Sextortion Hoax Scams Continue with Updated Tactics
Sextortion hoax scams continue to affect state, local, tribal, and territorial (SLTT) government employees, who are reporting updated email tactics that make the messages appear more legitimate, increasing the likelihood that employees will believe the emails and fear repercussions. The hoax emails now contain more specific details, including the recipient’s previously exposed email address and associated password, and the supposed timeframe when the recipient’s device was infected with a keylogger. Additionally, open source reporting indicates that cyber threat actors are now incorporating the recipient’s phone number in some sextortion hoax emails.
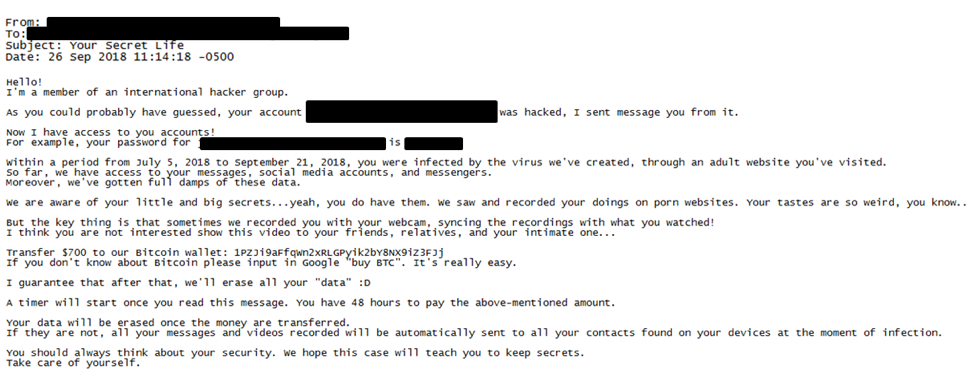
Sextortion emails are a hoax extortion scam, where the cyber threat actor threatens to release compromising material of an email recipient, to their personal contacts, unless an extortion payment is made by the stated deadline. In the emails, the cyber threat actor claims to have infected the recipient with a keylogger that used the recipient’s webcam to record the recipient visiting pornographic websites. The cyber threat actor typically demands the payment in bitcoin, ranging from $100 to $7,000, and includes a bitcoin wallet address to send the extortion to.
Updated Tactics
Previous sextortion hoax emails used generic messages to target a wider audience. The new tactic includes the recipient’s personal information in order to appear more credible and place greater pressure on the recipient to pay the extortion.
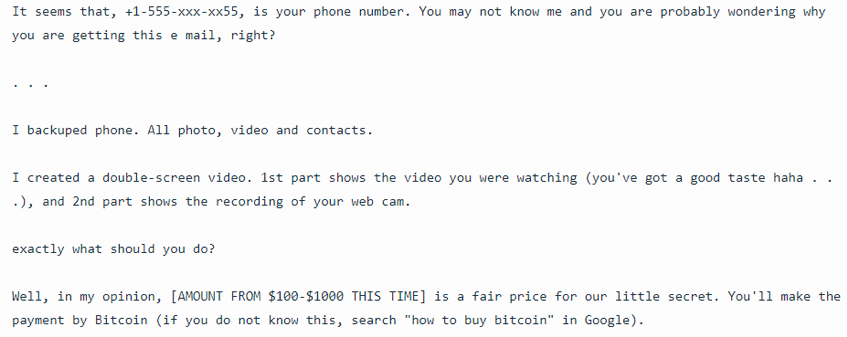
In the first example, below, the cyber threat actor included the employee’s username and password, which were likely from a data breach. In addition to these credentials, the cyber threat actor alleged that the infection occurred between July 5, 2018, and September 21, 2018. In the second example, the cyber threat actor included a portion of the recipient’s phone number. This information was likely accessed through lists that tied email addresses and phone numbers together. Including personal details and a recent timeframe makes these threats more plausible because it includes specific information about the recipient and the attack.
Recommendations
Due to the threats included in these sextortion hoax emails, SLTT governments are strongly encouraged to ensure users are aware of these hoaxes and that networks and systems are protected through the following recommendations. Refer to the MS-ISAC blog post on Hoax Extortion Scams for more information on protecting against hoax extortion scams.
Before receiving a hoax email:
- Train employees to recognize and report sextortion hoaxes. Urge them to not open suspicious emails, click links contained in such emails, post sensitive information online, and never provide usernames, passwords and/or personal information to any unsolicited request.
- If necessary, create policy and procedures for reporting and handling phishing emails for your organization.
- Ensure that the work culture is such that employees feel safe reporting incidents, as some employees’ state they do not report these scams due to a fear of a cybersecurity investigation into their workstation.
- Apply all vendor patches after appropriate testing.
- Implement spam filtering at the email gateway to filter out emails with known phishing indicators, such as the known malicious subject lines.
- Verify that proper account lockout policies are enforced to reduce the success of brute force attacks. The MS-ISAC recommends locking accounts after no more than 5 failed login attempts, as well as logging and notifying on successive login attempt failures.
- Block suspicious IP addresses at the firewall.
- Apply the Principle of Least Privilege to all systems and services.
- Adhere to best practices, such as those described in the CIS Controls™ and the CIS Benchmarks™ programs.
Upon receiving a hoax email:
- Report these attacks to the MS-ISAC, at [email protected], and to the Internet Crime Complaint Center (IC3).
- Reset passwords for all affected users.
- Run an antivirus scan using updated signatures on the machine suspected of being infected with a keylogger and reimage if appropriate.