Getting to Know the CIS Benchmarks
When the Center for Internet Security (CIS) was formed in 2000, the IT and cybersecurity industries identified a clear need to understand how to secure IT systems and data. This need highlighted a lack of hardening recommendations, particularly prescriptive and industry-recognized standards. Subsequently, CIS began working with the IT and cybersecurity industries to create secure configuration guidelines. They are now known collectively as the CIS Benchmarks.
What Are the CIS Benchmarks?
The CIS Benchmarks are secure configuration recommendations for hardening specific technologies in an organization's environment. They are a key component of an organization's overall security against cyber-attacks, and each CIS Benchmark recommendation maps to the CIS Critical Security Controls (CIS Controls). There are more than 100 CIS Benchmarks across 25+ vendor product families available through free PDF download for non-commercial use. CIS Benchmarks coverage includes security guidelines that are applicable to cloud provider platforms and cloud services, containers, databases, desktop software, server software, mobile devices, network devices, and operating systems.
Learn more about the CIS Benchmarks.
What Makes the CIS Benchmarks So Unique?
When compared to other secure configuration guides, the CIS Benchmarks stand out for four reasons:
1. The Consensus Development Process
Each Benchmark is the product of an ongoing consensus process involving the generous volunteer efforts of subject matter experts (SMEs), technology vendors, public and private community members, academics, and the CIS Benchmarks development team.
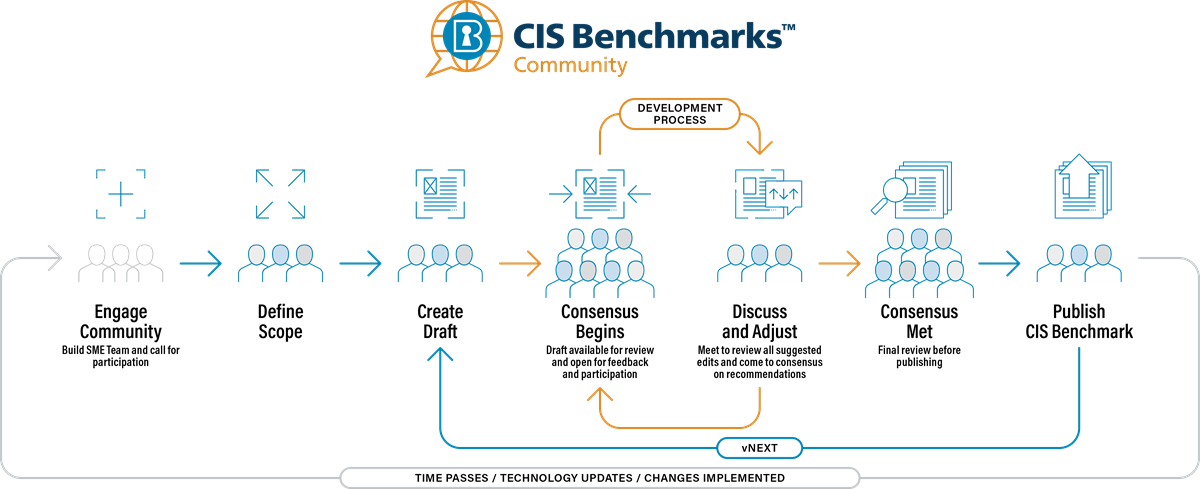
The process begins by engaging the community to develop an SME team and putting out a call for participation. Next, the team defines the scope of the Benchmark for a specific technology. This scope informs the work of SMEs, who are responsible for producing an initial draft.
Once that draft is complete, the development process begins. Here, the CIS Benchmarks development team announces the availability of the draft and invites volunteers to join a dedicated CIS Benchmarks Community for reviewing, testing, and providing feedback on the draft. All of the feedback that emerges from this consensus process goes back to the SMEs and the CIS lead responsible for that Benchmark Community. At this stage, the SMEs and CIS lead review the input and make any necessary changes to ensure that the Benchmark provides comprehensive guidance. They may then send the revised draft back through the development process for additional rounds of review until all feedback has been addressed.
