How CIS Hardened Images Can Help with Cloud Security
Regardless of whether you’re operating in the cloud or on-premises, it's important to harden your system by taking steps to limit potential security weaknesses. Most operating systems (OSes) and other computer applications are developed with a focus on convenience over security. Implementing secure configurations can help harden your systems by disabling unnecessary ports or services, eliminating unneeded programs, and limiting administrative privileges.
By working with cybersecurity experts around the world, CIS leads the development of secure configuration settings for over 100 technologies and platforms. These community-driven configuration guidelines (called CIS Benchmarks) are available to download for free in PDF format.
Want to learn about the community consensus development process powering the CIS Benchmarks? Here’s a video with more information.
CIS Hardened Images Offer Enhanced Security
A single operating system can have over 200 configuration settings, which means hardening an image manually can be a tedious process. Fortunately, you can save yourself some time without undermining your organization's security by using a CIS Hardened Image. CIS Hardened Images are virtual machine (VM) images that are pre-configured to meet the robust security recommendations of the associated CIS Benchmark for that operating system.
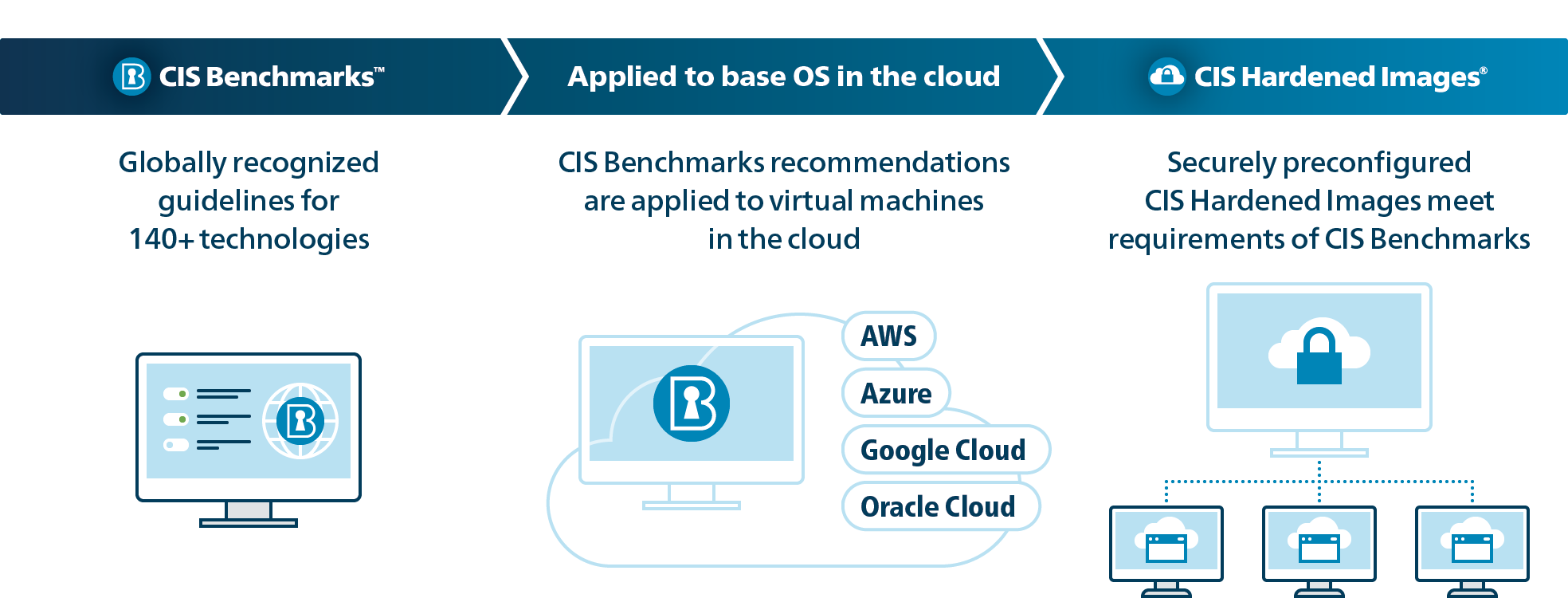
These VMs built to CIS Benchmarks standards can help organizations meet compliance with common frameworks like NIST, HIPAA, PCI DSS, DISA STIGs, and more. For ease of use, CIS categorizes the Benchmarks recommendations into Level 1, Level 2, and STIG CIS Benchmarks profiles. Here’s the difference:
- A Level 1 profile is intended to be practical and prudent, provide a clear security benefit, and not inhibit the utility of the technology beyond acceptable means.
- A Level 2 profile extends Level 1 recommendations and is not a standalone profile. These additional recommendations are intended for environments or use cases where security is paramount. It acts as a defense-in-depth measure, though it may negatively inhibit the utility or performance of the technology.
- The STIG profile is applicable to organizations and industries that require compliance to Security Technical Implementation Guide (STIG) standards. It indicates which existing consensus-based recommendations are applicable to DISA STIG recommendations, and it includes additional recommendations requirements from the STIG not covered in the Level 1 and Level 2 profiles that were agreed upon by the CIS communities.
Benefits of Working with Hardened Virtual Images
According to Google, "a VM is a digital version of a physical computer." It provides the same functionality as a physical computer with the added benefit that users can access it remotely from a variety of devices. Using VMs, or "virtual images" as they're sometimes called, therefore enables you to perform development and testing, run applications, and/or extend a data center with greater flexibility than you could using a physical computer as your organization’s needs change. By removing the need to purchase, set up, and maintain hardware, you can deploy virtual images quickly and focus on the task at hand.
Speed and agility don't remove the need for security, however. Malicious actors can still use virtual images to gain access to sensitive systems and data. Which is why we created CIS Hardened Images. Using the industry-recognized standards of CIS, you can ensure that you fulfill security "in" the cloud under the shared responsibility model, secure your Infrastructure as a Service (IaaS) environments, and overall reduce the number of cyber attacks that leverage your cloud deployments.

How to Get Started
CIS Hardened Images are currently available on AWS Marketplace, Google Cloud Platform, Microsoft Azure, and Oracle Cloud.
Note: This post was originally published June 2017 and has been revamped and updated for accuracy and comprehensiveness.
