Jupyter: A Cyberspace Invader Stealing SLTT Data
Executive Summary
The Multi-State Information Sharing and Analysis Center (MS-ISAC) Cyber Threat Intelligence Team (CTI) assesses with moderate confidence that Jupyter, a highly evasive and adaptive .NET infostealer, will continue to opportunistically target state, local, tribal, and territorial (SLTT) organizations. Cyber Threat Actors (CTAs) have deployed Jupyter widely, leveraging SEO-poisoning to create watering hole sites, increasingly infecting SLTT entities since September. Recommendations to better secure your organization are at the end of this report.
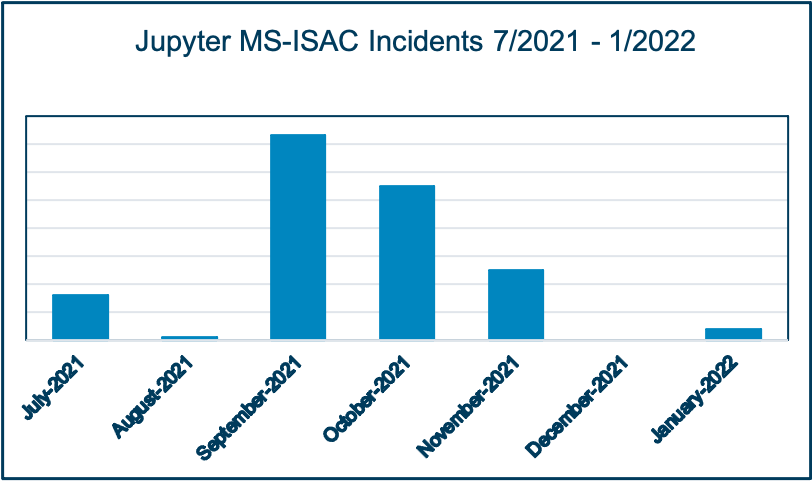
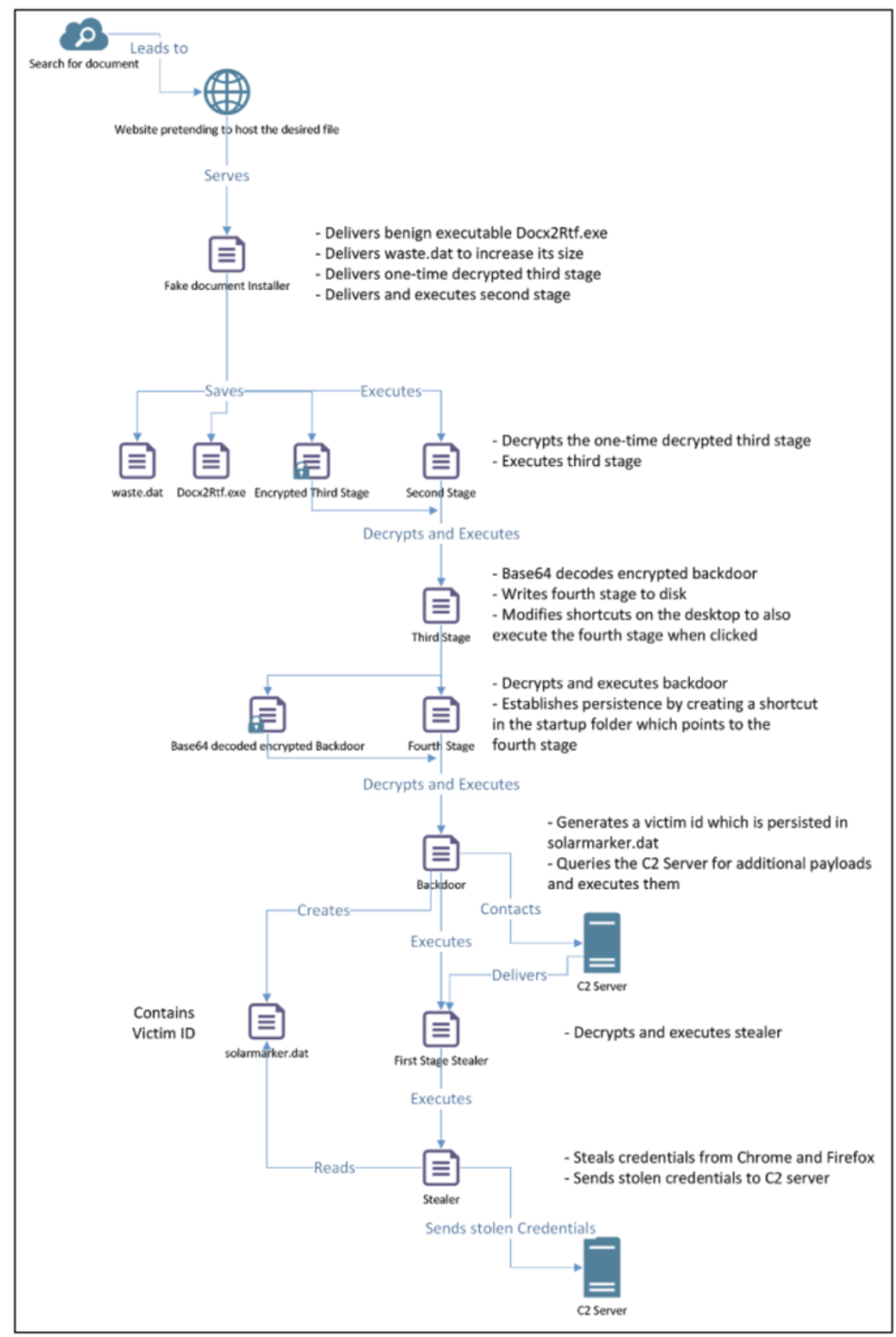
Jupyter (aka SolarMarker) deploys a multi-stage process, leveraging PowerShell and legitimate tools, such as Slim PDF Reader, to drop secondary payloads to fingerprint victim information, including computer name, OS version, architecture, permissions, and user identifier.1 Jupyter is likely impacting SLTTs as part of a broader opportunistic effort, since the malware is affecting an array of sectors, including finance, healthcare, and education.2 Following aspike in activity during the fall, SLTT-Jupyter infections subsided with no incidents in December and a small resurgence through this past month.
Substantive Analysis
The MS-ISAC determined SLTT victims became aware of infections when their endpoint detection and response services (EDR) alerted on unauthorized PowerShell commands attempting to communicate with command and control (C2) traffic. The MS-ISAC continues