Cyber Hygiene Guidance for Windows 10
 According to both Net Applications and Stat Counter, all versions of the Microsoft Windows operating systems combined represent well over 50% of all worldwide operating system (OS) usage. That same data shows that Windows 10 has the lion’s share of the market. This is great for security as Microsoft’s support for Windows 7 is drawing to a close in January 2020.
According to both Net Applications and Stat Counter, all versions of the Microsoft Windows operating systems combined represent well over 50% of all worldwide operating system (OS) usage. That same data shows that Windows 10 has the lion’s share of the market. This is great for security as Microsoft’s support for Windows 7 is drawing to a close in January 2020.
CIS is dedicated to offering practical guidance on cyber hygiene to Windows 10 users. To that end, our new resource, the CIS Controls Microsoft Windows 10 Cyber Hygiene Guide, is now available. While many versions of Windows are available, Windows 10 Pro is the primary edition of the Windows 10 operating system discussed within our guide. Read on to learn more about cyber hygiene and the role it can play in securing Windows 10.
What is cyber hygiene?
Cyber hygiene is often viewed as a set of baseline cybersecurity protections that help to secure an organization. CIS Controls Version 7.1 contains industry-developed cybersecurity best practices against the most common attacks seen in the wild. The protections outlined in 43 of the CIS Sub-Controls makeup Implementation Group 1 (IG1), and form the baseline of cyber hygiene. Tactics for implementing the CIS Controls can vary depending on which technology your organization is using. That’s why we developed a guide just for Windows 10.
We developed the CIS Controls Windows 10 Cyber Hygiene Guide to make cybersecurity basics for this particular technology easier to follow. The guide provides practical step-by-step assistance for securing computers running Windows 10 without the need for advanced technical knowledge. It is targeted to organizations concerned with stopping the theft of company information, website defacement, phishing attacks, ransomware, and data loss – just to name a few!
 Download CIS Controls
Download CIS Controls
Overcoming cybersecurity configuration challenges
Putting a new CIS Control or Sub-Control into place within an enterprise network can be a daunting task, regardless of the size of the organization. The guide is structured to help ease that effort. Each cyber mitigation discussed within the guide includes a detailed explanation to assist with implementation.
As organizations expand and implement more sophisticated cybersecurity technology, automation is often an important consideration. Because of this, the automatability for each Sub-Control in the guide is explored. This way organizations can focus on learning and implementing technologies that can have a broad impact for years to come.
Finally, additional guidance and tools from CIS and other organizations are highlighted. To the extent possible, we recommend open source or free tools, and guidance from non-profits and government entities.
Step-by-step instructions to configure Windows 10
With simplicity and ease of use as the governing principles for this document, detailed step-by-step instructions are provided for Windows 10. As there are often multiple ways of accomplishing the same task on Windows, approaches are provided from both the Control Panel and the more technical Local Group Policy Editor. Using either method, screenshots are presented to guide users and show each mouse click necessary to implement a security measure.
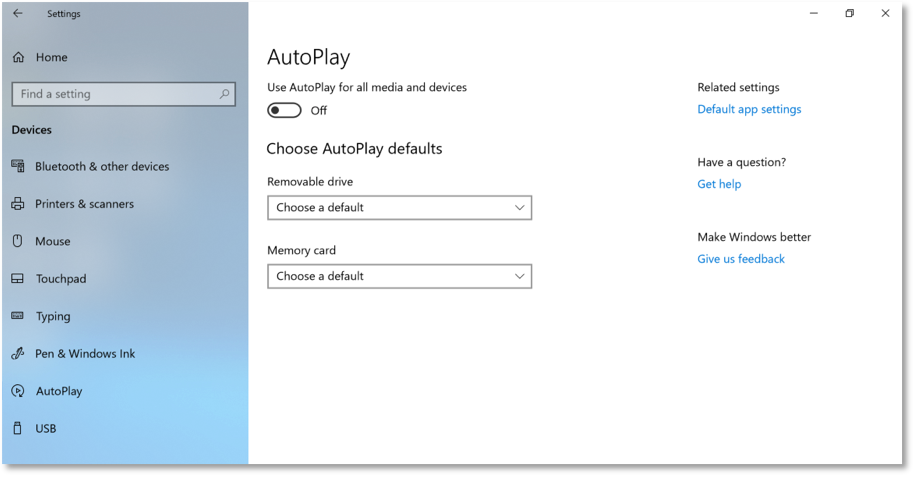
For instance, AutoPlay can be useful, but it is also a potentially dangerous setting if improperly managed. Here are the steps from the guide for ensuring AutoPlay on Windows 10 is disabled:
