How to Implement & Assess Your Cyber Hygiene
Just like physical hygiene keeps us healthy and protects us from common germs, cyber hygiene is important for protecting your organization from common cyber threats. Implementing cyber hygiene security best practices is the CIS-recommended way to help prevent data breaches, system misconfigurations, and more. But what exactly does cyber hygiene entail? This blog post will highlight the development process for establishing a cyber hygiene program and help identify a program that works for your organization. These cyber hygiene security guidelines are adapted from the CIS Controls V7.1. The CIS Controls are a free, internationally-recognized set of cybersecurity best practices. They’re known for bringing together expert insight about threats, business technology, and defensive options. They provide an effective and simple way to manage an organization’s security improvement regime.
Developing cyber hygiene guidance
Measuring your organization against a security best practice, such as the CIS Controls, will help you take stock of your cybersecurity health. CIS Controls V7.1 helps organizations prioritize their cybersecurity activities with the introduction of Implementation Groups (IGs). The IGs provide a simple and accessible way to help organizations classify themselves as belonging to one of these IGs to focus their security resources, expertise, and risk exposure while leveraging the value of the CIS Controls program, community, complementary tools, and working aids.
To develop the IGs, CIS took a “horizontal” look across all of the CIS Controls and identified a core set of defenses that organizations with limited resources and limited risk exposure should focus on. We call these accessible and high-value Sub-Controls IG1 or cyber hygiene. They provide effective security value with technology and processes that are generally already available while providing a basis for more tailored and sophisticated action if warranted. Building upon IG1, CIS identified an additional set of Sub-Controls for organizations with more resources and expertise, but also greater risk exposure. These more advanced security techniques form the second Implementation Group (IG2). Finally, the remainder of the CIS Sub-Controls makes up IG3. Watch this short video to learn more:
Staying fresh with cyber hygiene
Helping adopters of the CIS Controls implement cyber hygiene is important to us, so we created a page to allow cybersecurity professionals to explore the CIS Controls at the Sub-Control level – check it out here. The release of V7.1 introduces our Implementation Group (IG) methodology that will enable you to decide which IG is for your organization. With this tool, you can filter by IG, and then add additional CIS Sub-Controls based on your organizational needs. Be mindful of the following attributes: data sensitivity, technical expertise of staff, and available resources for cybersecurity which are the CIS-recommended attributes for choosing your IG. Start with IG1 and work your way up to IG2 or IG3. Export your selection to the desired format once you have completed your selections.
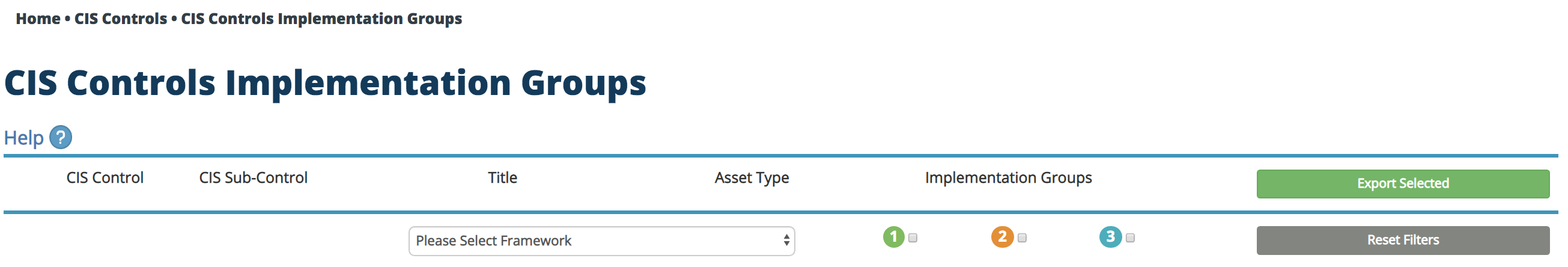
Additional filtering features include regulatory framework mappings for the NIST Cybersecurity Framework (CSF) and ISO 27001 where you can tie the IGs into your report. We hope to add more mappings in the coming months. If there’s a framework that’s important to you and your organization, please let us know by emailing [email protected] and we’ll add it to the queue of mappings.
Security for every organization
At home and in the workplace, cyber hygiene is an important best practice for keeping our systems and data secure. Just like washing our hands and brushing our teeth, using strong passwords and known Wi-Fi networks is something everyone should do. The CIS Controls have always provided best practices for organizations to defend their cyber assets. The development of Implementation Groups helps organizations and enterprises from around the world:
- Bolster their organization’s security
- Create cybersecurity programs on a budget
- Implement best practices regardless of cyber expertise
- Defend systems and data with limited resources
Find out where your cyber hygiene stands by downloading the CIS Controls and assessing against Implementation Group 1 today.