to investigate why Jupyter operators are harvesting victim information, granting CTAs commonly leveraged infostealers for financial gain and intellectual property theft. Security researchers have observed the Jupyter operators adapting their techniques, tactics, and procedures (TTPs) and malware frequently, so intrusion details are likely to vary across infections.
Despite the irregularity in Jupyter TTPs, several features are common among public-sourced and MS-ISAC-observed breaches. Prior to infection, the Jupyter operators inject over 2,000 keywords to push malicious Google and WordPress3 sites up search engine rankings, using a technique known as SEO-poisoning,4 thereby increasing the likelihood that an unsuspecting user will visit the page. Analysis of an SLTT Jupyter incident revealed that the initial infection occurred after an end-user attempted to download a malicious file embedded with an executable off a compromised website form. The malicious documents will often feature an unassuming name, such as ‘Assignment-Of-Proprietary-Lease-Form-.exe’ to lure users into interacting with it. The installer launches the malicious executable and then Nitro Pro 13 will execute an over 100MB MSI payload, allowing it to bypass antivirus software due to file size limitations.
All observed attacks have shared the objective of harvesting and communicating victim information, including from BIOS and browser, to a C2 address. Appendix “Figure 2” depicts Jupyter’s commonly observed four-stage infection chain, starting with the web-hosted malicious executable.