1. Navigate to the Windows Settings Panel and select Devices.
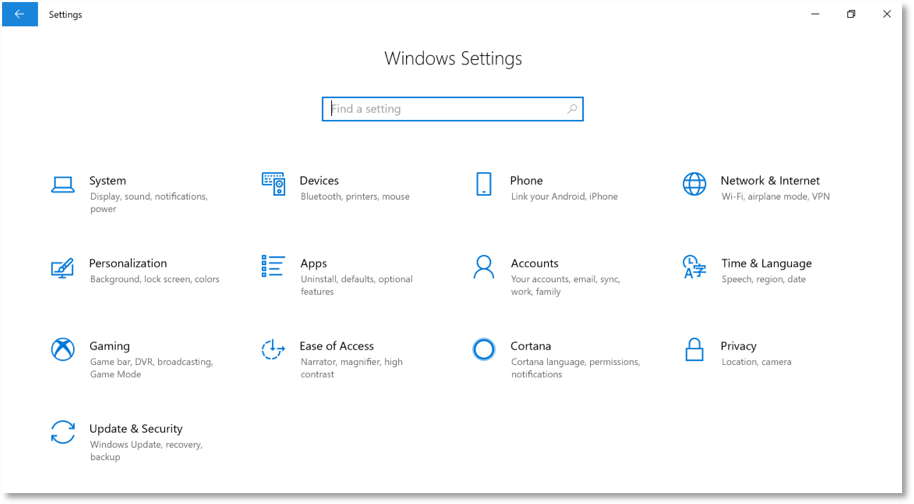
2. Select Autoplay in the bottom left.
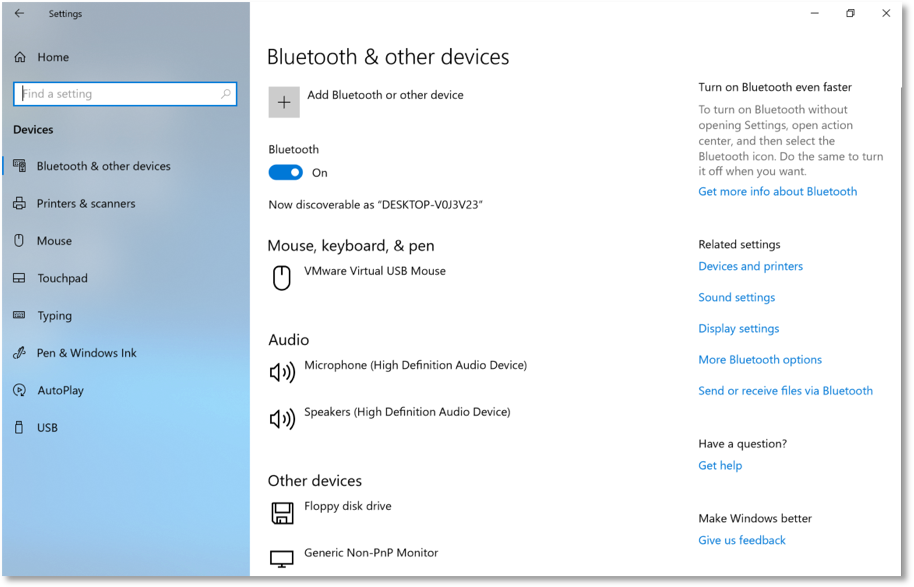
- Ensure AutoPlay is set to Off.
Securing the future with Implementation Group 1
All individuals and organizations should be able to protect themselves against cyber threats, regardless of their size or level of IT expertise. To that end, CIS created Implementation Group 1 and the Windows 10 Cyber Hygiene Guide to lower the barriers of practicing cyber hygiene. The 43 IG1 Sub-Controls are a mixture of technical and procedural recommendations that should be prioritized first. They are designed to be inexpensive and not to interfere with how you use your systems. Starting implementing them today!