Creating Event Trees to Help Measure Control Effectiveness
By Sean Atkinson, Chief Information Security Officer

The transformation of a fault tree
In an earlier blog post, I described using fault trees as a process to understand and attribute mistakes/errors to uncover missing security controls or existing risks to an organization. I used an example fault tree to demonstrate how to diagrammatically define and describe faults and scenarios for their probable realization. To take the next step, let’s transform the fault tree into an event tree. The event tree will help you create mitigation strategies for those faults you wish to control. It’s a helpful strategy for improving your organization’s security posture.
Building an event tree
To start our example, we will use the left side of the event tree in the following diagram:
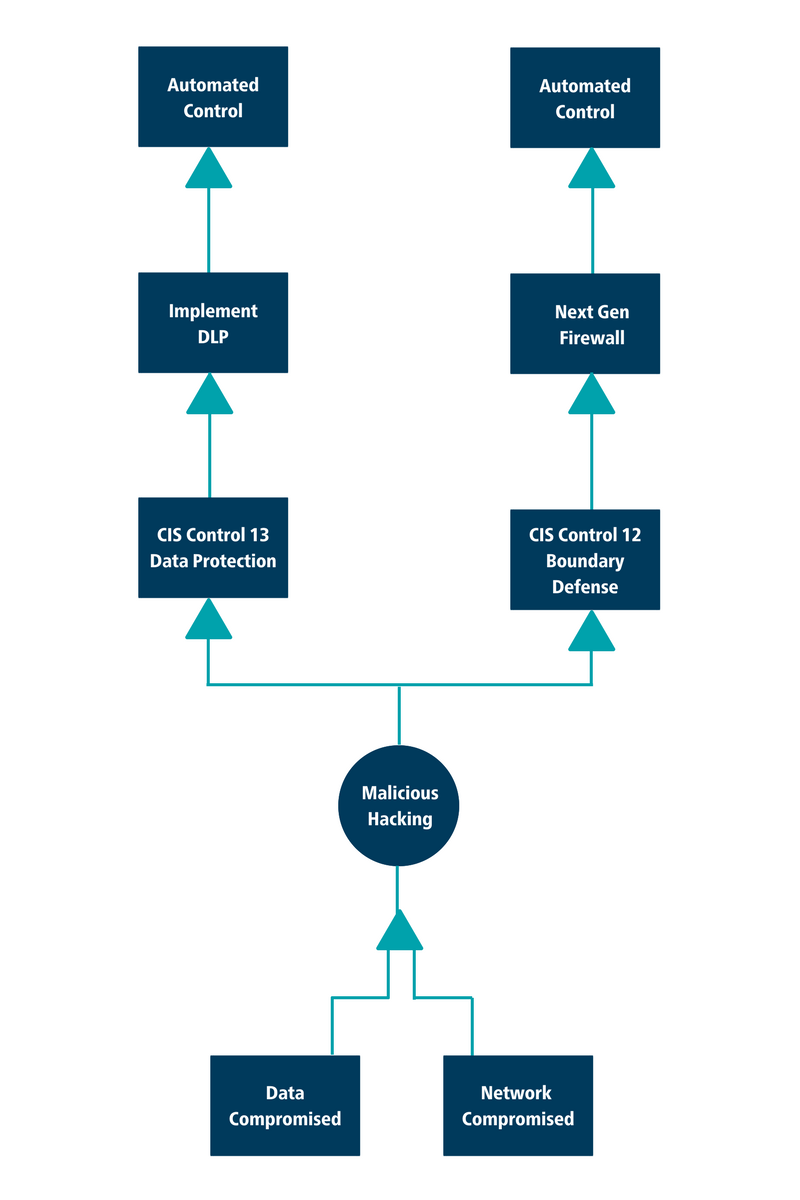
In this example, data from the organization has been compromised due to malicious hacking. There are specific CIS Controls™ which can help prevent such a scenario from taking place and remediate the risk of a data compromise.
Measuring probability
However, because no security control is 100% effective, each organization will need to establish a baseline for the probability of failure. This measurement will have to be gauged over time in order to provide the correct probabilities.
