Fault Trees and Risk Forests
By Sean Atkinson, Chief Information Security Officer
Risk management and the elicitation of scenarios
 Over the past few blog posts I have discussed and reviewed strategies for contingency, governance structures, and risk conversations. When starting a risk-focused discussion, gather the appropriate stakeholders and be sure to focus on forecasted expectations and what should occur in your organizations if those expectations fail to meet the forecast.
Over the past few blog posts I have discussed and reviewed strategies for contingency, governance structures, and risk conversations. When starting a risk-focused discussion, gather the appropriate stakeholders and be sure to focus on forecasted expectations and what should occur in your organizations if those expectations fail to meet the forecast.
Use the following concepts to build a risk elicitation questionnaire, interview, or peer review:
- Risk triggers – Questions to review the underlying assumptions of currently-held beliefs
- Scenarios based on the triggers – Diagrammatic examples that will require weighted responses to a risk scenario
Building a fault tree
Use the questionnaire responses to begin to build a fault tree to see where risks to the organization are greatest and how you might respond. Start building the fault tree using a specific high-level event, then determine the responses to risk using weighted examples. The example in the diagram shows potential responses to malicious hacking. This scenario is used to determine whether the data within the organization is the most likely to be compromised or if the systems would be the most likely target.
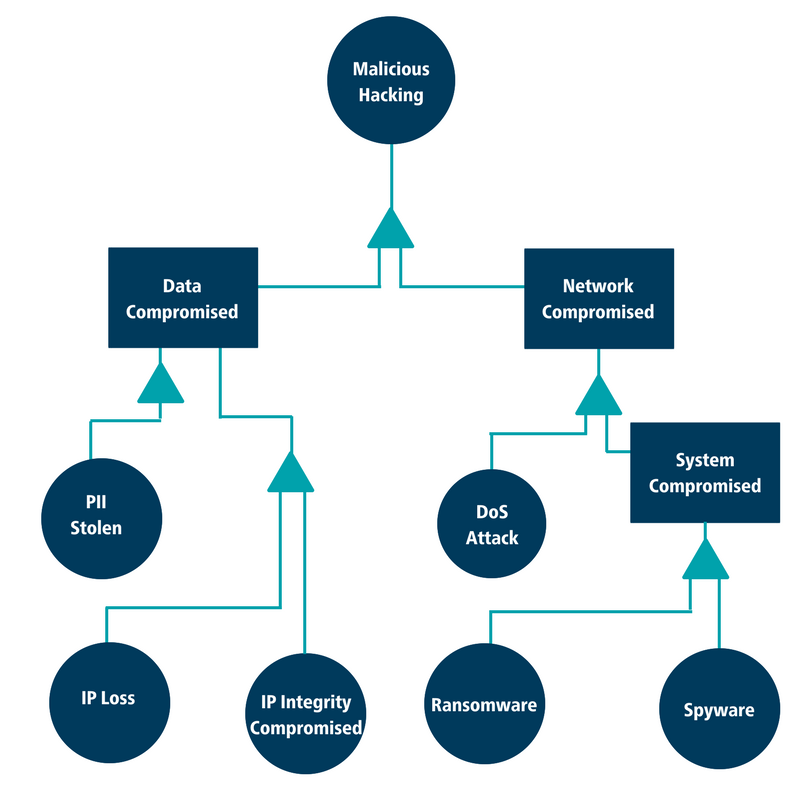
Given this analysis we can then look at the corresponding events that would lead the organization to the main outcome of malicious hacking. To build the tree, entertain multiple scenarios of how the main top-level event could occur. In this tree we have restricted the number of potential leading events for brevity.
Responding to risk
After you’ve built out your fault tree it’s time to consider how your organization will respond to potential risk. If the data stolen is PII (personally identifiable information) such as phone numbers and home addresses, what is the duty of care to inform those whose data was stolen? If the data was IP (intellectual property), what is its value to the organization and how much was taken? These questions will put you on the journey to incident response and implementing protective controls for data loss prevention as mitigation strategies for risk.
As you move from outcomes to causes in the diagram, your organization can:
- Evaluate existing controls and risk management processes
- Determine the organization’s current risk posture
- Strategize about the future implementation of controls based on the likelihood and probability of compromise in the event of a data breach or technical failure.
To greater improve your cybersecurity posture, consider developing multiple control scenarios for each event. You may want to follow existing best practices like the CIS ControlsTM or frameworks such as NIST CSF to help guide your implementation of security controls. To determine the best strategy for a set of controls you can employ techniques to evaluate the risk-reduction ROI as well as a review of measuring the effectiveness of the control, a topic for a future blog post.
