All Insights
Explore security resources, trends and updates, media, podcast episodes, and more
Filter
1328 Results Found
Solutions
Industry
811 - 820 of 1328 results
Published on 05.25.2021
CIS Benchmarks are the only consensus-developed security configuration recommendations both created and trusted by a global community of IT secur...
CIS BenchmarksTechnology
Published on 05.21.2021
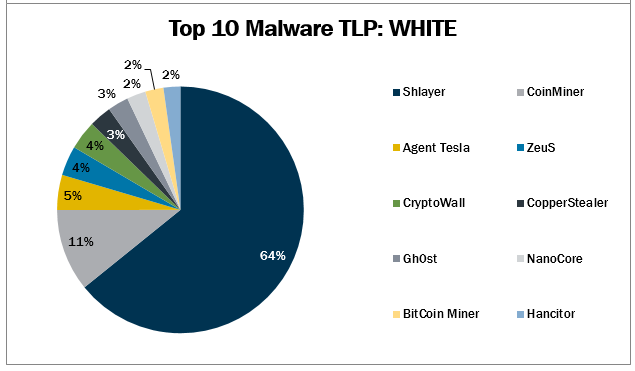
In April 2021, the MS-ISAC observed CryptoWall, Gh0st, and NanoCore’s return to the Top 10, while BitCoin Miner made its first appearance. The To...
MS-ISAC
Published on 05.20.2021
Changes and advances in technology (and changes in workplace circumstances) have prompted a revamp of the CIS Community Defense Model (CDM). Set ...
CIS Controls
Published on 05.20.2021
The Center for Internet Security’s 2020 Year in Review highlights all the efforts the cybersecurity nonprofit accomplished in its 20th year in bu...
CIS BenchmarksCIS ControlsCIS CyberMarketCIS Hardened ImagesCIS Services
Published on 05.18.2021
By: Autum Pylant The moment we’ve all been waiting for is finally here. The Center for Internet Security (CIS) officially launched CIS Crit...
CIS Controls
Published on 05.18.2021
This document provides a detailed mapping of the relationships between CIS Critical Security Controls v8 and NIST SP 800-171 Rev 2.
CIS Controls
Published on 05.18.2021
CIS Critical Security Controls (CIS Controls) v8 offers prescriptive, prioritized, and simplified cybersecurity best practices that provide a cle...
CIS Controls
Published on 05.18.2021
This document provides a detailed mapping of the relationships between CIS Critical Security Controls v8 and NIST SP 800-53 Rev. 5.
CIS Controls
Published on 05.18.2021
This document describes the methodology used to map the CIS Critical Security Controls to the Cloud Security Alliance Cloud Control Matrix. The m...
Published on 05.18.2021
This spreadsheet provides an overview of the changes from CIS Critical Security Controls version 7.1 to version 8. Our goal is to provide a refer...
CIS Controls
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More