 Nationwide Cybersecurity Review. Let's explore.
Notable Data Points of the 2021 NCSR
The Nationwide Cybersecurity Review (NCSR) is an annual, no-cost, and anonymous self-assessment designed to measure the gaps and capabilities of SLTT governments’ cybersecurity programs. Participants can also use the NCSR to gauge their cybersecurity posture relative to their peers.
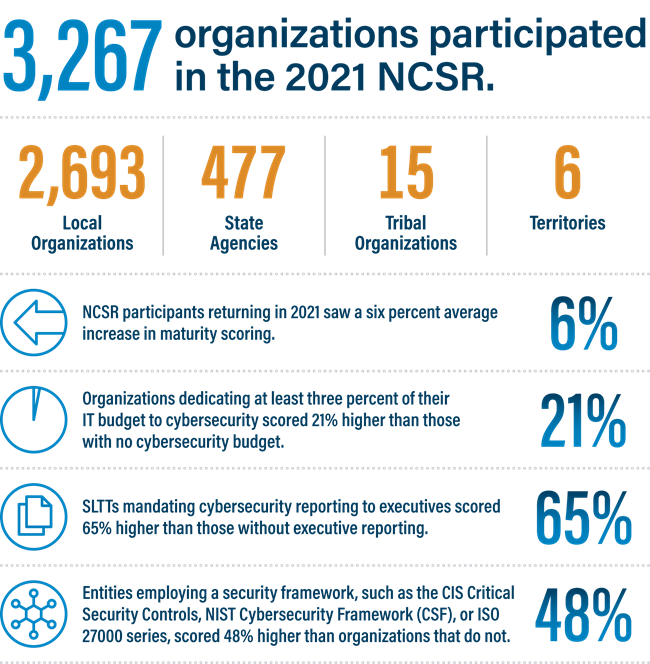
The 2021 NCSR was available for SLTT participation from October 1, 2021, through February 28, 2022. A total of 3,267 SLTT organizations participated. This included 2,693 local organizations, 477 state agencies, 15 tribal organizations, and six territories.
Return Participation Leads to Higher Maturity
NCSR participants who returned in 2021 saw a six percent average increase in maturity scoring. To understand why we turned to the Multi-State Information Sharing and Analysis Center (MS-ISAC) team.
"Participation in the NCSR helps provide a baseline the first time you take it," they explained. "From there, SLTTs can chart out improvements. So by participating in the NCSR, organizations can grow the maturity of their security programs over time."
Two Categories Where Participants Excelled
NCSR participants excelled in Identity Management & Access Control as well as Awareness & Training. Regarding the former, the MS-ISAC team noted that many SLTT organizations have built upon what they already had in place.
"Some of these activities and processes are low-hanging fruit," the team pointed out." Many SLTTs get password management, access control, and other features out of the box by purchasing certain products. So they already have processes in place to get a good score. This provides them with a baseline to get an even higher score by moving onto documentation and building a cybersecurity framework."
It was a similar story with Awareness & Training. The difference here is that other departments likely played a role in participants' scoring.
"Awareness & Training is often part of an organization's established processes," the team said. "Take HR and IT as an example. Onboarding processes commonly include new employee training, which may involve security training along with information for computer access. Awareness & Training is, therefore, something that many organizations are already doing."
Two Areas Warranting Improvement
In the 2021 NCSR, SLTTs struggled with Supply Chain Risk Management and Risk Management Strategy. The MS-ISAC team explained that this finding traces back to SLTTs' priorities.
"Some organizations (especially smaller locals) are trying to keep up with their day-to-day tasks," the team stated. "They might not be looking to formalize processes with third-party organizations and vendors in the short term. The same can be said of formalizing processes and documentation in terms of internal risk tolerance. They might see this as something that they can pursue down the road, if and when they obtain the necessary resources."
Maturity Scoring Elevated by Executive Reporting
Finally, participants that said they had reported on cybersecurity matters to executive management scored 65% higher in the 2021 NCSR than those without a similar communication channel.
"Executive reporting helps to create a culture of discussing security needs and priorities in the organization," the MS-ISAC team observed. "It keeps the organization focused on the importance of cybersecurity."
Some organizations might struggle with reporting cybersecurity issues to executives because they lack executive buy-in. To remedy that situation, organizations can review this case study to learn how they can inform stakeholders using cybersecurity metrics. They can also use the NCSR Data Reporting Template that they receive when they sign up to participate as a starting point to guide their conversations with executives.
The 2021 NCSR Overview
High-Performance Cybersecurity Activities for the SLTT Community
- Maintaining inventories of physical devices and systems
- Managing and protecting physical access to assets
- Managing remote access
- Issuing, managing, and verifying identities/credentials for authorized devices, users, and processes
- Conducting, maintaining, and testing backups of information
- Implementation of the following capabilities:
- Endpoint protection tools
- Intrusion defense systems
- Antiviral tools
Cybersecurity Areas of Deficiency for the SLTT Community
- Conducting response and recovery planning with suppliers and third-party providers
- Routinely assessing suppliers and third-party partners
- Usage of integrity checking mechanisms to verify hardware integrity
- Detecting unauthorized mobile code
- Identifying and prioritizing suppliers and third-party partners using a risk assessment process
- Implementation of the following capabilities:
- Automated tools for managing removable media
- Automated tools for creating and maintaining baseline configuration change control
- Two-factor authentication
Top 5 Security Concerns

Recommendations for SLTTs Going Forward
Regardless of whether they participated in the 2021 NCSR or not, SLTT organizations can look to strengthen their cybersecurity posture by implementing the following steps:
- Utilize federally funded services from organizations such as the MS-ISAC and the Cybersecurity Infrastructure Security Agency (CISA), along with open-source tools, to perform cybersecurity activities. Available services include a malicious domain blocking program, incident response planning resources, and supply chain best practice resources.
- Create security policies and communicate the policy information to executives, employees, and third-party stakeholders.
- Report organizational cybersecurity metrics to management or executive teams in order to justify and prioritize future cybersecurity investments.
- Evaluate practices within a formal cybersecurity framework, such as the CIS Critical Security Controls or a NIST Framework, and plan for implementation.
Incremental Improvements to Cybersecurity
The results of the 2021 NCSR demonstrate how cybersecurity is a journey, not a destination.
"Trying to create change in organizations creates time," the MS-ISAC team said. "It's not weeks and months. It's an ongoing process. That being said, there's no reason to get discouraged. Even if organizations don't have additional funding or investment available, they can use their existing employees and external resources to maximize the coverage of their security requirements."
Indeed, through participating in the NCSR, SLTTs will receive critical information that they can use to embark on their own journeys towards improving their cybersecurity posture.
As of June 23, 2025, the MS-ISAC has introduced a fee-based membership. Any potential reference to no-cost MS-ISAC services no longer applies.