After the completion of the consensus development process, the CIS lead re-releases the Benchmark and announces a final review period of two weeks within the corresponding Benchmark Community. After addressing any final feedback, they submit the final Benchmark for publication and, by extension, for public availability online. This Benchmark encapsulates the most up-to-date prescriptive guidance. The process starts entirely anew with the passage of time, certain technology updates, and/or other changes.
2. Different Ways To Get Involved
Currently, more than 12,000 professionals participate in our CIS Benchmarks Communities. Each of these individuals brings something different. To appeal to those unique skill sets, we're inviting volunteers to fill the following roles:
- Technical and Security SMEs – These positions are best suited to people with demonstrable expertise in a given technology, particularly regarding overarching security issues and/or system interactions within that technology.
- Technical Writers – No Benchmark would be possible without the input of technical writers who can succinctly communicate highly technical topics and proofread drafts.
- Testers – Anyone with access to network devices or specialized hardware can review and comment on the technical details of open discussions or tickets within a particular Benchmark.
You can volunteer for one (or several) CIS Benchmarks Communities by visiting CIS WorkBench.
3. Prescriptive Guidance
CIS Benchmarks don't just tell you what to do to harden your systems. They also tell you why. They do so by breaking down every security recommendation into several sections. These include the following core sections that explain why and how a particular recommendation is implemented:
- The description provides a high-level overview of the recommendation.
- The rationale clarifies why it's important to implement the recommendation.
- You need to understand the impact of implementing a recommendation.
- The audit identifies how to prove that a recommendation has been implemented for an audit.
- Finally, the remediation discusses steps to implement the recommendation.
To understand these core sections in practice, let's use Recommendation 1.1.4 from Level 1 of CIS Microsoft Windows 11 Enterprise Benchmark v1.0.0: "'Ensure 'Minimum password length' is set to '14 or more character(s)' (Automated)."
- Description: This policy setting determines the least number of characters that make up a password for a user account. There are many different theories about how to determine the best password length for an organization, but perhaps "passphrase" is a better term than "password." In Microsoft Windows 2000 and newer, passphrases can be quite long and can include spaces. Therefore, a phrase such as "I want to drink a $5 milkshake" is a valid passphrase; it is a considerably stronger password than an 8 or 10 character string of random numbers and letters, and yet is easier to remember. Users must be educated about the proper selection and maintenance of passwords, especially with regard to password length. In enterprise environments, the ideal value for the Minimum password length setting is 14 characters, however you should adjust this value to meet your organization's business requirements. The recommended state for this setting is: 14 or more character(s).
- Rationale: Types of password attacks include dictionary attacks (which attempt to use common words and phrases) and brute force attacks (which try every possible combination of characters). Also, attackers sometimes try to obtain the account database so they can use tools to discover the accounts and passwords.
- Impact: Requirements for extremely long passwords can actually decrease the security of an organization, because users might leave the information in an insecure location or lose it. If very long passwords are required, mistyped passwords could cause account lockouts and increase the volume of help desk calls. If your organization has issues with forgotten passwords due to password length requirements, consider teaching your users about passphrases, which are often easier to remember and, due to the larger number of character combinations, much harder to discover.
- Audit: Navigate to the UI Path articulated in the Remediation section and confirm it is set as prescribed.