Below is an example set of data protection probability figures:
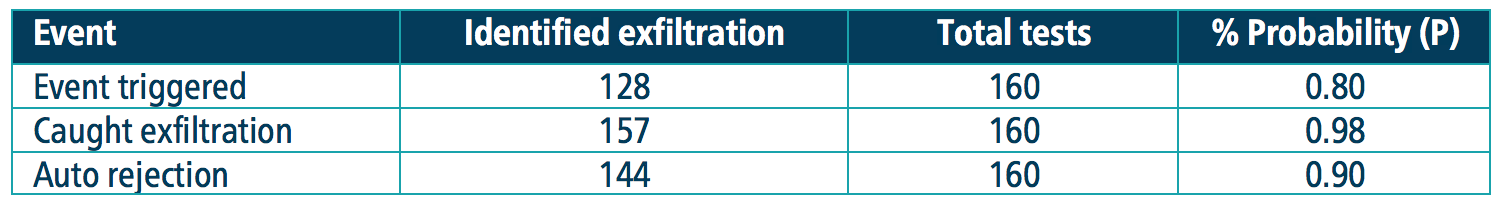
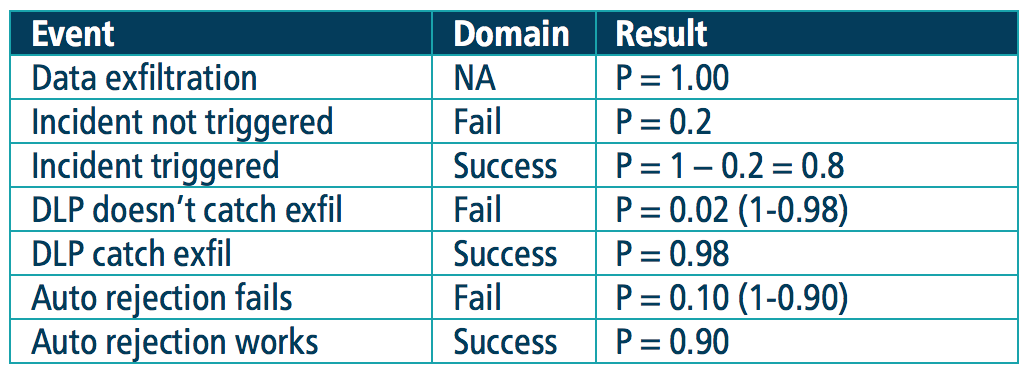
Next, apply the probability to the diagram below to evaluate overall risk.
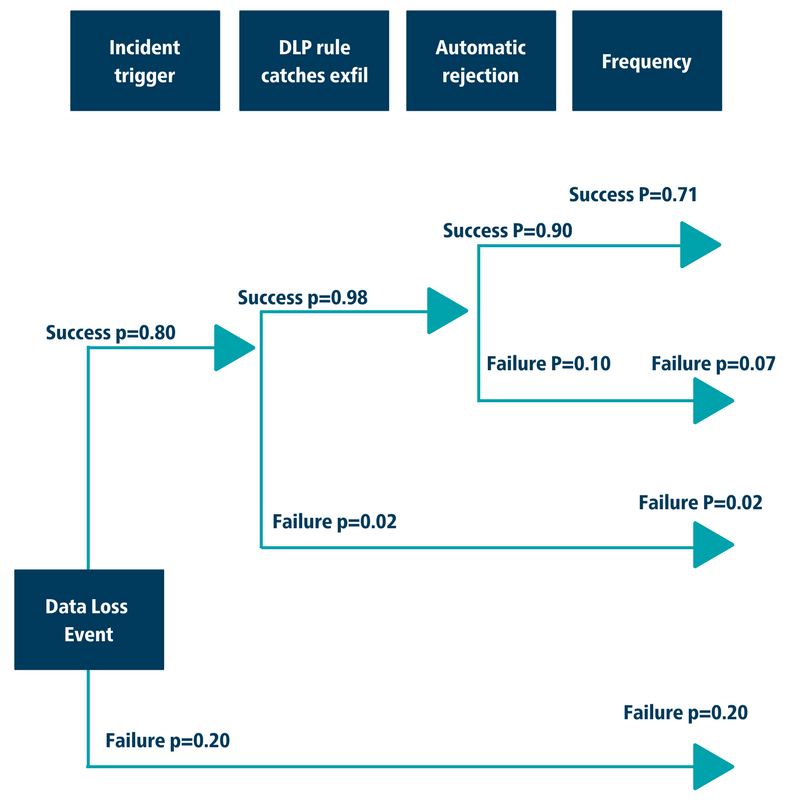
By mapping out the total probabilities, we can see that the organization’s total success probability during the 3-step event is 71% compared to a total failure probability of 29%. From a risk perspective, the company needs to decide, “Are we implementing a strong enough set of security controls to across a particular platform to successfully implement the CIS Control 13 level of data protection?” Each company’s requirements are different, but these types of evaluations will allow for a more stringent review of risk.
Risk and response
The aim of these exercises is to contemplate your organization’s risk and response activities and allow for the review of multiple probabilities to understand risk mitigation strategies and their effective ROI. In a future blog post, I will review the use of such a tool to evaluate the cost-effectiveness of multiple security strategies to make the best business case for leadership-level decision making.