Indicators of Compromise5
Jupyter frequently shifts infrastructure, so the below-listed IPs may not be active. Organizations are encouraged to leverage these IOCs for threat hunting.C2 IPs
104.223.123[.]7
146.70.24[.]173
185.244.213[.]64
37.221.114[.]23
45.42.201[.]248
37.120.237[.]251
Filepaths
AppData\Roaming\Microsoft
AppData\Local\Temp\ .\Users\’username’\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
.\Users\’username’\AppData\Roaming
.\Users\’username’\Downloads
Targeted File Types
<randomly generated>.lmk
<randomly generated>.cmd
<randomly generated>.ps1
Abused Native Applications
Docx2rtf.exe
<randomly generated>.ps1
AlienVault Hashes
39B0E2965DAF855FBD25FACBDD0DCB84E3A2103D0AC37699B27284DD918DFCB7
1F034E91613AB7C290D172B87200A000365728F218CBD4491F59D09A20BFD866
8C35F2A78E366ABF2450D5882C49C69EE5CC01DBA3743938B45CEDC2B5DEE3A3
E34AF1B6EDF33B155CA9854D084577C30E1BC9D96EEE10014277A0E55A47BEEF
BC7986F0C9F431B839A13A9A0DFA2711F86E9E9AFBED9B9B456066602881BA71
934CB210DB692C3EBCD9BA8D113B1669573A20DB79C02A2587A4BEAD10D8DFEB
8E06C31285911C936425921CCF9F20107160174ACD602CC7F2DD8CA677E8956D
8BCF6506B21F67641FA753D7328D3C1045541F84BC62BBE43D485F38E3D5E3AE
8447B77CC4B708ED9F68D0D71DD79F5E66FE27FEDD081DCC1339B6D35C387725
2524CEA17B8EC62D30A93751FC42CC4E33350CAAFF5BA9A2327C048B715B2D4A
1197067D50DD5DD5AF12E715E2CC00C0BA1FF738173928BBCFBBAD1EE0A52F21
F6AA48BC45BE3B603A48A5261A28CC75E9C1C2F65AA37BB807B6C1BD80DCE05A
E466158FF4C6DA37213DC9E0F05038D05EBEAD93FEBF51A5EC3AC6E2B9E3E22D
9E3B4E4948521467216515E92812E5A47FB23F5BCB3A8B1A6014AE2F038C7181
8BD8FA4A5500D390D69941CB5D89A568D46D49BC4AC731A6C548B7D8E69625C2
88748AAE11029228D84AEF0855F4BC084DFD70450DB1F7029746D8BC85182F93
1D90B6C3B59A4287697C81A10EA950BDA9326AF8B629EF59C8B5BDE3A7486683
1C5082CB7FBD011FEB14909320B163B038FEBED29700568F9A2C7B5A416FAD51
A3322F7C7B28EDE324BBC652FBE30E49F1737F49
55A5180ADB6044D6A5B9A0ED039A3EB0
MITRE ATT&CK Patterns Observed6
Execution
T1059.001 Command and Scripting Interpreter: PowerShellDefense Evasion
T1027 Obfuscated Files or InformationT1218.007 Signed Binary Proxy Execution: Msiexec
Discovery
T1083 File and Directory DiscoveryT1082 System Information Discovery
T1033 System Owner/User Discovery
Collection
T1005 Data from Local SystemCommand and Control
T1071 Application Layer ProtocolExfiltration
T1041 Exfiltration Over C2 Channel
Analytic Confidence
Analytic confidence in this assessment is moderate. Source reliability is moderate with several conflicts among sources, the CTI team attributes to Jupyter’s evolving tactics and infrastructure, as well as variation across security researcher methodology. The analyst used a Circleboard, Timeline, and Key Assumptions Check to perform this analysis.
For questions or comments, please contact us at [email protected].
Recommendations
- Malicious Domain Blocking and Reporting (MDBR):7a service available to SLTTs to help prevent systems from resolving malicious DNS requests. It provides an additional layer of protection by blocking known bad domains and is proven, effective, and easy to deploy.
- CIS Endpoint Security Services (ESS):8 a host-driven security solution available to SLTTs that is designed to help mitigate and prevent malicious files from executing on covered systems.
- Network Intrusion Detection (NID): 9 MS-ISAC’s NID, Albert Network Monitoring and Management, provides signature-based security alerts for both traditional and advanced network threats, helping organizations identify malicious Jupyter activity leveraging known TTPs and IOCs.
- Application Allowlists:10 recommended under CIS Critical Security Control 2 to help organizations actively manage (inventory, track, and correct) all software on the network so that only authorized software is allowed. Allowlist restrictions can prevent Jupyter from leveraging internal tools to drop additional payloads.
References
- https://www.morphisec.com/hubfs/eBooks_and_Whitepapers/Jupyter%20Infostealer%20WEB.pdf
- https://www.menlosecurity.com/blog/holy-seo-poisoning/
- ibid
- https://otx.alienvault.com/pulse/614b28d3e2d3e29b57c77127
- https://www.cid.army.mil/assets/docs/2can/SEOPoisoning.pdf
- https://blog.talosintelligence.com/2021/07/threat-spotlight-solarmarker.html
- https://www.cisecurity.org/ms-isac/services/mdbr/
- https://www.cisecurity.org/services/endpoint-security-services/
- https://www.cisecurity.org/services/albert-network-monitoring/
- https://www.cisecurity.org/controls/inventory-and-control-of-software-assets/
- https://www.crowdstrike.com/blog/solarmarker-backdoor-technical-analysis/
Appendix