- Remediation: To establish the recommended configuration via GP, set the following UI path to 14 or more character(s): Computer Configuration\Policies\Windows Settings\Security Settings\Account Policies\Password Policy\Minimum password length
4. Recognitions from Regulatory Standards
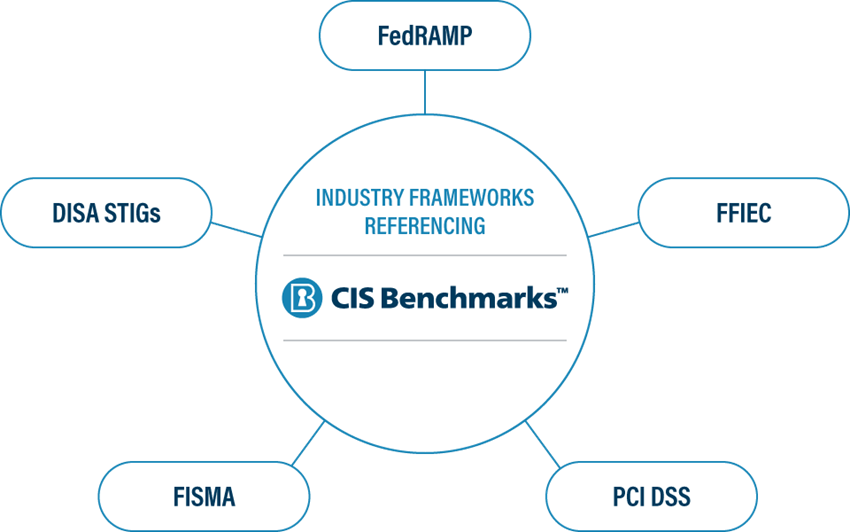
Regardless of your organization's size, you likely need to comply with multiple cybersecurity frameworks and regulatory and legal standards. CIS understands these obligations, which is why its Controls, Benchmarks, and other resources are designed to work as standalone resources as well as companions to help meet compliance with other frameworks and standards. Because the CIS Benchmarks are an industry-recognized hardening standard, many frameworks and standards will reference the guidelines within their documentation as a trusted resource to help meet compliance.
To call out just a few and how they recognize the CIS Benchmarks:
- The DoD Cloud Computing SRG Version 1 Release 3 recognizes the CIS Benchmarks as an acceptable alternative to DISA STIGs.
- NIST’s National Checklist Program Repository recommends the CIS Benchmarks to organizations trying to meet FISMA compliance.
- FedRAMP and PCI DSS refer to the CIS Benchmarks as industry-recognized hardening standards.
For more information, please review these mappings.
How Can You Use a CIS Benchmark?
Using a PDF
You can use the CIS Benchmarks in multiple ways. Anyone can download them free of charge in PDF format for non-commercial use. If you're a CIS SecureSuite Member, you can download the Benchmarks in additional formats such as Word, Excel, and XML via CIS WorkBench.
It's not always quick to manually implement a Benchmark's recommendations using one of the formats discussed above. Some Benchmarks are over 1,000 pages in length and offer hundreds of recommendations. It can be time-consuming to manually implement.
Through CIS SecureSuite Membership
Luckily, there is another option for most CIS Benchmarks. You can use automated assessment content (machine-readable formats of the Benchmarks) with the help of the CIS Configuration Assessment Tool (CIS-CAT). CIS-CAT Lite provides anyone with HTML-based reporting output and access to a limited set of CIS Benchmarks (Microsoft Windows 10, Google Chrome, and Ubuntu Linux). Beyond this free preview, a CIS SecureSuite Member can use CIS-CAT Pro to turn the best practices of more than 80 CIS Benchmarks into actionable insights by scanning their systems and reporting on their levels of compliance.
Accessing CIS Build Kits and CIS Hardened Images
There are two additional CIS offerings to consume CIS Benchmarks recommendations. First, CIS Build Kits are group policy objects (GPOs) for Windows, and Bash shell scripts for Unix and Linux environments to automate hardening systems to CIS Benchmarks standards. This content can save you time and effort when remediating failed settings or recommendations identified in the CIS-CAT Pro report.
Second, CIS Hardened Images are virtual images hardened in accordance with the Benchmarks. They're available in major cloud computing platform marketplaces like Amazon Web Services, Microsoft Azure, Google Cloud Platform, and Oracle Cloud.
Deploying the Tools of Certified Product Vendors
The final way to use a CIS Benchmark is through CIS SecureSuite Product Vendor Member tools. These solutions are helpful in situations where CIS-CAT Pro coverage isn't available for assessments, and they also provide certified offerings for configuration, assessment, and remediation of CIS Benchmarks content.
So, What Are You Waiting for?
There are many factors that make the CIS Benchmarks unique, many opportunities for you to get involved in the Benchmark development process, and many ways to use a Benchmark. All that remains is to figure out a level of engagement and a path that works best for you. You can start by downloading the CIS Benchmarks today.